Phobos Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1,621 |
| First Seen: | July 24, 2009 |
| Last Seen: | July 16, 2020 |
| OS(es) Affected: | Windows |
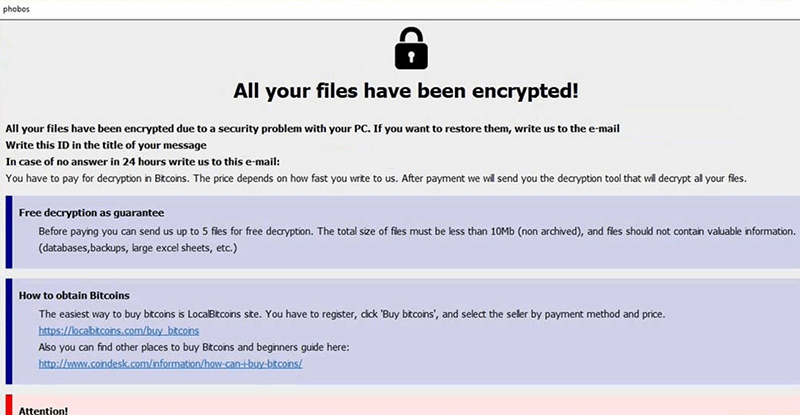
Phobos Ransomware Image
The Phobos Ransomware is an encryption ransomware Trojan that was first observed on October 21, 2017. The Phobos Ransomware is being used to target computer users in Western Europe and the United States and delivers its ransom messages in English to the victims. The main way in which the Phobos Ransomware is being distributed is through the use of spam email attachments, which may appear as Microsoft Word documents that have enabled macros. These macro scripts are designed to download and install the Phobos Ransomware onto the victim's computer when the corrupted file is accessed. It is likely that the Phobos Ransomware is an independent threat since it does not seem to belong to a vast family of Ransomware as a Service (RaaS) provider.
This Week in Malware Ep2: Phobos Ransomware is Targeting Western Europe & U.S.
Table of Contents
How to Identify the Files Encrypted by the Phobos Ransomware
Like most other, similar threats, the Phobos Ransomware works by encrypting the victim's files by using a strong encryption algorithm. The encryption makes the files inaccessible, allowing the Phobos Ransomware to take the victim's data hostage until the victim pays a ransom. The Phobos Ransomware will target the user-generated files, which may include files with the following extensions:
.aif, .apk, .arj, .asp, .bat, .bin, .cab, .cda, .cer, .cfg, .cfm, .cpl, .css, .csv, .cur, .dat, .deb, .dmg, .dmp, .doc, .docx, .drv, .gif, .htm, .html, .icns, .iso, .jar, .jpeg, .jpg, .jsp, .log, .mid, .mp3, .mp4, .mpa, .odp, .ods, .odt, .ogg,.part, .pdf, .php, .pkg, .png, .ppt, .pptx, .psd, .rar, .rpm, .rss, .rtf, .sql, .svg, .tar.gz, .tex, .tif, .tiff, .toast, .txt, .vcd, .wav, .wks, .wma, .wpd, .wpl, .wps, .wsf, .xlr, .xls, .xlsx, .zip.
As can be noticed from the list above, the Phobos Ransomware targets documents, media, images, and other commonly used files, and encrypts them using the AES 256 encryption. After the victim's files have been encrypted, the Phobos Ransomware will communicate with its Command and Control server to relay data about the infected computer, as well as receive configuration data. The Phobos Ransomware will identify the files encrypted by its attack by changing their names to the following string:
..ID[eight random characters].[ottozimmerman@protonmail.ch].PHOBOS
The Phobos Ransomware’s Ransom Demands
The Phobos Ransomware delivers a ransom note in the form of a program window with the title 'Your files are encrypted!' after the victim's files have been encrypted and renamed. This program window includes the logo 'PHOBOS' in one of the corners of the window and claims that the victim must pay a ransom to restore the infected files. The ransom note that the Phobos Ransomware displays during its attack on a victim's computer reads:
'All your files are encrypted
Hello World
Data on this PC runed into useless binary code
To return to normal, please contact us by this email: OttoZimmerman@protonmail.ch
Set topic of your message to 'Encryption ID:[8 random characters]'
Interesting facts:
1. Over time, the cost increases, do not waste your time
2. Only we can help you, for sure, no one else.
3. BE CAREFUL If you still try to find other solutions to the problem, make a backup copy of the files you want to experiment on, a. play with them. Otherwise, they can be permanently damaged.
4. Any services that offer you help or just take money from you and disappear, or they will be intermediaries between us, with inflated value. Since the antidote is only among the creators of the virus
PHOBOS'
Dealing with the Phobos Ransomware
Unfortunately, once the Phobos Ransomware encrypts the files, it becomes impossible to restore the affected files without the decryption key. Because of this, it is important to take preemptive measures to ensure that your data is well protected. The best protection against threats like the Phobos Ransomware is to have a reliable backup system. Having backup copies of all files means that the victims of the Phobos Ransomware attack can restore their data after an attack quickly and reliably.
Update January 4th, 2019 — 'Job2019@tutanota.com' Ransomware
The 'Job2019@tutanota.com' Ransomware is categorized as a slightly updated variant of the Phobos Ransomware that was released in October 2017 initially. The 'Job2019@tutanota.com' Ransomware appears a little more than a year later with no significant updates to show. The 'Job2019@tutanota.com' Ransomware was identified in January 2019 and seems to spread the same way as its predecessor. The threat payload is delivered through macro scrips embedded into Microsoft Word files that you might see attached to seemingly official updates from social media and online stores. The 'Job2019@tutanota.com' Ransomware is likely to create a temporary folder on the primary system drive and load a process with a random name in the Task Manager. The 'Job2019@tutanota.com' Ransomware Trojan is configured to delete the Shadow Volume snapshots before encoding your photos, text, music and video. The new variant is known to promote decryption services via two email accounts, namely — 'Job2019@tutanota.com' and 'Cadillac.407@aol.com.' The ransom note is styled as a small program window colored in the same shade of blue as the default Windows 10 theme. The Trojan is reported to show a window named 'Your files are encrypted!.' The window seems to be loaded from 'Phobos.hta,' which is dropped to the Temp folder on Windows and reads:
'All your files are encrypted
Hello World
Data on this PC turned into a useless binary code
To return to normal, please contact us by this e-mail: OttoZimmerman@protonmail.ch
Set topic of your message to 'Encryption ID: [8 digit number]
1. Over time, the cost increases, do not waste your time
2. Only we can help you, for sure, no one else.
3. BE CAREFUL !!! If you still try to find other solutions to the problem, make a backup copy of the files you want to experiment on, and play with them. Otherwise, they can be permanently damaged
4. Any services that offer you help or just take money from you and disappear, or they will be intermediaries between us, with inflated value. Since the antidote is only among the creators of the virus'
Some variants of the 'Job2019@tutanota.com' Ransomware are said to produce a simple dialog box instead of the 'Your files are encrypted!' screen that says:
'All your files are encrypted
To decrypt your files, contact us using this e-mail: [email address] Please set topic 'Encryption ID: [8 digit number].
We offer free decryption of your test files as a proof. You can attach them to your e-mail, and we'll send you decrypted ones.
Decryption price increases over time, hurry up and get discount.
Decryption using third parties may lead to scam or increased price.'
The affected data may receive one of two extensions — '.ID-[8 digit number].[Job2019@tutanota.com].phobos' or '.ID-[8 digit number].[Job2019@tutanota.com].phobos.' For example, 'Sabaton-Carolus Rex.mp3' may be renamed to 'Sabaton-Carolus Rex.mp3.ID-91651720.[Job2019@tutanota.com].phobos' and 'Sabaton-Carolus Rex.mp3.ID-68941751.[Job2019@tutanota.com].phobos.' We recommend avoiding negotiations with the ransomware actors because you may not receive a decryptor. You should use data backups to rebuild your files structure and run a complete system scan to remove the resources that may have been left by the 'Job2019@tutanota.com' Ransomware.
Aliases
5 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| CAT-QuickHeal | Win32.Trojan.Obfuscated.gx.3 |
| AVG | Downloader.Obfuskated |
| Prevx1 | Covert.Sys.Exec |
| Microsoft | TrojanDownloader:Win32/Agent.ZZC |
| AntiVir | TR/Crypt.XPACK.Gen |
Phobos Ransomware Screenshots
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | rrr_output7251B30.exe | b3b69dabf55cf7a7955960d0c0575c27 | 72 |
| 2. | rrr_output713F8B0.exe | 29d51846a76a1bfbac91df5af4f7570e | 64 |
| 3. | rrr_output8F2121F.exe | 5d533ba319fe6fd540d29cf8366775b1 | 63 |
| 4. | rrr_outputEE209BF.exe | 3677195abb0dc5e851e9c4bce433c1d2 | 59 |
| 5. | rrr_output89A8FEF.exe | 75d594f166d438ded4f4f1495a9b57b6 | 51 |
| 6. | rrr_output354CF0.exe | 360f782f4a688aba05f73b7a0d68ef43 | 51 |
| 7. | rrr_output7492970.exe | 376625a4a031656f0667723cd601f333 | 49 |
| 8. | yvihok.exe | 00db62e1b519159b0c20c00c2e97288b | 46 |
| 9. | rrr_outputE17E73F.exe | f9ef51967dcb4120df9919ac5423bc13 | 39 |
| 10. | rrr_outputDBB65DF.exe | cd16baef95d0f47387e7336ceab30e19 | 32 |
| 11. | rr_output89224BF.exe | fb9df7345520194538db6eef48fb0652 | 31 |
| 12. | rrr_outputF71089F.exe | 3d5ec29f0374fce02c5816c24907cafe | 27 |
| 13. | rr_output5F98E0.exe | 559973f8550ce68f7bae9c3e3aaa26aa | 21 |
| 14. | rrr_outputF0DA6CF.exe | f653bc6e6dda82e487bfc4bc5197042b | 21 |
| 15. | rr_output12C4770.exe | 45a9b21bd51f52db2b58ae7ae94cd668 | 18 |
| 16. | rrr_output940674F.exe | b76fbb1b51118459d119d2be049d7aa5 | 18 |
| 17. | rrr_output3A9CF40.exe | 6fa328484123906a6cfbbf5c6d7f9587 | 10 |
| 18. | rrr_outputD25868F.exe | b43db466c60b32a1b76fe3095851d026 | 8 |
| 19. | rr_output12F8B00.exe | 0f9f6b73beef0dba5d4f348da8393379 | 7 |
| 20. | rrr_output43f40e0.exe | d1258b39c924746ed711af72e35e8262 | 5 |
| 21. | ac044b97c4bfecc78ffa3efa53ffd0938eab2d04e3ec983a5bbb0fd5059aaaec.exe | 26c23da3b8683eb3a727d54dcb8ce2f0 | 5 |
| 22. | rr_output516C100.exe | e8dedea6ce819f863da0c75c9d9bccde | 4 |
| 23. | rrr_output8f0a14f.exe | 52e6b8ee647e675969d36b69070d1047 | 4 |