Are You Sure You’re NOT Infected with Malware?
Don’t Fall Victim to Malware or Ransomware Attacks!
Detect and remove malware, viruses, ransomware & other threats for FREE! Get Protected with SpyHunter.
Download SpyHunter (FREE Trial!)*An Advanced Persistent Threat (APT) is a computer threat actor, most often operated or sponsored by nation-states. The aim of these groups aims at unauthorized access to computer networks for extended periods. The term may also be used for large-scale intrusions with specific targets in more recent cases.
The motivations behind threat actors of that level are most often political or economic. Major business sectors saw attacks by APTs with theft, spying, or disruption in mind. The affected sectors spanned defense, legal services, financial services, government, telecoms, industrial, and consumer goods, among others. Some of the groups with this concept in mind work with the more traditional steps, social engineering, infiltration, and intelligence efforts to gain physical access to networks. These attacks are performed to place malicious code on multiple computers with specific tasks in mind.
The exact nature of an APT might vary, but the details and requirements remain the same:
Advanced – Meaning the operators behind the APT have a wide range of intelligence gathering capabilities to work with. Commercial and open-source intrusion techniques and technologies, intelligence gathering through state-operated means, and more may be a part of the APT’s arsenal. Although the attack’s elements may not be advanced, meaning that some of the components may be easy to exploit or find, the operators usually have access to advanced tools. Many APTs have either access to such tools or are capable of developing them within their organizational structure. Techniques and targeting methods are combined to maximize the compromise of a targeted individual or organization to slip through defenses and to maintain access over a long time. The professionalism exhibited by operators of this level shows a specific focus on operational security that separates them from the average hacker into a league of their own.
Persistent – The operators have a set of objectives to aim for, instead of just reaping information for financial gain. The difference is that these attackers are guided by the idea of monitoring, interaction, and action to achieve a clearly defined objective. That does not mean a set of constant attacks or malware updates; their work is often more insidious and slow. If the APT loses access to their target, they might attempt to gain access again, instead of moving on. One of the long term goals of an operator of this kind is to have unobstructed access to their target, contrasting to threats that aim at a variety of victims.
Threat – APTs are a threat because of their intent and advanced capabilities. Their attacks are performed by human intent, rather than automatically through the use of code. Their targets are specific and chosen through research and intelligence gathering. APTs are groups with skill, motivation, organization, and funding, backed by either states or other powerful groups.
Advanced Persistent Threats: What Are They, Really? – Source: DarkReading.com
Cases of targeted and socially engineered emails dropping Trojans to exfiltrate data were seen, and warnings were given by CERT organizations in the UK and US as far back as 2005. The method was popular in the 1990s, but it did not bear the name given today. The term ‘Advanced Persistent Threat’ was cited as used by the United States Airforce in 2006. It was Colonel Greg Rattray, who is accepted as having used the term for the first time.
There were many sources observing attacks that were likely affiliated with, or even acting as agents of sovereign states. Businesses with a high capacity of personally identifiable information have been at a high risk of being targeted by APTs. Examples of attacks could be seen in agriculture, telecommunications, technology, energy, transportation, manufacturing, financial institutions, higher education, and healthcare providers.
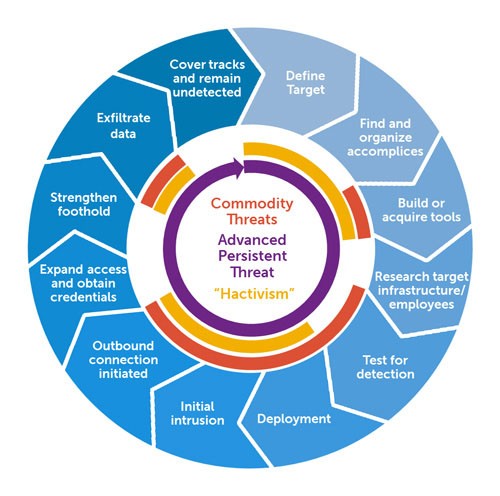
Advanced Persistent Threat Lifecycle – Source: Secureworks.com
APT attacks may be broken down into stages, to understand better the way these threat actors operate in the digital world. The first step begins with:
APT targets are usually infiltrated through the compromise of one of three ways: network resources, web assets, or authorized users. That is most often achieved through the use of several techniques. Malicious uploads are used with RFI and SQL injections, social engineering attacks such as spear phishing are used on the human element of an organization to get a foot in the door. These are all daily threats faced by large and small organizations, making adamant security a necessity. Infiltrators may work simultaneously to throw a DDoS attack against some targets, serving as a distraction for network personnel and a way to soften up security measures. Once the initial steps are taken, attackers move in to install a backdoor shell as fast as possible. The shell is a malware that allows network access and capabilities for remote operations flying under the radar. Backdoors may sometimes come masquerading as legitimate software.
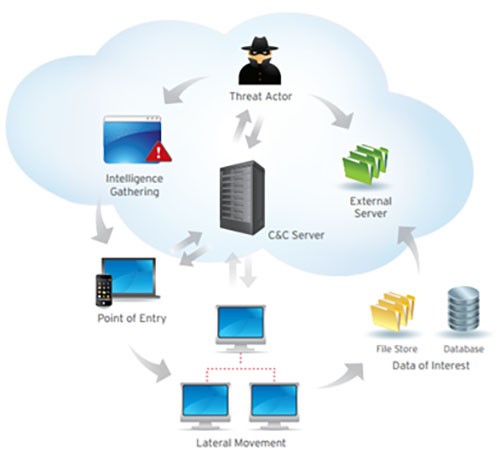
Operation Path of an Advanced Persistent Threat – Source: Infosecinstitute.com
Once the foothold has been established on a network, attackers spread their operations around the network. That involves moving up the organization’s hierarchy. Ideally, they would compromise staff members with the most access to sensitive data, gathering valuable information, such as employee data, financial records, product line information, research and development details, and more. Depending on the nature of the attack’s final goal, the gathered data may be sold to competitors of the victim company, altered to sabotage production, or even to take down entire organizations. If sabotage is the desired outcome, as was the case with the Stuxnet worm, this phase is used to either gain control of essential functions, or to manipulate them to cause maximum damage. Attackers may wipe entire databases within company servers or may sabotage network communications in a way that may take a long time to recover.
While an APT is working to compromise the security of a victim, stolen information is often stored in secure locations inside the attacked network. When the data is collected in full, the cybercriminals move on to the last step – exfiltration. In most cases, that involves distractions for the affected organization’s security team, so information can be moved while they’re busy. That may take the form of a DDoS attack, a situation that forces security to scramble. Meanwhile, the APT operators transfer the collected valuable data and cover their tracks. In some cases, that involves wiping drives and data through malware to erase any possible traces of their presence.
Suspicious activity on organization networks may be a sign of an APT attack, seen in the following examples:
The emails behind the infected attachments and social engineering emails may be fake, but they may often contain keywords referring to ongoing projects, subjects, and other bits of information that give the attackers credibility and the chance to build trust with the victim. Information about ongoing projects or other team members, gossip, and anything else that might compromise security through human error may be exploited.
Focused, successful spear-phishing attacks on executives or project leaders are an ideal situation for the cybercriminals behind an APT, as that gives them elevated access to the organizational structure. If suspicious emails are being sent to people in critical positions, that might be an ongoing attack against your organization. Avoiding this potential first step is essential since cleaning up after an APT attack involves looking for backdoors and other complications that might be avoided through proper training and operational security.
Last updated: 2026-02-07