XHAMSTER Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 7,187 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 5,745 |
| First Seen: | July 24, 2009 |
| Last Seen: | August 20, 2024 |
| OS(es) Affected: | Windows |
Cybercriminals are using the XHAMSTER Ransomware threat to lock their victims' data. The XHAMSTER Ransomware is a new variant of the Phobos Ransomware. The strong encryption algorithm utilized by XHAMSTER ensures that the affected files will be nearly impossible to restore without the assistance of the hackers. More specifically, without having the specific decryption keys in their possession.
Once activated on the compromised device, XHAMSTER will affect a wide range of file types, including the victim's documents, photos, PDFs, archives, databases, and many more. As part of its actions, the ransomware will also significantly modify the original names of the locked files:
- It will add an ID string generated for the particular victim.
- The threat will add the ICQ account of the attackers (ICQ@xhamster2020).
- '.XHAMSTER' will be appended as a new file extension.
Victims of the threat will be presented with two ransom notes. One will be inside a newly generated text file named 'info.txt.' The other will be displayed in a pop-up window created from an 'info.hta' file. The instructions in both places are identical.
Table of Contents
Demands Overview
The ransom-demanding message of the threat doesn't specify the exact sum that victims are expected to pay as ransom. However, it is stated that the amount will be based on how fast affected users establish contact with the attackers. Furthermore, the only payment method accepted is the one made using the Bitcoin cryptocurrency will be accepted. The note also tells victims they can send up to 5 files to be decrypted for free. It is likely a demonstration of the hackers' ability to unlock all of the affected data. The total size of the chosen files must not exceed 3MB in non-archived form, and they should not contain any important or valuable information. To receive additional details, victims of the threat are directed toward contacting the same ICQ account found in the names of the encrypted files.
What Does XHAMSTER Ransomware Look Like?
XHAMSTER Ransomware uses a clever ransom note where it makes rather forceful demands and instructions to supposedly restore the files that it has encrypted. Moreover, XHAMSTER Ransomware instructs victimized computer users not to rename encrypted files or use a third-party software resource to decrypt the data. Lastly, the message explains that victims will have to pay for the decryption tool in Bitcoins, a common method of payment that helps prevent the hackers behind XHAMSTER from being tracked or caught performing the malicious actions of spreading such malware and extorting money from victimized computer users.
Image Example of the XHAMSTER Ransomware Ransom Note & Alert Message
XHAMSTER Ransomware Ransom Note
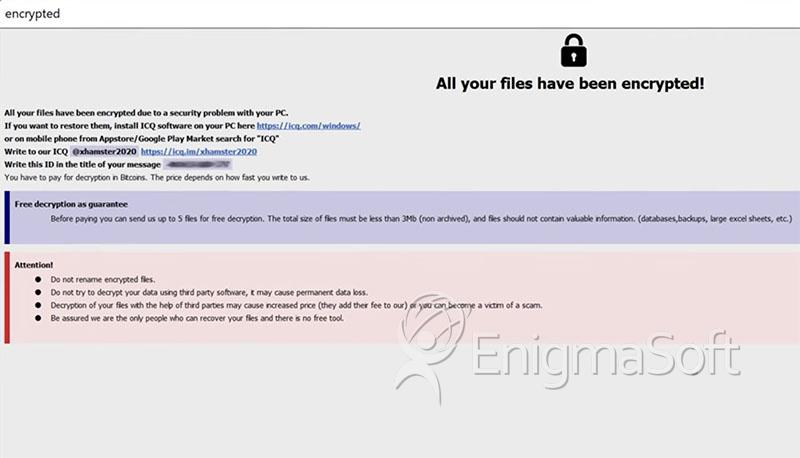
The full set of instructions left by XHAMSTER Ransomware is:
'All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC.
If you want to restore them, install ICQ software on your PC here hxxps://icq.com/windows/
or on mobile phone from Appstore/Google Play Market search for "ICQ"
Write to our ICQ @xhamster2020 hxxps://icq.im/xhamster2020
Write this ID in the title of your message -
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 3Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Be assured we are the only people who can recover your files and there is no free tool.'
Where Does XHAMSTER Ransomware Come From and How to Prevent Future Infections?
The XHAMSTER Ransomware threat is among the more aggressive forms of malware. XHAMSTER is considered more of a prevalent and demanding type of malware because it can employ several distribution methods and thus spread through questionable downloaded software or software installation bundles. Furthermore, by renaming the files, XHAMSTER may append the developer’s information and a new file extension. Such files will then be inaccessible and force computer users to find a solution for those files through decryption or to restore them from a backup copy. Our assessment and technical analysis found that files encrypted by XHAMSTER cannot be decrypted by any available third-party resources, leaving computer users with very few options.
Like many other ransomware threats, XHAMSTER can spread efficiently and effectively through spam email attachments such as PDF documents, ZIP files, RAR files, .exe executable files, JavaScript files, and even malicious Microsoft Office documents. In other instances of XHAMSTER spreading, it comes from unreliable sources on the Internet or malicious websites that may offer software downloads that turn out to be bogus or fake software activation tools (crack software) and resources. Many of these harmful sites are designed to look legitimate or like a “trusted” source to trick computer users into downloading their files or software.
Many malicious downloads that infect computers with XHAMSTER Ransomware contain a nasty payload or Trojan horse that may load on a vulnerable computer without indicating to the computer user or administrator. These are often the worst cases of infecting a computer with XHAMSTER as the user later discovers the threat through its ransom notification, which means it’s too late to stop XHAMSTER Ransomware in its tracks.
Computer users should avoid downloading questionable software files from deceptive websites or installation bundles from third-party sources. These sources thrive on unsuspecting computer users, as do spam emails that contain malicious attachments. Such emails may appear legitimate, either offering an enticing message or appearing to be from an official company that pressures a computer user into opening or downloading the attachment file, which contains the payload that loads XHAMSTER Ransomware. If a computer user encounters a questionable email or spam message, it should be deleted immediately.
The curiosity of some computer users in opening an enticing spam email or attachment is what gets them into trouble. All it takes is to open the malicious attachment file once, and the payload is free to conduct malicious actions.
Are There Any Other Solutions or Steps to Take to Fix the XHAMSTER Ransomware Issues?
Some computer users have successfully disconnected their system from the Internet upon noticing the XHAMSTER infection to isolate their system and prevent further damage from XHAMSTER. While such a process may seem like a good idea, the fact remains that XHAMSTER Ransomware will encrypt files regardless of a connection to the Internet.
The infiltration of storage devices connected to a computer infected with XHAMSTER may occur regardless of an Internet connection being available after the initial infection. Though, ejecting or disconnecting storage devices may suffice in preventing XHAMSTER from encrypting stored files on those devices.
There is no way of stopping XHAMSTER Ransomware from encrypting files and performing malicious actions once a system is infected. Fortunately, removing XHAMSTER completely from a PC will stop its malicious activities, which could otherwise result in the encryption of additional files or ones found on storage devices connected to the affected computer.
Removing XHAMSTER Ransomware Is Essential to Help Remedy Its Malicious Actions
While preventing threats like XHAMSTER Ransomware is the best method to keep a computer from being infiltrated and files encrypted, removing XHAMSTER with an antimalware tool is the next best approach to remedying such a malicious attack. Ransomware removal is essential to recovering encrypted files and restoring an affected system to normal operation. XHAMSTER Ransomware may continue its malicious activities if it is left on an infected computer. It is important to avoid delay in removing XHAMSTER once a computer user has identified or detected the threat using an antimalware resource.
Using a malware removal tool to safely detect and remove XHAMSTER Ransomware will free up system resources and the ability to restore files that XHAMSTER may have damaged beyond repair through encryption. Not only will removing XHAMSTER Ransomware stop the file encryption process, but it may allow a computer user to safely restore files without concern that the new files will be targeted and eventually encrypted.
Because there is no known decryption tool that restores files encrypted such aggressive malware threat like XHAMSTER Ransomware, computer users should always back up their systems and utilize antimalware software to help protect their files from future threats. Such threats may be proactively detected and stopped before they can propagate and perform malicious actions if a proper antimalware resource is consistently used.
XHAMSTER Ransomware Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
XHAMSTER Ransomware Screenshots
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ~tmp1174.exe | ff47c3fcc59b40f444c8fcfe48255f26 | 0 |

