KeRanger Ransomware
KeRanger Ransomware Image
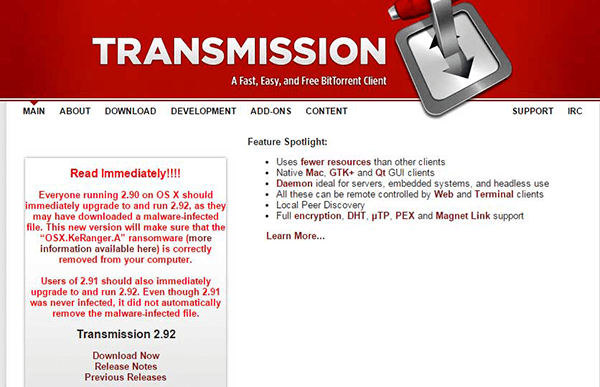
The KeRanger Ransomware is an encryption ransomware Trojan. The KeRanger Ransomware gained attention because it seems to be the first encryption ransomware Trojan that carries out a complete attack and is directed to attack computers running the Mac OS operating system. PC security researchers first observed the KeRanger Ransomware being distributed as a fake version of Transmission, a BitTorrent client on March 2016. The KeRanger Ransomware, like most encryption ransomware Trojans, is designed to take over victims' computers, taking the victim's files hostages and then demanding a ransom payment from the victim in exchange for the decryption code needed to restore the affected files.
Table of Contents
What the KeRanger Ransomware Trojan can Cause to Your Files
The KeRanger Ransomware has a feature that has not been observed in ransomware Trojans targeting the Windows systems: the KeRanger Ransomware enters a dormant stage when it infects a computer, sleeping for three days before it carries out its attack. Once the KeRanger Ransomware is activated, the KeRanger Ransomware uses a strong encryption algorithm to encrypt the victim's data, adding the file extension '.encrypted' to each file compromised by the KeRanger Ransomware attack. Threats like the KeRanger Ransomware target certain files in these attacks, which include:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The KeRanger Ransomware delivers a ransom note in the form of a text file named 'README_FOR_DECRYPT.txt,' which contains the following message for the victim:
'Your computer has been locked, and all your files has been encrypted with 2048-bit RSA encryption.
instruction for decrypt:
1. Go to h[tt]ps://fiwf4kwysoldpwShonlon[.]to ( IF NOT WORKING JUST DOWNLOAD TOR BROWSER AND OPEN THIS LINK: h[tt]ps://fiwf4kwysoldpwShonlon[.]onion )
2. Use 1PGaufinNcvSnYKopligaggpkynynomEof as your ID for authentication
3. Pay 1 BTC (≈407.47$) for decryption pack using bitcoins (wallet is your IP for authentication - 1PGAIMINO6NYMPN244rFkYAMMIREof)
4. Download decrypt pack and run
Also at h[tt]ps://fiwfalkwysmAdowSl.onion[.]to you can decrypt 1 file for FREE to make sure decryption is working.
Also we have ticket system inside, so if you have any questions - you are welcome.
We will answer only if you able to pay and you have serious question. IMPORTANT: WE ARE ACCEPT ONLY (!!) BITCOINS
HOW TO BUY BITCOINS:
h[tt]ps://localbitcoins[.]com/guides/how-to-buy-bitcoins
h[tt]ps://en.bitcoin[.]it/wiki/Buying_Bitcoinsjthe_newbie_version'
Dealing with the KeRanger Ransomware Infection
Unfortunately, once the KeRanger Ransomware has encrypted the victim’s files, these files will no longer be recoverable without the decryption key. Because of this, prevention is the most important way of limiting the effects of attacks like the KeRanger Ransomware. Computer users are advised to have backup copies of their files and avoid installing suspicious software distributed by third parties, similar to the corrupted version of Transmission commonly used to distribute the KeRanger Ransomware in its first attacks.
KeRanger Ransomware is the first of its kind to target Mac computers but not the last
While a close eye has been kept on Windows PCs with an influx of ransomware in the past several years, Mac computers have been known to be a safer bet until now. While being among the first of its kind to attack Mac computers, KeRanger Ransomware will not be the last ransomware threat as it looks to have had success in extorting money from Mac users.
The widespread effects of KeRanger Ransomware have taken the Mac computer world by storm in that it acts much like well-known ransomware threats do when they attack Windows computers. Moreover, KeRanger Ransomware will encrypt files on a Mac OS computer as mentioned previously, but it does it more through a web browser-based platform. Such a method utilizes and relies more on web browser apps that are installed on Mac computers where the demands can be prompted through websites and paths accessed by web browser applications.
As far as where KeRanger Ransomware comes from, we've noticed that the threat may lie dormant for days on end while residing on a Mac computer. Though, KeRanger Ransomware directly comes from a legitimate Transmission BitTorrent client that was replaced with a malicious variation. While Apple has revoked the certificate of the Transmission BitTorrent client app, the spread of the ransomware has already taken place on countless systems. Moreover, Keranger Ransomware may have alternate methods of infecting a Mac computer, potentially taking on the actions of common Windows PC ransomware to spread via spam email attachments.
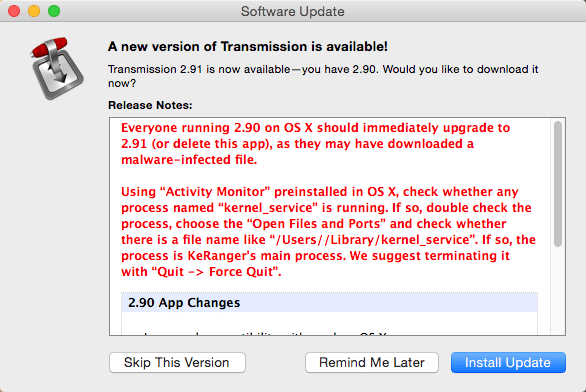
Notification to update version of Transmission due to KeRanger Ransomware-infected version installed
There is still much unknown about KeRanger Ransomware and how the files on the legitimate Transmission's website were altered to give Mac users a malicious version of the client app. The malicious app was titled General.rtf and copied to the ~/Library/kernel_service path on the Mac OS X. Masking itself as an RTF file allowed it to act as the main executable for the KeRanger Ransomware, where upon execution it would remain dormant and later contact its designated TOR command and control servers and send information collected about the infected Mac computer. From there, the Mac user could view the ransom note and find the TOR payment site that must be accessed to pay the ransom for supposedly downloading a decryptor. The payment site, fiwf4kwysm4dpw5l.onion, utilizes Bitcoins for its method of collecting payment demanding Bitcoin IDs.
If a Mac user ever pays the ransom, they may be granted a decryption app, but it is known that the decryptor will only work with one Mac computer and cannot be shared. Regardless, it is not recommended that Mac users pay the ransom but instead eliminate the KeRanger Ransomware immediately using a proper antimalware resource.


