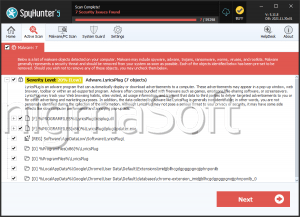
Scanner
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 12,776 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 12,024 |
| First Seen: | December 28, 2010 |
| Last Seen: | February 2, 2026 |
| OS(es) Affected: | Windows |
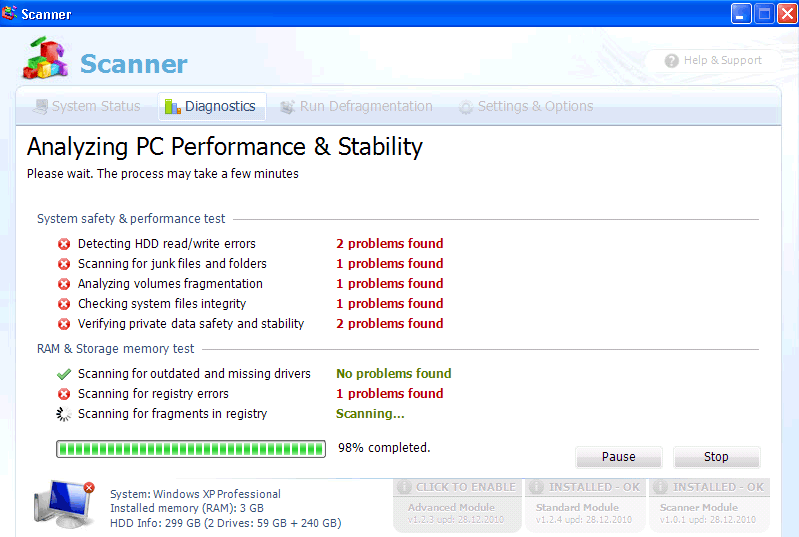
Scanner Image
Scanner is a counterfeit PC optimization tool used to fool Internet users into spending money on a program that does nothing to fix system errors or speed up their computer's performance. The people responsible for Scanner may have chosen a generic name as a way to fool computer users and poison search engine results when Internet users type the term "scanner". Scanner is distributed through the use of various Trojans. Rogue authors use a variety of Trojans to spot security vulnerabilities in an operating system and application. A common method to become a victim of a Trojan infection is to open attachments from spam emails or download software installers from warez websites.
Scanner comes from the FakeSysDef family, the same family of other rogue PC optimization tools as System Defragmenter, Ultra Defragger, HDD Control, Win HDD, Win Defrag, Win Defragmenter, Disk Doctor, Hard Drive Diagnostic, HDD Diagnostic, HDD Plus, HDD Repair, HDD Rescue, Smart HDD, Defragmenter, HDD Tools, Disk Repair, Windows Optimization Center, HDD Low, Hdd Fix, PUP.PC Health Kit.
As Scanner scans your computer, it will display several fake error alerts on the Task bar. Also, whenever you try to run an application or remove a file, Scanner will block your actions and display "critical" error messages. Scanner uses these techniques as a way to protect itself from any anti-virus program running in a user's computer.
Scanner's bogus claims are only a ploy to drive you to purchase its licensed version. Some of the errors it alleges to detect are:
- Data Safety Problem. System integrity is at risk.
- 32% of HDD space is unreadable
- Bad sectors on hard drive or damaged file allocation table
- Read time of hard drive clusters less than 500 ms
- Drive C initializing error
- Requested registry access is not allowed. Registry defragmentation required
- Ram Temperature is 83 C. Optimization is required for normal operation.
- Registry Error - Critical Error
- Hard drive doesn't respond to system commands
- GPU RAM temperature is critically high. Urgent RAM memory optimization is required to prevent system crash
If you make the mistake and use Scanner, it will lead to a black screen designed to look like a Safe Mode background. Another tactic from Scanner is to make it appear that a folder does not contain any content or show the content from a different folder to make you think your hard disk is infected; this usually occurs on C:\Windows:\System32 and is simply an illusion. Scanner's sole purpose is to profit from computer users, and it will hold the computer hostage until it gets what it wants. Do not let Scanner linger any longer in your computer and get a strong anti-spyware program that can restore your computer to its original self.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| AVG | Generic4.AOUF |
| Sunbelt | eZula.CommonElements |
| AntiVir | TR/BHO.iuj.15175 |
| Kaspersky | not-a-virus:AdWare.Win32.EZula.hkp |
| McAfee | Artemis!0A8E0D337A0C |
| AhnLab-V3 | Packed/Win32.Krap |
| Antiy-AVL | Packed/Win32.Krap.gen |
| AntiVir | TR/Agent.ar.15 |
| Kaspersky | Packed.Win32.Krap.ar |
| Symantec | W32.Koobface |
| NOD32 | Win32/Koobface.NDI |
| AVG | Cryptic.BTR |
| BitDefender | Gen:Variant.Kazy.7102 |
| Avast | Win32:FakeSysdef-K |
| NOD32 | a variant of Win32/Kryptik.JJG |
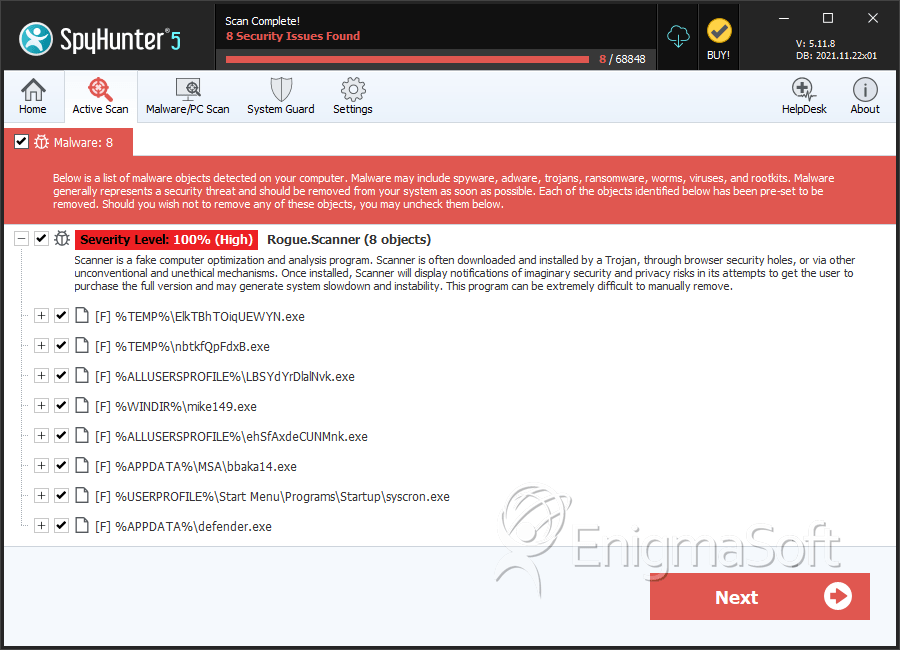
SpyHunter Detects & Remove Scanner
Scanner Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ElkTBhTOiqUEWYN.exe | 92e8a9f7fead7937380b9fb4ee3f4ab9 | 46 |
| 2. | 69c186c533f920719f71ef895a7b36f43b878096075ce55434ab125a7369cdb4.EXE | adf38c340367f9772fa352414984a944 | 34 |
| 3. | LBSYdYrDlalNvk.exe | 9811765f5136490618dfd95f6beae0d1 | 23 |
| 4. | mike149.exe | 7f4db3946a4e554f6ed093b7d678afdf | 14 |
| 5. | ehSfAxdeCUNMnk.exe | 3acf15d92bbe24ddf9b378429bd0842f | 13 |
| 6. | bbaka14.exe | 657e6c7efd339a2efa60c5338ce1ba5b | 11 |
| 7. | defender.exe | a89a714b389f182973f6ebcf2f02c20b | 9 |
| 8. | syscron.exe | 37bf2db6d12d6b53addaf3753e87cb52 | 6 |
| 9. | bbzzkzz17.exe | a60c0eb12877e2bd55d5d8696cdf71e6 | 5 |
| 10. | lsass.exe | 17b67fe8d168577045825638841474a1 | 4 |
| 11. | conhost.exe | 34b5af6dd06b27ca15c938318990aa5a | 3 |
| 12. | 13b9.dll | 330b8b95adb8fd70022827a52d4059a1 | 2 |
| 13. | qykcmjln.exe | 711ca3091ac4d0c371a3ab3aa7627d1a | 1 |
| 14. | 0.08093930418284179.exe | 24723650f47db68061e56eda9a10fd06 | 1 |
| 15. | driverwinx.exe | b4f5ea42cb3404fe522f876ec4e9e445 | 1 |
| 16. | m.23C.tmp.exe | cf27dcc4bf3d8e41fed8c0cc68ab9573 | 1 |
| 17. | cdosys3232.dll | 6118baeb1ef1165b4d272d7d54a06a4f | 1 |
| 18. | Apphlpdm32.dll | c59fd7d299581486ecb47af70d76123c | 1 |
| 19. | api-ms-win-core-file-l1-1-032.dll | f80872715ca54e00238ab56372a65b64 | 1 |
| 20. | hmm.exe | e7a659d0edf6c6f157fe98efcac37e2c | 1 |
| 21. | 14bc9f61-4222-c3b7-11e2-4ce8c3479aa9.dll | a751f32f3a751c20099beb28faef13a9 | 1 |
| 22. | PI9f3_231.exe | a965b83a1b2c1eca6a11ac36d14eaa3c | 1 |
| 23. | 4886746.exe | 2073e7be4ece0e69d59a1ebb492677ac | 1 |
| 24. | DCjap4QWgPf.exe | 43f6528114a4dbe0a77720b17c4dade8 | 1 |
| 25. | dwm.exe | e303f81216f6544ae7ae093799de4aff | 1 |
| 26. | qp4iReRF.exe | 58ad6a013e1747137018ca3b66c1571e | 0 |
| 27. | qYfoKD6PzadEEhF.exe | 969A26E89B4F13ADF66226B82FADB6C9 | 0 |
| 28. | tSfkTNduxrPpGPr.exe | E4CD92C1495368A2FB0AC287FA44C0DF | 0 |