Win32/Rovnix
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 83 |
| First Seen: | February 28, 2012 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The Win32/Rovnix family of Trojans is a relative newcomer to the malware world. The original Win32/Rovnix malware infection was first detected in 2011, with new variants popping up every few weeks since the first appearance of this severe threat. Trojans in the Win32/Rovnix family are Trojan droppers, designed to infiltrate a computer system and place certain files on the victim's computer. This characteristic makes Win32/Rovnix highly versatile. ESG security researchers have detected the use of Win32/Rovnix Trojans in association with various malware attacks, including the Carberp family of malware which is the most widely disseminated banking Trojan in the Russian Federation. Any malware infection involving Win32/Rovnix will usually pose a severe threat to the infected computer due to the high degree of control that Win32/Rovnix allows criminals to gain over the infected computer system, as well as the advanced nature of security vulnerabilities that Win32/Rovnix exploits. In order to remove Win32/Rovnix, it is important to ensure that the security programs you have are fully up to date.
Table of Contents
A Basic Description of a Win32/Rovnix Trojan Attack
The Win32/Rovnix family of Trojans makes changes to the NFTS boot sector of the infected hard drive (NFTS stands for New Technology File System). These changes force the modified sector of the infected hard drive to execute other malware and, much like a rootkit or bootkit, it makes malware associated with the Win32/Rovnix very difficult to detect with traditional anti-malware techniques. Win32/Rovnix will usually include a component that forces the infected computer system to reboot in order to ensure that the malware on the infected NFTS boot sector is executed. Since Win32/Rovnix Trojans are usually associated with banking Trojans or other kinds of spy Trojans, they will usually display no symptoms other than a notification from the victim's security software if it is updated to include Win32/Rovnix in its malware database. As soon as Win32/Rovnix runs, Win32/Rovnix will install various malicious files on the infected hard drive, which is executed due to the modifications made to the NTFS boot sector. This malware threat has the capacity to infect both 32-bit and 64-bit operating systems running Windows. The effects of a Win32/Rovnix infection vary greatly depending on the malware associated with Win32/Rovnix. Since Win32/Rovnix is a Trojan dropper, it is very rare to find a stand-alone Win32/Rovnix infection. Instead, Win32/Rovnix will be accompanied by a subsequent malware threat designed to carry out tasks that allow criminals to profit, such as installing a Remote Access Trojan or installing malware designed to steal banking information.
SpyHunter Detects & Remove Win32/Rovnix
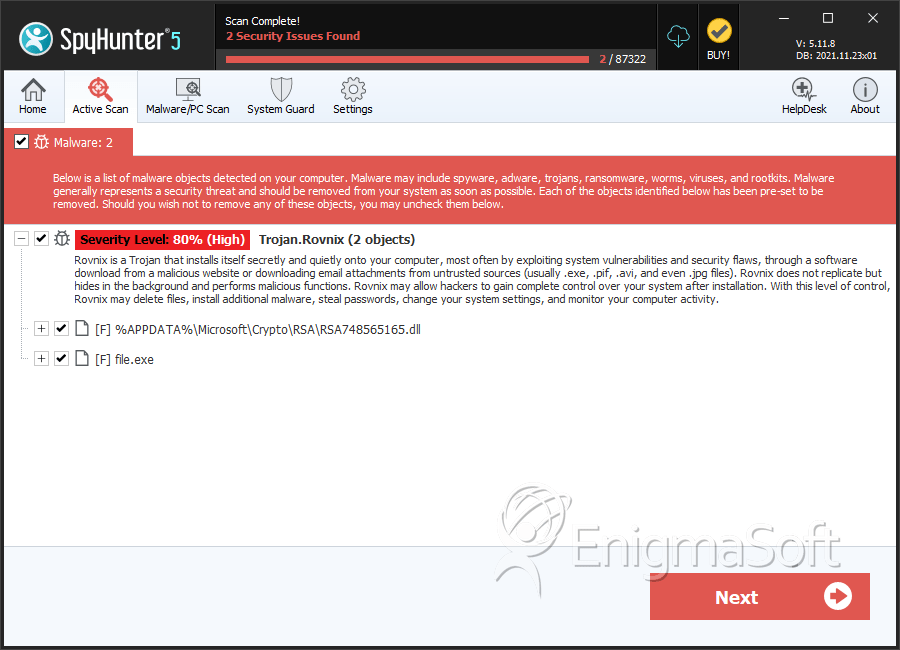
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | RSA748565165.dll | 85e66af1c36c21d1cec76d8dce28ae7e | 3 |
| 2. | file.exe | 56a43042ab259c5a9782d2b26b79c8f7 | 0 |
