Are You Sure You’re NOT Infected with Malware?
Don’t Fall Victim to Malware or Ransomware Attacks!
Detect and remove malware, viruses, ransomware & other threats for FREE! Get Protected with SpyHunter.
Download SpyHunter (FREE Trial!)*Phishing (pronounced ‘fishing’) is an online attack strategy used by cybercriminals to deceptively gather or collect data. Stolen data could then be used to breach the security of online accounts, hack into websites, or aid in targeted malicious attacks. When ‘fishing’, one must lay a trap or bait to hook the catch.
Phishing attacks have evolved over the years and taken on a different face, one that may appear to many as a legitimate entity that doesn’t raise any suspicion among computer users. Unfortunately, many of the modern-day phishing attacks are carefully crafted by resourceful hackers and come in many different forms. Some of the forms, such as spam email messages that look like legitimate emails from banks, social media networks, and other popular sources, are at the frontline of stealing data from unsuspecting computer users.
Phishing dates back to 1995 and the bait has evolved and expanded since its debut. Here are a few traps to avoid:
The landscape of modern-day phishing attacks has leaned towards theft of personal data, which in turn can easily lead to identity theft cases. Identity theft is a prevalent issue when it comes to phishing. Because phishing attacks have a primary goal of stealing personal information from a victimized computer user, identity theft cases loom with today’s hackers utilizing sophisticated malware threats to leverage phishing attacks so they may collect personal data and potentially sell it over the Dark Web to the highest bidder. Such a process is known to garner identity theft cases at alarming rates.
Other forms of modern-day phishing attacks often leverage government entities like the IRS where spoofed emails claim to be from the IRS or hackers breach data from the IRS so they can later send phishing emails to taxpayers demanding personal information like their address and social security number. Such an incident of breaching data at the IRS resulted in over a half a million taxpayers’ having their information accessed.
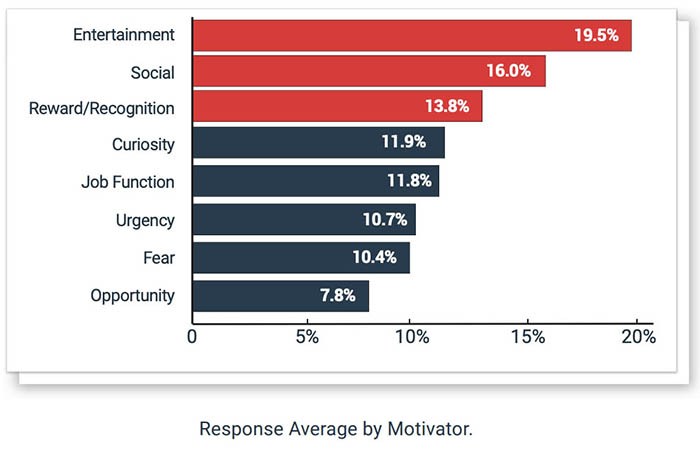
Among Internet behaviors that contribute to emotional motivators behind successful phishes, entertainment and social rank the highest, according to PhishMe’s Enterprise Phishing Resiliency and Defense Report released in 2018 (demonstrated in the Figure 1. chart below). Additionally, PhishMe mentions that mature anti-phishing programs may have conditioned employees to spot certain work-related scams, potentially influencing the results show in the chart below. The totality of the PhishMe report shows that phishing attempts have grown overall 65% in 2018.
Figure 1. PhishMe Phishing Behavioral Chart 2018
Spam emails are at the forefront of phishing attacks, one of the most popular aspect of sophisticated phishing methods, and one commonly used to directly spread modern ransomware threats or other malware as an attachment. Unfortunately, many spam messages have evolved to exploit vulnerabilities and bypass spam detection methods and software. Often there are many different forms of spam messages that initiate phishing campaigns, such as the following popular subject matters:
The best way to avoid becoming a victim of Phishing and having your valuable data stolen and abused is by verifying the source of emails, IMs, or any links and attachments before clicking. Otherwise, you could not only be transported to a look-a-like or fraudulent form or webpage awaiting input of your financial or personal data, but too could unleash malware onto your vulnerable system.
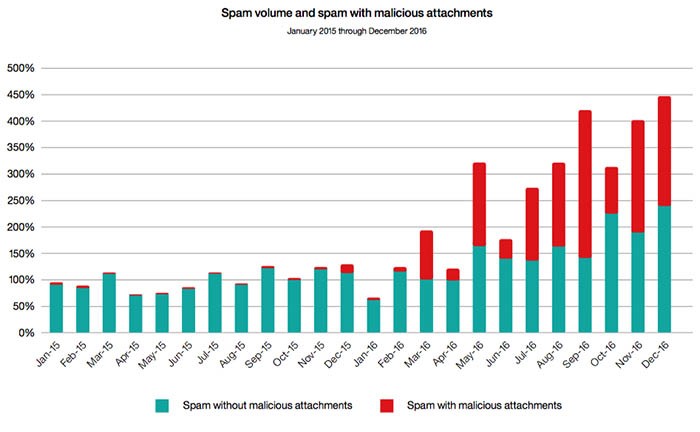
The overall volume of spam emails has shown some inclines while those with malicious attachments has pushed the collective amount of spam messages to new records from January 2015 to December 2016 as shown in the IBM Threat Intelligence Index 2017 report chart below (Figure 2.). Moreover, email remains to be the number one method for delivering malware to vulnerable computers around the world keeping phishing a prevalent issue.
Figure 2. IBM Threat Intelligence Index 2017 Malicious Spam Attachments Chart
Not all ‘Phishing’ leads to a website but rather too could be executed over the phone. In these cases, the victim will be provided a phone number that is fraudulent. Supposedly the phone number is that of a trusted source, i.e. Microsoft or bank representatives, etc., and the person or recording will ask the victim to either verify their personal information or provide it. Don’t be surprised that the attacker knows just enough information about you already to sell or legitimize the scam. The Internet and its tracking of personal data has made it easy for just about anyone to learn about you, such as your name, age, intimate associations, birth city and state or current residence, as well as past ones, or even political or religious affiliations. Knowing that you work for XYZ, for instance, makes a cleverly spoofed and written email seem believable. So never think it silly or a waste of time to ‘pick up the phone’ and verify the communication before you click or provide requested data. The worst that could happen is that the receiver ‘verifies’ it is legitimate. Otherwise, the following could result:
Actually, malware could already be present on your system, for example, a backdoor that a gives a hacker the ability to remotely access and control your computer. Don’t wait to learn that a DNS strike was tracked to your IP address or that your online accounts were hacked and your money stolen.
Many times, computer users have issue with identifying a phishing scam or a phishing email. PhishMe, a ten-year-old firm that helps companies train employees to help avoid phishing scams, had their CEO on CNBC to discuss how the biggest issue is “US” and how we can take steps to spot phishing emails among other phishing scams in the video below.
Phishing attacks have no boundaries and social media platforms are prime targets for hackers to proliferate phishing campaigns. Undoubtedly, social media is in high demand with billions of users who access the popularized networks of Facebook, Twitter, Instagram and others on a daily basis. Among the most popular methods of hackers stealing one’s identity and potentially their money is through social media giants like Facebook. There are countless phishing campaigns used throughout Facebook and other social media networks that are highly effective at collecting personal information from users. Many of the modernized phishing campaigns are sometimes masked as advertisements, quizzes, like-jacking scams, free offers, or the common personable post with an attached malicious link.
Today’s malware is aggressive and not only demands aid of a stealth guard or antimalware solution to protect your data and resources, but too demands PC users use safe online habits. Below are a few safety steps to consider:
In addition to our tips above, below is a comprehensive outline and detailed visual (Figure 3. infographic) for computer users of virtually any experience level from Digital Guardian. The phishing infographic has sourced many trusted firms and government agencies, from the IC3.com to the IRS to communicate phishing methods, forms, and how to prevent becoming a victim.
Figure 3. DigitalGuardian Phishing Infographic (click image to view full infographic)
Last updated: 2026-02-07