Sodinokibi Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 644 |
| First Seen: | June 17, 2019 |
| Last Seen: | May 12, 2023 |
| OS(es) Affected: | Windows |
Sodinokibi Ransomware Image
Sodinokibi Ransomware is a new malware threat that is gaining traction in the cybercriminal circles. Although Sodinokibi operates in the typical ransomware fashion - it infiltrates the victim's computer, uses a strong encryption algorithm to encrypt the files, and demands a payment for their restoration, analyzing its underlying code reveals that it is an entirely new malware strain and not an updated variant of an already existing ransomware.
Table of Contents
Zero-Day Exploit Facilitates First Sodinokibi Attack
Sodinokibi was first detected on April 25 when it was used in an attack that exploited a zero-day Oracle WebLogic Server vulnerability. The severity of the zero-day exploit couldn’t be understated as it allowed the remote execution of code without any of the otherwise required authentication credentials. Oracle issued a patch on April 26, outside of their regular patch cycle, to fix it and to assign the vulnerability as CVE-2019-2725.
Through the exploit the attackers were able to download the Sodinokibi payload to the endpoint machines without the need of any user input. Usually ransomware threats require at least some interaction from victims before the infection can begin. Once inside, Sodinokibi starts encrypting all files with the following extensions:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
For each infected system, Sodinokibi generates a distinct alphanumeric string that can be between 5 and 9 characters long and appends it as a new extension to every successfully encrypted file. The ransomware then creates a text or HTA file with the ransom note in every folder containing encrypted files. The name of the ransom note follows the pattern - [RANDOM EXTENSION]-HOW-TO-DECRYPT.txt. For example, if Sodinokibi has generated a5b892t as an extension for the particular machine, the ransom note will be named a5b892t-HOW-TO-DECRYPT.txt.
This Week in Malware Ep2: Sodinokibi Ransomware is a Ransomware-as-a-Service
Sodinokibi ransomware has the functionality to utilize "cmd.exe" to execute the vssadmin utility to prevent the users from restoring the encrypted files through the default Windows backup mechanics. More specifically, the ransomware executes the following commands to delete the Shadow Volume Copies of the affected files and to disable the Windows startup repair:
C:\Windows\System32\cmd.exe" /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set {default} recoveryenabled No & bcdedit /set {default} bootstatuspolicy ignoreallfailures
Sodinokibi Demands A Hefty Sum For Decryption
Instead of putting their instructions and demands in the body of the ransom note, the criminals behind Sodinokibi direct all affected users towards two websites - a .onion site hosted on the TOR network and one on the public part of the Internet at the domain "decryptor[.]top." The full text of the note is:
"--=== Welcome. Again. ===---
[+] Whats Happen? [+]
Your files are encrypted, and currently unavailable. You can check it: all files on you computer has expansion ----------.
By the way, everything is possible to recover (restore), but you need to follow our instructions. Otherwise, you cant return your data (NEVER).
[+] What guarantees? [+]
Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities - nobody will not cooperate with us. Its not in our interests.
To check the ability of returning files, You should go to our website. There you can decrypt one file for free. That is our guarantee.
If you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause just we have the private key. In practise - time is much more valuable than money.
[+] How to get access on website? [+]
You have two ways:
1) [Recommended] Using a TOR browser!
a) Download and install TOR browser from this site: hxxps://torproject.org/
b) Open our website: hxxp://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/913AED0B5FE1497D
2) If TOR blocked in your country, try to use VPN! But you can use our secondary website. For this:
a) Open your any browser (Chrome, Firefox, Opera, IE, Edge)
b) Open our secondary website: http://decryptor.top/913AED0B5FE1497D
Warning: secondary website can be blocked, thats why first variant much better and more available.
When you open our website, put the following data in the input form:
Key:
-
Extension name:
-----------
-----------------------------------------------------------------------------------------
!!! DANGER !!!
DONT try to change files by yourself, DONT use any third party software for restoring your data or antivirus solutions - its may entail damge of the private key and, as result, The Loss all data.
!!! !!! !!!
ONE MORE TIME: Its in your interests to get your files back. From our side, we (the best specialists) make everything for restoring, but please should not interfere.
!!! !!! !!!"
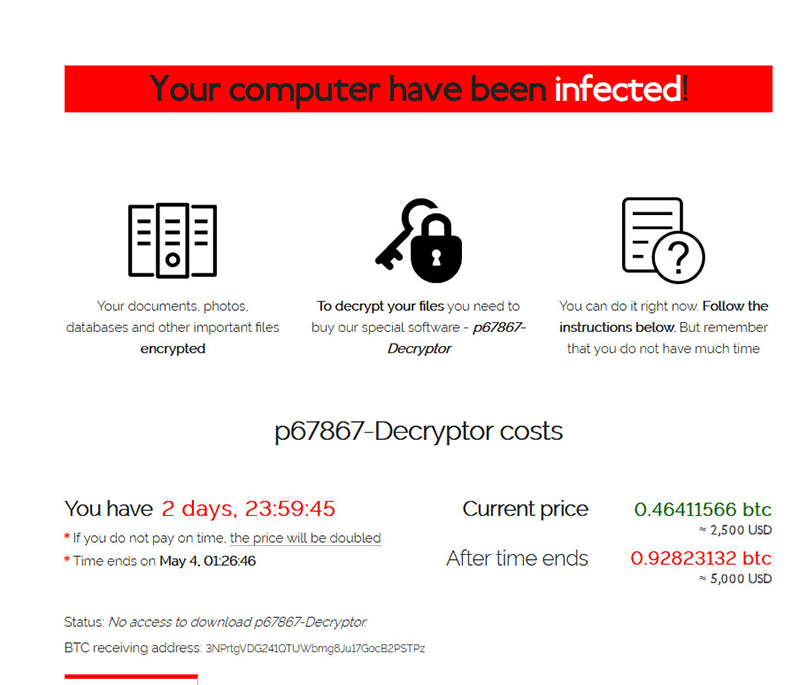
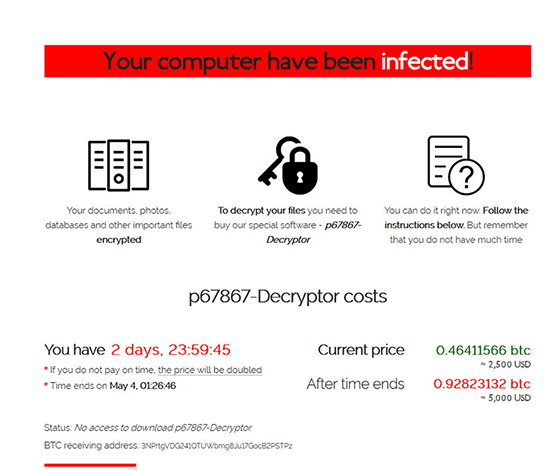
In order to access either of the sites listed in the note, users have to input a specific key that can be found in the text file of the ransom note. Once the code has been entered, they will be taken to the following landing page that will display the specific extension ID code for the computer system and a countdown timer showing that in two days the ransom sum will double in size - from $2500 to $5000, payable in the Bitcoin cryptocurrency. The website recalculates the Bitcoin/USD rate every 3 hours and updates the shown numbers.
Sodinokibi Ransomware Expands Its Reach
Following the patch that shut down the Oracle WebLogic zero-day, researchers observed an increase in the attack vectors employed to distribute the Sodinokibi ransomware. In fact, nearly all of the possible distribution methods have now been attempted:
Spam Email Campaigns - German users were targeted by a malicious spam campaign that carried the Sodinokibi payload in compromised email attachments posing as urgent foreclosure notifications. Another email campaign pretended to be a "New Booking" from Booking.com. In order to access the supposed booking information, users have to open a word file and then allow the execution of macros. Doing so will initiate the Sodinokibi ransomware infection.
Replacing legitimate software downloads - According to TG Soft, an Italian WinRar distributor got its site compromised, resulting in the download of Sodinokibi ransomware instead of the WinRar program.
Hacked Managed Service Providers (MSPs) - Several Managed Service Providers were hacked to distributed Sodinokibi ransomware to their clients. Apparently the attackers used Remote Desktop Services to enter the networks of the affected MSPs and then pushed the ransomware files through the management consoles to the endpoint machines of the clients.
Exploit Kits - Malvertising campaign through ads on the PopCash ad network appears to be redirecting users to websites carrying the RIG Exploit Kit under certain conditions.
It is more than apparent that the Sodinokibi affiliates are getting more ambitious and may now be trying to fill the vacuum that was created as a result of the GandCrab Ransomware operators shutting down their operations and claiming to have generated over $2 billion in ransom payments.
Sodinokibi Ransomware Starts to Play Rough
The threat actors behind the Sodinokibi ransomware ended 2019 on a high note, hitting Travelex, a foreign exchange company based in the UK, and operating in more than 70 countries worldwide. Travelex's websites in around 30 countries had to be taken down on New Year’s Eve, for what appeared to be ‘’planned maintenance’’, but turned out to be a countermeasure to stop the Sodinokibi ransomware from spreading. The attack also affected Travelex's partners, such as HSBC, Barclays, Sainsbury’s Bank, Virgin Money, Asda Money, and First Direct.
Considering the scale of the attack and the nature of Travelex’s business, it was no wonder that the hackers demanded a ransom payment that jumped from $3 million to $6 million in a matter of a few days. The threat actors also decided to show everyone that they mean business by threatening to release stolen sensitive information. Travelex, on the other hand, denied that any info was exfiltrated. A few days later, however, a user on a Russian hacking forum, going by the name Unknown, reiterated the cyber crook’s threats against Travelex and Chinese company CDH Investments. This was done by the publishing of 337MB of data that was allegedly stolen from Artech Information Systems.
This amount of stolen data pales in comparison to the 5GB that were allegedly exfiltrated from Travelex systems. The hackers have vowed that Travelex would pay, one way, or another. Meanwhile, Travelex has stated that the company is cooperating with Metropolitan Police and the National Cyber Security Centre(NCSC) in resolving the case. Travelex has also gone into emergency brand management, promising transparency, and the release of a recovery roadmap.
Sodinokibi doesn’t seem to be showing any signs of slowing down either, hitting a New Jersey Synagogue on January 9th, 2020, and demanding a ransom of $500 thousand under the threat that the threat actors will release sensitive data about the congregants.
No matter if Sodinokibi will manage to take the spot of the top current ransomware, there are certain steps that could help all users build a strong defense against such ransomware attacks. One of the most reliable methods is to create a system backup that is stored on a drive not connected to the network. By having access to such a backup, users can simply restore the files that have been taken hostage by the malware with minimal loss of data. In addition, using a legitimate anti-malware program and keeping it up-to-date could mean that some ransomware threats are stopped even before they have had the chance to execute their malicious coding.
SpyHunter Detects & Remove Sodinokibi Ransomware
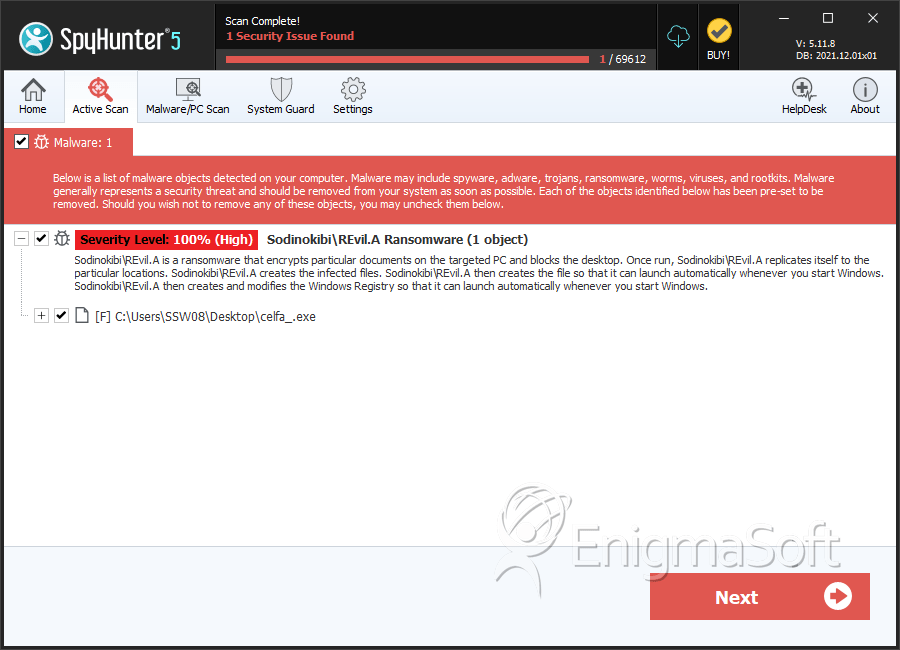
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | celfa_.exe | 9dbb65b1a435a2b3fb6a6e1e08efb2d0 | 11 |

