STOP Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 3,003 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 363,455 |
| First Seen: | November 29, 2018 |
| Last Seen: | January 28, 2026 |
| OS(es) Affected: | Windows |

STOP Ransomware Image
PC security researchers received reports of ransomware attacks involving a threat known as the STOP Ransomware on February 21, 2018. The STOP Ransomware is based on an open source ransomware platform and carries out a typical version of an encryption ransomware attack. The STOP Ransomware is distributed using spam email messages containing corrupted file attachments. These file attachments take the form of DOCX files with embedded macro scripts that download and install the STOP Ransomware onto the victim's computer. Learning how to recognize phishing emails and avoiding to download any unsolicited file attachments received is one of the ways to avoid these attacks.
Table of Contents
How to Recognize a STOP Ransomware Infection
Once the STOP Ransomware is installed onto the victim's computer, the STOP Ransomware will search the victim's drives for a wide variety of file types, generally looking for user-generated files such as images, media files, and numerous other document types. The STOP Ransomware seems to be also engineered to target Web servers since it looks for database files and similar file types usually contained in these machines explicitly. The file types that the STOP Ransomware will search for and target in its attack include:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
This Week in Malware Ep 10: STOP & Zorab Ransomware Exploits Victims w/Fake Decryptor
The STOP Ransomware uses a strong encryption algorithm to make each of the victim's files inaccessible. The STOP Ransomware attack will add the file extension '.SUSPENDED' to the files it enciphers, as a way to mark the affected files.
The STOP Ransomware’s Ransom Note
The STOP Ransomware demands a ransom payment by delivering a ransom note to the victim's computer. This ransom note is displayed in a text file dropped onto the victim's desktop. The file, named '!!! YourDataRestore !!!.txt,' contains the message:
'All your important files were encrypted on this PC.
All files with .STOP extension are encrypted. Encryption was produced using unique private key RSA-1024 generated for this computer.
To decrypt your files, you need to obtain private key + decrypt software.
To retrieve the private key and decrypt software, you need to contact us by email stopfilesrestore@bitmessage.ch send us an email your !!!YourDataRestore!!!.txt file and wait for further instructions.
For you to be sure, that we can decrypt your files - you can send us a 1-3 any not very big encrypted send you back it in a original form FREE.
Price for decryption $600 if you contact us first 72 hours.
Your personal id:
[RANDOM CHARCTERS]
E-mail address to contact us:
stopfilesrestoret@bitmessage.ch
Reserve email address to contact us:
stopfilesrestore@india.com'
The people responsible for the STOP Ransomware demand a ransom payment of 600 USD to be paid using Bitcoin to a specific Bitcoin wallet address, and within 72 hours. However, contacting these people or paying the STOP Ransomware ransom may not be the best solution.
Protecting Your Data from the STOP Ransomware and Other Ransomware Trojans
The best protection against the STOP Ransomware and other ransomware Trojans is to have file backups. Computer users that have backup copies of their files can recover these files easily after an attack without having to resort to paying the ransom. A recommended security program also can prevent the STOP Ransomware from being installed in the first place.
Update December 6th, 2018 — 'helpshadow@india.com' Ransomware
The 'helpshadow@india.com' Ransomware is categorized as a comparatively small update to the code that carries the STOP Ransomware brand. The threat authors do not seem to have dedicated enough time for polishing the new variant since it scored a low infection ratio. The 'helpshadow@india.com' Ransomware was picked up by AV vendors quickly, and alerts have been issued through major social platforms and cybersecurity reports. Unfortunately, there is no possibility for free decryption yet. Users are typically compromised through a corrupted document received by email. The threat is known to erase the Shadow Volume snapshots created by Windows and attach the '.shadow' extension to the enciphered objects. For example, 'C12-H22-O11.pptx' is renamed to 'C12-H22-O11.pptx.shadow' and a ransom note called '!readme.txt' appears on the desktop. The 'helpshadow@india.com' Ransomware is likely to show the following message to the infected users:
'ALL YOUR FILES ARE ENCRYPTED
Don't worry, you can return all your files!
All your files documents, photos, databases and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees do we give to you?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information
Don't try to use third-party decrypt tools because it will destroy your files.
Discount 50% available if you contact us first 72 hours.
To get this software you need write on our e-mail:
helpshadow@india.com
Reserve e-mail address to contact us:
helpshadow@firemail.cc
Your personal ID:
[random characters]'
The text shown above is used by variants released earlier than the 'helpshadow@india.com' Ransomware and the only alteration worth noting is the new emails configuration. The 'helpshadow@india.com' Ransomware is named after one of the email contacts, and the other one refers the users to the same username but on a different email platform — 'helpshadow@firemail.cc.' Both email accounts are likely to be terminated by the time this article reaches you. The chances of catching whoever is behind the helpshadow@india.com' Ransomware are not great considering that the ransomware operators use proxies, VPN services, and the TOR Network to hide their control devices. Hence, the users need to be proactive in defending their data. Step number one — install a backup program on your system; step number two — don't open files from unknown senders. Remember to export your data backups to a removable memory storage or a file hosting service.
Update December 13th, 2018 — '.djvu File Extension' Ransomware
The '.djvu File Extension' Ransomware is a new variant of the STOP Ransomware that was reported on December 12th, 2018. Computer security researchers categorize the '.djvu File Extension' Ransomware as a small update to the previous releases of the STOP Ransomware and alert that the threat is still distributed via spam emails primarily. The threat actors have been using macro-enabled documents and fake PDFs to trick the users into installing their program silently. The attacks with the '.djvu File Extension' Ransomware are almost the same as the first wave of infections in February 2018. The threat deletes the Shadow Volume snapshots and maps connected to memory drives before it encrypts the user's data. The new variant supports a different file extension, and the ransom note is altered slightly. As the name indicates, the files receive the '.djvu' suffix and something like 'Jonne-Kaiho.mp3' is renamed to 'Jonne-Kaiho.mp3.djvu.' The ransom note can be seen on the desktop as '_openme.txt' and reads:
'ALL YOUR FILES ARE ENCRYPTED
Don't worry, you can return all your files!
All your files documents, photos, databases and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees do we give to you?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information
Don't try to use third-party decrypt tools because it will destroy your files.
Discount 50% available if you contact us first 72 hours.
To get this software you need write on our e-mail:
helpshadow@india.com
Reserve e-mail address to contact us:
helpshadow@firemail.cc
Your personal ID:
[random characters]'
The threat authors continue to use the 'helpshadow@india.com' and the 'helpshadow@firemail.cc' email accounts for their ransomware campaign. Do not trust the STOP Ransomware team and avoid using the fake 50% discount mentioned above. The threat actors discussed here are not known for their leniency. PC users should remove the '.djvu File Extension' Ransomware using a trusted anti-malware instrument. It is best to use backup images and backup services to recover your data.
Update January 11th, 2019 — '.tfude File Extension' Ransomware
The '.tfude File Extension' Ransomware is a version of the STOP Ransomware that came out on January 11th, 2019. The threat is classified as a version that exhibits minimal modifications compared to the original cyber-threat. The '.tfude File Extension' Ransomware is named after the only notable change in its corrupted code. The Trojan is configured to attach the '.tfude' file extension to encrypted data. The '.tfude File Extension' Ransomware continues to use standard encryption technologies and secure connections to the Command servers that prevent security specialists from offering free decryption to compromised users.
The crypto-threat at hand uses encryption technologies that government agencies and companies like Google Inc. employ to secure data transmissions. The encrypted files are displayed in the Windows explorer as generic white icons, and the programs the user has installed remain functional. However, certain database managers may not work properly since the threat encodes popular database formats. For example, 'Recent sales.pdb' is renamed to 'Recent sales.pdb.tfude.' The ransom note is loaded in the Notepad from the file '_openme.txt,' which can be found on the desktop. The '.tfude File Extension' Ransomware offers the same message as the original Trojan, but this time the threat actors are using the 'pdfhelp@firemail.cc' email account to reach out to users. There is no free decryptor available for the users, and you will need to use data backups to recover. You will need to clean the infected devices by running a complete system scan with a reputable anti-malware instrument.
Update January 23th, 2019 — 'pausa@bitmessage.ch' Ransomware
The 'pausa@bitmessage.ch' Ransomware is a file encoder malware that is produced with the STOP Ransomware Builder. The 'pausa@bitmessage.ch' Ransomware was released to PC users via spam emails in the first week of May 2018. The 'pausa@bitmessage.ch' Ransomware is perceived as a generic encryption Trojan that overwrites data on infected computers and deletes volume snapshots to obstruct recovery. The 'pausa@bitmessage.ch' Ransomware is known to use the same encryption technologies as other successful Ransomware like Cerber and Dharma to name a few. The 'pausa@bitmessage.ch' Ransomware is programmed to run from the Temp folder under the AppData directory and apply a secure AES-256 cipher to documents, video, music, databases, and ebooks. Encoded data receives the '.PAUSA' extension and something like 'Hartmann-Save me.mp3' is renamed 'Hartmann-Save me.mp3.pausa.' The ransom notification is saved as '!!RESTORE!!!.txt' to the user's desktop and reads:
'All your important files were encrypted on this PC.
All files with .PAUSA extension are encrypted.
Encryption was produced using unique private key RSA-1024 generated for this computer.
To decrypt your files, you need to obtain private key + decrypt software.
To retrieve the private key and decrypt software, you need to contact us by email pausa@bitmessage.ch send us an email your !!!RESTORE!!!.txt file and wait for further instructions.
For you to be sure, that we can decrypt your files - you can send us a 1-3 any not very big encrypted files and we will send you back it in a original form FREE.
Price for decryption $600 if you contact us first 72 hours.
Your personal id:
[random characters]
E-mail address to contact us:
pausa@bitmessage.ch
Reserve e-mail address to contact us:
pausa@india.com'
We recommend you avoid negotiations with the threat actors via the 'pausa@bitmessage.ch' and the 'pausa@india.com' email accounts. It is safer to boot data backups and clean your system with the help of a reputable anti-malware tool. Even if you pay the absurd ransom of $600, there is no guarantee you will receive a decryptor. PC users are encouraged to make data backups at least two times a month and ignore spam messages that may lead to a security compromise. AV companies support detection rules for the 'pausa@bitmessage.ch' Ransomware, but there is no free decryptor available at the time of writing.
Update January 23th, 2019 — 'waiting@bitmessage.ch' Ransomware
The 'waiting@bitmessage.ch' Ransomware is an encryption Trojan that is based on the STOP Ransomware. The 'waiting@bitmessage.ch' Ransomware was reported by compromised users on April 18th, 2018 and it appears to invade computers via corrupted Microsoft Word documents. The 'waiting@bitmessage.ch' Ransomware is recorded to encrypt photos, audio, video, and text on the infected computers. Unfortunately, the malware authors added a command to delete the volume snapshots Windows makes to protect your data. The Trojan overwrites targeted data with files that carry the '.WAITING' extension and can't e opened with software on your system. For example, 'Hartmann-Like a River.mp3' is renamed to 'Hartmann-Like a River.mp3.waiting,' and a ransom message is dropped to your desktop. The 'waiting@bitmessage.ch' Ransomware writes '!!!INFO_RESTORE!!!.txt' to the desktop and shows the following text:
'All your important files were encrypted on this PC.
All files with .WAITING extension are encrypted.
Encryption was produced using unique private key RSA-1024 generated for this computer.
To decrypt your files, you need to obtain private key + decrypt software.
To retrieve the private key and decrypt software, you need to contact us by email waiting@bitmessage.ch send us an email your !!!INFO_RESTORE!!!.txt file and wait for further instructions.
For you to be sure, that we can decrypt your files - you can send us a 1-3 any not very big encrypted files and we will send you back it in a original form FREE.
Price for decryption $600 if you contact us first 72 hours.
Your personal id:
[random characters]
E-mail address to contact us:
waiting@bitmessage.ch
Reserve email address to contact us:
waiting@india.com'
The malware does not interfere with third-party backup tools, and you should be able to boot data backups. It is recommended to avoid interaction with the threat actors via the 'waiting@bitmessage.ch' and the 'waiting@india.com' email addresses. You may be interested in exploring file hosting services if you wish to protect your data backups against network transmitted cyber threats and most Ransomware variants like the 'waiting@bitmessage.ch' Ransomware.
Update November 25th, 2019 - .zobm and .rote Extensions
Security researchers came across a couple of new variants of the STOP Ransomware on November 24 and November 25, 2019. The ransomware variants appended the encrypted files with .zobm and .rote extensions, but had an identical ransom note, named _readme.txt. The emails through which the threat actors could be reached were also the same – datarestorehelp@firemail.cc and datahelp@iran.ir.
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-4NWUGZxdHc
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
datarestorehelp@firemail.cc
Reserve e-mail address to contact us:
datahelp@iran.ir
Your personal ID:
[random characters]
STOP Ransomware in 2019 and Beyond
Later in 2019, the STOP ransomware was still being used and new attack vectors were being tested. The STOP ransomware started appearing in bundles containing other forms of malware, primarily adware, that you can find on websites claiming to host cracked executables for games and software. This way, many of the ransomware's new victims turned out to be hopeful software pirates looking who got more than they bargained for.
There has also been evidence that the STOP ransomware is installing password-stealer Trojans that are able to scrape various login credentials.
The ransomware also expanded the long list of encrypted file extensions it uses. Files encrypted by the STOP ransomware now received the .rumba and .tro extensions. Thus far, little else has changed - the ransom note was still found in a file named "_openme.txt", but the ransom sum was bumped up to $980, with a reduction to $490 if the victim pays within the first 72 hours following infection.
Update March 24th, 2020 – New Variants
The threat actors behind the STOP Ransomware have been working as tirelessly in 2020 as they did in 2019, with new variants encrypting victims' files and appending them with a variety of new extensions. Some of the new extensions of the STOP Ransomware include .piny, .redl, .rooe, mmnn, .ooss, .rezm, .lokd, and .foop.
A sample of a ransom note that came with the .lokd variant contained the following text:
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents, and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t7m8Wr997Sf
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail ''Spam'' or ''Junk'' folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
helpdatarestore@firemail.cc
Reserve e-mail address to contact us:
helpmanager@mail.ch
Your personal ID:
[random characters]
Other emails that the threat actors have been using with these new variants include helpmanager@iran.ir and helpmanager@firemail.cc.
SpyHunter Detects & Remove STOP Ransomware
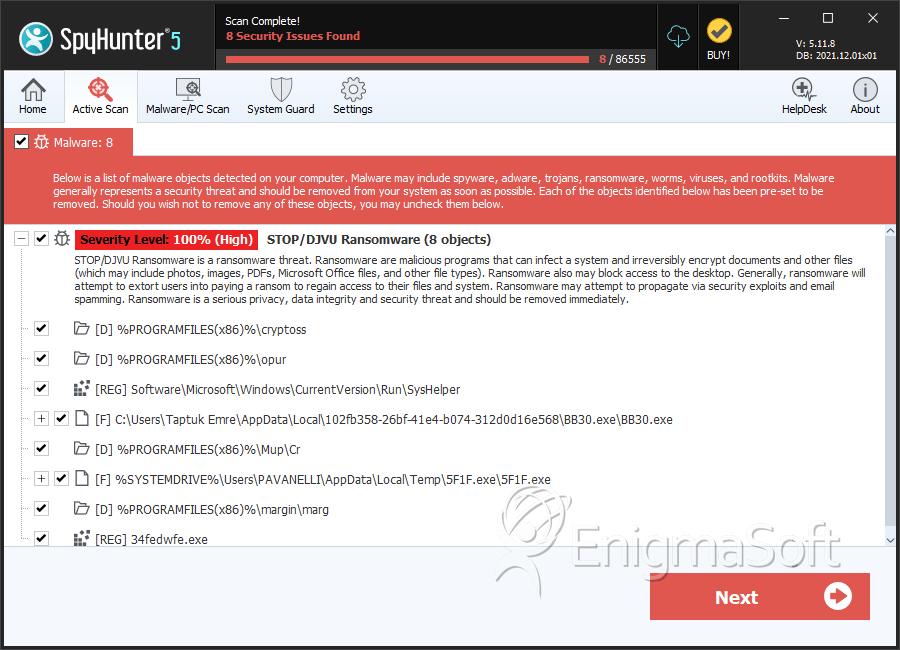
STOP Ransomware Screenshots
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | BB30.exe | f8ef98bbaff6ac82dacde20ee90bfa55 | 4,207 |
| 2. | 5F1F.exe | b5b59a34192343da2c0fc84fb3bb6b2e | 3,154 |
| 3. | 3ffa.exe | a0192bd5d8164e61819890e908fa0e7d | 1,890 |
| 4. | 97DE.tmp.exe | 4e8f1415dd3366f81fa3960db4cf70f9 | 1,772 |
| 5. | 1368.tmp.exe | 8cebee5086592386fa86f3ee5bacc0d2 | 1,647 |
| 6. | 9686685955.exe | 5c71f8c3bb000d163fc2e63c089b35a1 | 1,631 |
| 7. | a395.tmp.exe | 536f955ae69e666b44aac54c7619b9b1 | 1,589 |
| 8. | 3823.TMP.EXE.WPT | d4fceee0f4fe0f1b50a5c957eab5151b | 1,500 |
| 9. | 512B.tmp.exe | 89b1b4f3f6ec190865abaa7f61046ee5 | 1,255 |
| 10. | 3344.exe | 6a4d9e0ad2a5361dd947537182f5692d | 1,240 |
| 11. | d5e2.tmp.exe | 4c1b9a14dda6a74b7abff708758d98f6 | 1,038 |
| 12. | B117.tmp.exe | 283bf952e656763a94626cac01d7bc85 | 979 |
| 13. | 25b9.tmp.exe | 9bd737b220a4040dbcaf17f48be54a98 | 825 |
| 14. | 3A93.tmp.exe | d5995275a4d96672ed08cc6188143a7a | 773 |
| 15. | 2c6b.tmp.exe | ac2dffb783aed99d77ecc2006a29d971 | 744 |
| 16. | 618.tmp.exe | 99ba307185c56cfb6d9ea965fcfef083 | 719 |
| 17. | 160f.tmp.exe | 3a1a3c4b4b3de474b574f48198d6e41e | 647 |
| 18. | 1df7.tmp.exe | ad5a82caee53510fafcdfcddfa74daae | 54 |
| 19. | 5cd3.tmp.exe | 1569c3b648b4c63ae39ddc2d2d91b7d5 | 14 |
| 20. | e5cb.tmp.exe | 031ff93d3e55a84f475cf0b563fe7f65 | 14 |
| 21. | 5dcc.tmp.exe | e3b973420daf30a4180f60337a2eaf90 | 14 |
| 22. | 6fa4.tmp.exe | 67e8f528b4db3443a74718443a2fc788 | 12 |
| 23. | cc0.tmp.exe | 0564489cff6c549ca82b7a470b305346 | 11 |
| 24. | c11d.tmp.exe | a0eb1e740d92c51576ed117d8b6de3c5 | 11 |
| 25. | ransomware.exe | fdc340769c3ca364f6cc7ca1be99762b | 0 |
Registry Details
Directories
STOP Ransomware may create the following directory or directories:
| %ALLUSERSPROFILE%\tzjajmmqgl |
| %PROGRAMFILES%\3DMarkproed |
| %PROGRAMFILES%\3DMarkproediot |
| %PROGRAMFILES%\3DMarkproedit |
| %PROGRAMFILES%\3Dmarkproa |
| %PROGRAMFILES%\Blubnerg |
| %PROGRAMFILES%\Cry\Cryp |
| %PROGRAMFILES%\Davai |
| %PROGRAMFILES%\Glary\Utilities\Settings |
| %PROGRAMFILES%\Hyps |
| %PROGRAMFILES%\Innovativ\ddd |
| %PROGRAMFILES%\Ivp\bin |
| %PROGRAMFILES%\Laertseer |
| %PROGRAMFILES%\Lawer\Xor |
| %PROGRAMFILES%\Marg\Cr |
| %PROGRAMFILES%\Mup\Cr |
| %PROGRAMFILES%\Opute |
| %PROGRAMFILES%\Rondom |
| %PROGRAMFILES%\Sir\Air |
| %PROGRAMFILES%\Tryhd |
| %PROGRAMFILES%\cedfs |
| %PROGRAMFILES%\chrum\xon\note |
| %PROGRAMFILES%\company\3dmarkssdf |
| %PROGRAMFILES%\company\64Product |
| %PROGRAMFILES%\crights\file\xml |
| %PROGRAMFILES%\cryptoss |
| %PROGRAMFILES%\crys\cry |
| %PROGRAMFILES%\crysp\cryq |
| %PROGRAMFILES%\der\supr |
| %PROGRAMFILES%\dera\kii |
| %PROGRAMFILES%\ferr\seda\sx\bin |
| %PROGRAMFILES%\hop |
| %PROGRAMFILES%\inner\win\bin |
| %PROGRAMFILES%\krontal |
| %PROGRAMFILES%\laert |
| %PROGRAMFILES%\laerts |
| %PROGRAMFILES%\lass\inst |
| %PROGRAMFILES%\lastpass\bur\tronfiles |
| %PROGRAMFILES%\lawop |
| %PROGRAMFILES%\lawops |
| %PROGRAMFILES%\margin\marg |
| %PROGRAMFILES%\opur |
| %PROGRAMFILES%\sccsd |
| %PROGRAMFILES%\sir\xd |
| %PROGRAMFILES%\virtka |
| %PROGRAMFILES%\xery |
| %PROGRAMFILES%\youtubedown |
| %PROGRAMFILES(x86)%\3DMarkproed |
| %PROGRAMFILES(x86)%\3DMarkproediot |
| %PROGRAMFILES(x86)%\3DMarkproedit |
| %PROGRAMFILES(x86)%\3Dmarkproa |
| %PROGRAMFILES(x86)%\Blubnerg |
| %PROGRAMFILES(x86)%\Cry\Cryp |
| %PROGRAMFILES(x86)%\Davai |
| %PROGRAMFILES(x86)%\Hyps |
| %PROGRAMFILES(x86)%\Innovativ\ddd |
| %PROGRAMFILES(x86)%\Laertseer |
| %PROGRAMFILES(x86)%\Lawer\Xor |
| %PROGRAMFILES(x86)%\Marg\Cr |
| %PROGRAMFILES(x86)%\Mup\Cr |
| %PROGRAMFILES(x86)%\Opute |
| %PROGRAMFILES(x86)%\Rondom |
| %PROGRAMFILES(x86)%\Sir\Air |
| %PROGRAMFILES(x86)%\Tryhd |
| %PROGRAMFILES(x86)%\cedfs |
| %PROGRAMFILES(x86)%\chrum\xon\note |
| %PROGRAMFILES(x86)%\company\3dmarkssdf |
| %PROGRAMFILES(x86)%\company\64Product |
| %PROGRAMFILES(x86)%\crights\file\xml |
| %PROGRAMFILES(x86)%\cryptoss |
| %PROGRAMFILES(x86)%\crys\cry |
| %PROGRAMFILES(x86)%\crysp\cryq |
| %PROGRAMFILES(x86)%\der\supr |
| %PROGRAMFILES(x86)%\dera\kii |
| %PROGRAMFILES(x86)%\ferr\seda\sx\bin |
| %PROGRAMFILES(x86)%\hop |
| %PROGRAMFILES(x86)%\inner\win\bin |
| %PROGRAMFILES(x86)%\krontal |
| %PROGRAMFILES(x86)%\laert |
| %PROGRAMFILES(x86)%\laerts |
| %PROGRAMFILES(x86)%\lass\inst |
| %PROGRAMFILES(x86)%\lastpass\bur\tronfiles |
| %PROGRAMFILES(x86)%\lawop |
| %PROGRAMFILES(x86)%\lawops |
| %PROGRAMFILES(x86)%\margin\marg |
| %PROGRAMFILES(x86)%\opur |
| %PROGRAMFILES(x86)%\sccsd |
| %PROGRAMFILES(x86)%\sir\xd |
| %PROGRAMFILES(x86)%\virtka |
| %PROGRAMFILES(x86)%\xery |
| %PROGRAMFILES(x86)%\youtubedown |
| %ProgramFiles%\kiss\me |
| %ProgramFiles%\mroz\new\trunk |
| %ProgramFiles(x86)%\kiss\me |
| %ProgramFiles(x86)%\mroz\new\trunk |
Analysis Report
General information
| Family Name: | STOP/DJVU Ransomware |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
def8a7bfe5fe47d95a95085d8dbc7a53
SHA1:
7182d4b2f55a560d83edf0824e119f71fa8422b6
SHA256:
B83855EA63E7F28396099A5B6E877BE537E78E4A50DF720262461A1D13B02192
File Size:
6.29 MB, 6292105 bytes
|
|
MD5:
a6b8c0cb178c31dd347554c3e5a0d5f8
SHA1:
91864f269d696ee80869cfeb3c9a204f8031a3bb
SHA256:
4FFB8E9ADF508662B5E51CBEC75B2E07CE1CBBFAAB873F72EDC7BAC385421E2C
File Size:
3.47 MB, 3471869 bytes
|
|
MD5:
2336c9624d9a44c393d354206226f508
SHA1:
ea7edc388ad62990f52b9ed40df26d20f4e20190
SHA256:
CE48ED04C92143B7E91F9665DD9337B2EE0B9CC1B5AEE534D26C09E084F8ABB0
File Size:
1.36 MB, 1359918 bytes
|
|
MD5:
42f32aa699bc45a3638ddeb325ebebc1
SHA1:
508cea3ba2bf04cc6851295f92bf0e752071f6b8
SHA256:
16532B38591B713395C288B11610494BCC4C4537BE492D43C54D66FEB7B95FA4
File Size:
1.33 MB, 1328186 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has exports table
- File has TLS information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
Show More
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Comments | This installation was built with Inno Setup. |
| Company Name |
|
| File Description |
|
| File Version |
|
| Internal Name |
|
| Legal Copyright | Copyright © Alexander Roshal 1993-2022 |
| Original Filename |
|
| Product Name |
|
| Product Version |
|
File Traits
- 2+ executable sections
- big overlay
- HighEntropy
- Installer Manifest
- No Version Info
- RAR (In Overlay)
- RARinO
- SusSec
- vb6
- WinRAR SFX
Show More
- WRARSFX
- x86
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp\is-13e8d.tmp\508cea3ba2bf04cc6851295f92bf0e752071f6b8_0001328186.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-88uan.tmp\ea7edc388ad62990f52b9ed40df26d20f4e20190_0001359918.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-pk5hm.tmp\_isetup\_setup64.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\is-shkd6.tmp\_isetup\_setup64.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Other Suspicious |
|
| Anti Debug |
|
| User Data Access |
|
| Process Manipulation Evasion |
|
| Process Shell Execute |
|
| Keyboard Access |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
"C:\Users\Lehsoaco\AppData\Local\Temp\is-88UAN.tmp\ea7edc388ad62990f52b9ed40df26d20f4e20190_0001359918.tmp" /SL5="$5036E,928289,131584,c:\users\user\downloads\ea7edc388ad62990f52b9ed40df26d20f4e20190_0001359918"
|
"C:\Users\Dfhrhqtz\AppData\Local\Temp\is-13E8D.tmp\508cea3ba2bf04cc6851295f92bf0e752071f6b8_0001328186.tmp" /SL5="$802E8,896816,131584,c:\users\user\downloads\508cea3ba2bf04cc6851295f92bf0e752071f6b8_0001328186"
|

