APT28
 The world of cyber crime is not just about hackers and bad actors who are out for a quick buck, spreading around phishing spam emails. There is a different kind of threat actors that go beyond for-profit ransomware or annoying viruses. Those groups are usually called Advanced Persistent Threat actors, or APTs.
The world of cyber crime is not just about hackers and bad actors who are out for a quick buck, spreading around phishing spam emails. There is a different kind of threat actors that go beyond for-profit ransomware or annoying viruses. Those groups are usually called Advanced Persistent Threat actors, or APTs.
The biggest difference between an APT and a group of hackers spreading malware is that an APT is most commonly a state-sponsored organization, whose actions are usually used to infiltrate high-profile, often government networks, and extract sensitive or confidential information. The "persistent" part of the definition implies that the actors in the group have defined, long-term objectives and are not just looking for hit-and-run monetary gains, keeping a low profile for as long as possible to avoid detection.

Assuming an APT is backed by an official state authority, the resources available to the group will also be much greater than what most cybercriminal organizations can muster.
The numeric identifier given to different APTs is just convenient shorthand for security researchers to talk about them without mentioning their entire aliases, of which there are often many.
The APT28 (Advanced Persistent Threat) is a hacking group that originates from Russia. Their activity dates as far back as the mid-2000s. Malware researchers believe that the APT28 group’s campaigns are funded by the Kremlin, as they usually target foreign political actors. The APT28 hacking group is best known as Fancy Bear, but it also is recognized under various other aliases – Sofacy Group, STRONTIUM, Sednit, Pawn Storm and Tsar Team.
Table of Contents
The Infamous Hacking Campaigns Carried Out by Fancy Bear
Experts believe that the Fancy Bear had a hand in the 2016 Democratic National Committee hack, which some believe had some influence on the outcome of the Presidential Elections taking place the same year. During the same year, the Fancy Bear group also targeted the World Anti-Doping Agency because of the scandal involving Russian athletes. The data that Fancy Bear obtained was then published and available publicly. The data revealed that some of the athletes who tested positive for doping were later exempted. The report of the World Anti-doping Agency stated that the illicit substances were meant for ‘therapeutic use.’ In the period 2014 to 2017, the Fancy Bear group was involved in various campaigns targeting media personalities in the United States, Russia, Ukraine, the Baltic States and Moldova. Fancy Bear went after individuals working in media corporations, as well as independent journalists. All the targets were involved in the reporting of the Russia-Ukraine conflict that took place in Eastern Ukraine. In 2016 and 2017, Germany and France had major elections, and it is likely that the Fancy Bear group dipped their fingers in these pies too. Officials from both countries reported that a campaign using spear-phishing emails as infection vectors took place, but they stated that there were no consequences of the hacking attack.
The image below is a demonstration path that APT28/Fancy Bear utilizes to carry out its cyber intrusions against certain targeted systems. The U.S. Government has confirmed such actions of intrusion into the polity party from the first actor group, APT29 in 2015, and then the second, APT28, into 2016.
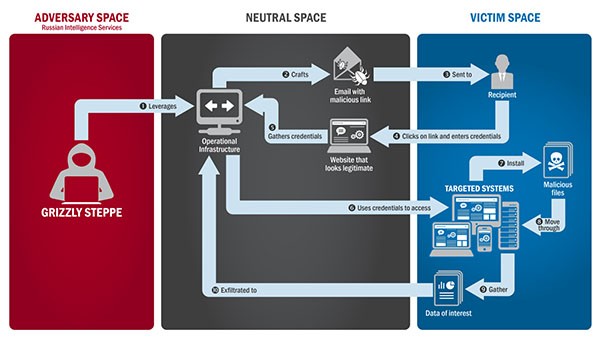
Diagram demonstrating the actions and processes of APT28/Fancy Bear's spear-phishing techniques and intrusions against targeted systems - Source: US-Cert.gov
Fancy Bear’s Tools
To evade the prying eyes of cybersecurity researchers, the Fancy Bear hacking group makes sure to alter their C&C (Command and Control) infrastructure regularly. The group has an impressive arsenal of hacking tools, which they have built privately – X-Agent, Xtunnel, Sofacy, JHUHUGIT, DownRange and CHOPSTICK. Often, instead of direct propagation, Fancy Bear prefers to host its malware on third-party websites, which they build to imitate legitimate pages to trick their victims.
Fancy Bear also employ advanced obfuscation techniques that help them avoid detection for as long as possible. The group started adding junk data in their encoded strings, making it very difficult to decode the information without the specific algorithm to remove the junk bits. To further hinder security researchers, APT28 also resets the timestamps of files and regularly cleans event logs to make tracing malicious activity more difficult.
Fancy Bear is one of the most ill-famed hacking groups, and there are no indications that they will halt their campaigns any time soon. The Russian government is known to use the services of hacking groups, and Fancy Bear is one of the highest-tier hacking groups out there.
German Accusations Against Alleged Members of APT28
In June 2020, the German Foreign Ministry informed the Russian ambassador in the country that it will seek "EU sanctions" against Russian citizen Dmitriy Badin. German authorities believe him to be connected to Fancy Bear / APT28 and claim to have evidence that he was involved in a 2015 cyber attack on the German parliament.
Russian Foreign Ministry spokesperson Ms. Zakharova called the allegations "absurd" and firmly dismissed them, underlining her belief that the information German authorities used was coming from US sources. She also urged German authorities to provide any proof of Russian involvement in the attack.

