HOSTS File Protection
SpyHunter 5 includes advanced features to protect your Windows HOSTS file from unauthorized tampering.
The HOSTS file is used by Windows to map domain names to IP addresses. When resolving a domain name, the HOSTS file is checked before your service provider's DNS servers are queried.
A malicious object can surreptitiously write an entry to your HOSTS file to transparently point a trusted domain name (such as www.enigmasoftware.com) to a malicious server that is in no way affiliated with the actual domain name. This opens the door to unauthorized access to your personal data, phishing activities and other potential confidence scams which may seriously compromise the security on your PC. Fortunately, SpyHunter 5 offers a tool designed to help prevent this from occurring.
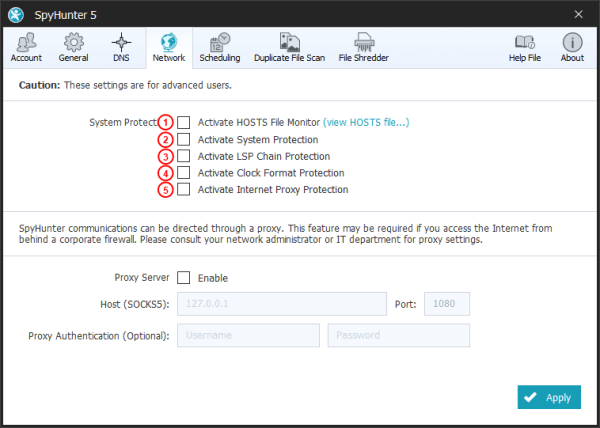
Within the Network tab, at the right of the "Activate HOSTS File Monitor" checkbox, SpyHunter 5 provides a "View HOSTS file..." link that will display the contents of your Windows HOSTS file.
To activate the HOSTS File Monitor, select the "Activate HOSTS File Monitor" (1) checkbox from the "Network" tab in SpyHunter 5's "Settings."
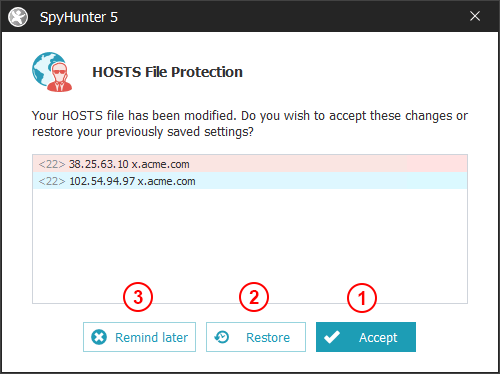
When the "HOSTS File Monitor" is active, SpyHunter 5 monitors your HOSTS file for any additions, deletions, or modifications. When SpyHunter 5 detects a change in the HOSTS file, it will alert you with a dialog window, displayed below, where you will have the option to allow or prevent the changes via the "Accept" (1) and "Restore" (2) buttons. If you cannot decide on an appropriate course of action at the moment, you can click on the "Remind Later" (3) button.