Matrix Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 16,954 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 2,830 |
| First Seen: | December 2, 2016 |
| Last Seen: | September 18, 2023 |
| OS(es) Affected: | Windows |
PC security researchers observed the Matrix Ransomware, an encryption ransomware Trojan, on April 3, 2018. Victims may have the Matrix Ransomware delivered to their machines through the use of spam email messages, which will contain corrupted file attachments, which use macro scripts to download and install the Matrix Ransomware onto the victim's computer. The Matrix Ransomware has two versions, both used to encrypt the victim's files, and then a ransom should be paid by the victims to be given a decryption key. This behavior is observed in most encryption ransomware Trojans. The Matrix Ransomware makes it easy to recognize the files it encrypts because the Matrix Ransomware will add the file extension '.matrix' to the files' names.
Table of Contents
What are the Consequences of a Matrix Ransomware Attack
Trojans like the Matrix Ransomware use strong encryption algorithms to make the files inaccessible. The Matrix Ransomware will target the user-generated file in its attack, which may include files with the following extensions:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
After the Matrix Ransomware has finished encrypting the files, the Windows operating system will not recognize these files, and they will appear as blank icons and display error messages when the PC user attempts to open them. The Matrix Ransomware will demand that the victim contacts its operators via email to pay a substantial ransom in exchange for the decryption key. Different variants of the Matrix Ransomware use different contact emails, and the following email addresses have been associated with the Matrix Ransomware:
files4463@tuta.io
files4463@protonmail.ch
files4463@gmail.com
restorfile@tutanote.com
restorfile@protonmail.com
restorfile@qq.com
The Matrix Ransomware delivers its ransom note in the form of an HTA file that displays the following message on the infected computer:
'WHAT HAPPENED WITH YOUR FILES?
Your documents, databases, backups, network folders and other important files are encrypted with RSA-2048 and AES-128 ciphers. More information about the RSA and AES can be found here:
h[tt]p://en.wikipedia[.]org/wiki/RSA (cryptosystem)
h[tt]p://en.wikipedia[.]org/wiki/Advanced Encryption Standard
It means that you will not be able to access them anymore until they are decrypted with your personal decryption key! Without your personal key and special software data recovery is impossible! If you will follow our instructions, we guarantee that you can decrypt all your files quickly and safely!
If you want to restore your files, please write us to the e-mails: [STRING OF EMAILS] In subject line of your message write your personal ID: [EDITED]
We recommend you to send your message ON EACH of OUR 3 EMAILS, due to the fact that the message may not reach their intended recipient for a variety of reasons! Please, write us in English or use professional translator! If you want to restore your files, you have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
If you prefer live messaging you can send us Bitmessages from a web browser through the webpage h[tt]ps://bitmsg[.]me.'
Dealing with the Matrix Ransomware
Unfortunately, once the Matrix Ransomware encrypts the files, they will no longer be recoverable. Because of this, it is necessary that computer users take steps to ensure that they have protected their data from these threats preemptively. The best protection against threats like the Matrix Ransomware is to have file backups, which will give the victims the opportunity to recover their files.
Update November 14th, 2018 — Matrix-FASTA Ransomware
The Matrix-FASTA Ransomware is a variant in the Matrix family, a family of ransomware threats that emerged in April 2018, and have seen various variants since their initial release. The Matrix-FASTA Ransomware, like other Matrix variants, is designed to encrypt the victims' files and then demand a ransom payment from the victim. It is crucial that computer users take steps to protect their PCs from the Matrix-FASTA Ransomware and similar attacks.
How the Matrix-FASTA Ransomware Trojan Works
The Matrix-FASTA Ransomware is typically delivered to the victim's computer through the use of spam email attachments. Once the Matrix-FASTA Ransomware has been installed onto the victim's computer, the Matrix-FASTA Ransomware will encrypt the user-generated files that it finds on the victim's computer, which may include files with the following file extensions:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The Matrix-FASTA Ransomware attack will damage the targeted data in a way that it will not be recoverable without the decryption key, which means that it may be lost permanently. The criminals will attempt to force the victim to pay a ransom in exchange for the data compromised by the Matrix-FASTA Ransomware attack.
How the Matrix-FASTA Ransomware is Delivered to Its Victims
The Matrix-FASTA Ransomware variant was first observed on November 14, 2018. There have been several variants in this ransomware family that have been released in 2018. Like other Matrix variants, the most common way in which the Matrix-FASTA Ransomware is delivered to victims' computers through spam email attachments, which use embedded macro scripts to download and install the Matrix-FASTA Ransomware onto the victim's computer. The Matrix-FASTA Ransomware ransom note, which demands payment from the victim, asks the victim to contact the criminals via the email address 'fastbk@qq.com' to restore the affected data. The Matrix-FASTA Ransomware marks the files encrypted by the attack by adding the file extension '.FASTA' to each file encrypted by the attack. The Matrix-FASTA Ransomware also will rename the files encrypted by the attack by replacing the files' names with the Matrix-FASTA Ransomware email contact address and a string of encrypted characters. A typical Matrix-FASTA Ransomware ransom is in the 300 to 1,000 USD range.
Protecting Your Data from Threats Like the Matrix-FASTA Ransomware
The best protection against threats like the Matrix-FASTA Ransomware is to have file backups stored in a safe location. Security specialists advise computer users to have backup copies of their data stored either on the cloud or an external memory device. Apart from file backups, computer users also should use a security program to intercept the Matrix-FASTA Ransomware infection or remove it once it has been installed.
Update October 22nd, 2018 — Matrix-GMPF Ransomware
The Matrix-GMPF Ransomware is categorized as a slightly modified version of the Matrix Ransomware that was released in April of 2018. The new variant was reported on October 22nd, 2018 and added to AV databases. The cyber-threat is named after the file marker shown to compromised users — '.GMPF.' Earlier versions featured similar names and included the Matrix-THDA Ransomware and the Matrix-ITLOCK Ransomware. The Matrix-GMPF Ransomware is crafted to use the AES and RSA ciphers and make the data on the infected devices unreadable. Then, the users are shown a text file called '#GMPF-README#.txt' and asked to send an email to the 'GetMyPass@qq.com' email account. The threat is programmed to send the decryption key to the programmers via the TOR Network and prevent third parties from uncovering a way to decrypt the affected data. You can recognize the encrypted files by looking at their names. The Matrix-GMPF Ransomware Trojan uses the model — [GetMyPass@qq.com]..GMPF — to mark the encrypted objects. For example, 'Hanuman.pptx' may be renamed to [GetMyPass@qq.com].Z2VuZXJp-YwdGV89t.GMPF.' As mentioned above, the ransom message is provided as '#GMPF-README#.txt,' which you can load in Microsoft's Notepad and read the following:
'WHAT HAPPENED WITH YOUR FILES?
Your documents, databases, backups, network folders and other important files are encrypted with RSA-2048 and AES-128 ciphers. More information about the RSA and AES can be found here:
h[tt]p://en.wikipedia[.]org/wiki/RSA (cryptosystem)
h[tt]p://en.wikipedia[.]org/wiki/Advanced Encryption Standard
It means that you will not be able to access them anymore until they are decrypted with your personal decryption key! Without your personal key and special software data recovery is impossible! If you will follow our instructions, we guarantee that you can decrypt all your files quickly and safely!
If you want to restore your files, please write us to the e-mails: getmypass@qq.com'
The threat authors switch email accounts often as a way to keep their operations running and avoid raising alarms with email service providers. It is advised to boot data backups to recover from potential attacks. Detection names for the Matrix-GMPF Ransomware include:
Generic.Ransom.Matrix.B38FC644
Ransom.Agent!8.6B7 (CLOUD)
Ransom.Matrix.S3765495
Ransom_MATRIX.THAOOBAH
Troj/Matrix-K
W32/Agent!tr
W32/Generic.AC.41B59B!tr
malware (ai score=100)
Update December 20th, 2018 — Matrix-PRCP Ransomware
Security researchers pinpointed a new variant of the Matrix Ransomware in the last few days before Christmas 2018 called Matrix-PRCP Ransomware. The new offshoot of Matrix applies the .PRCP extension to the encrypted files.
The ransom note is contained in a file named "#README_PRCP#.rtf." The email used by the authors of the new variant that victims can use to contact them is radrigoman@protonmail[.]com. It appears this email is also used in the way the ransomware scrambles files. The Matrix-PRCP Ransomware renames all the files that it has encrypted by using the following pattern '[radrigoman@protonmail.com].[random character string]-[random character string].PRCP.
Update January 14th, 2019 — Matrix-GRHAN Ransomware
The Matrix-GRHAN Ransomware is a minor update to the Matrix line of encryption Trojans that began appearing in April 2018. The Matrix-GRHAN Ransomware differs very slightly compared to earlier iterations, and the only notable difference is that it uses a new rename pattern. The threat applies a modified AES-256 cipher to images, audio, video, text and databases. The files that are processed by the Matrix-GRHAN Ransomware are represented by generic white icons and feature names following the model '[greenelephan@qq.com]..GRHAN.' For example, 'Jotunheim.docx' may be renamed to '[greenelephan@qq.com].VC6NJ9-XWI88P.GRHAN' and the users are unable to recover from the attack by using the Shadow Volume snapshots. The threat at hand is known to use the Shadow Volume Service and delete the System Restore points, as well as recently created Shadow Volume snapshots. The Matrix-GRHAN Ransomware is reported to drop '!README_GRHAN!.rtf' to the infected systems and offer the following message:
'WHAT HAPPENED WITH YOUR FILES?
Your documents, databases, backups, network folders and other important files are encrypted with RSA-2048 and AES-128 ciphers. More information about the RSA and AES can be found here:
h[tt]p://en.wikipedia[.]org/wiki/RSA (cryptosystem)
h[tt]p://en.wikipedia[.]org/wiki/Advanced Encryption Standard
It means that you will not be able to access them anymore until they are decrypted with your personal decryption key! Without your personal key and special software data recovery is impossible! If you will follow our instructions, we guarantee that you can decrypt all your files quickly and safely!
If you want to restore your files, please write us to the e-mails: greenelephan@qq.com'
The Matrix-GRHAN Ransomware Trojan may interfere with the work of database managers and some backup managers. The cyber-threat is designed to infiltrate and run on company networks, server farms and small business networks. It is recommended to make sure that there are no open ports and services that are connected to the Internet over insecure connections. It is not recommended to contact the ransomware operators via 'greenelephan@qq.com' and other channels that may be associated with the Matrix-GRHAN Ransomware. You should use clean backups and run complete system scans if you have been infected with the Matrix-GRHAN Ransomware. The removal of this threat should be facilitated by certified experts and trusted security products.
SpyHunter Detects & Remove Matrix Ransomware
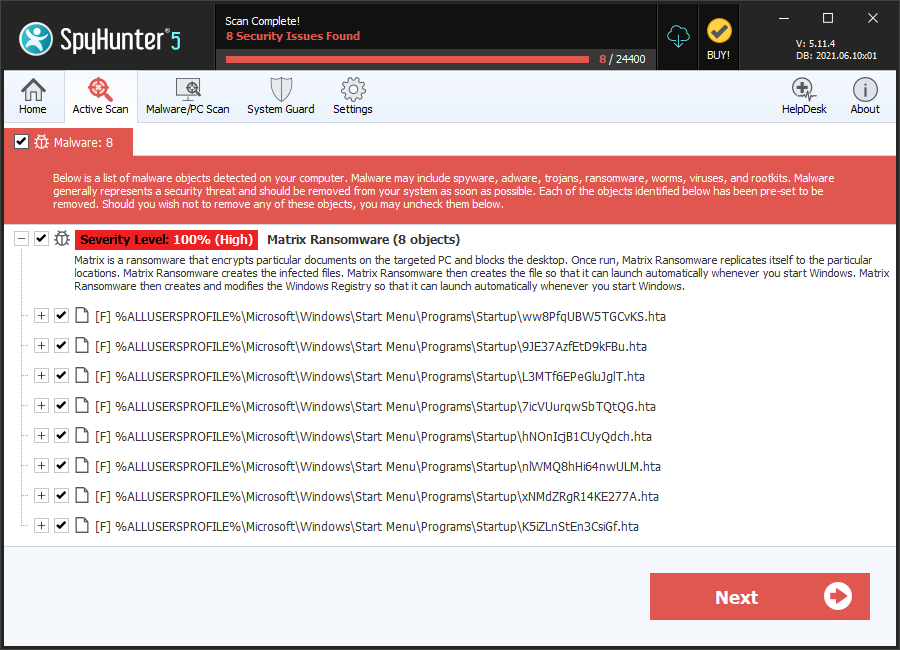
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ww8PfqUBW5TGCvKS.hta | 357ebe43792548be1256e67a8813ff36 | 70 |
| 2. | 9JE37AzfEtD9kFBu.hta | b0bd20328f7f8821206c874dde831b79 | 54 |
| 3. | L3MTf6EPeGluJglT.hta | b0f28cf9f05c5e25c20f04013fb6a696 | 46 |
| 4. | 7icVUurqwSbTQtQG.hta | c01b3084158ead651be3d6b006c31ddb | 43 |
| 5. | hNOnIcjB1CUyQdch.hta | b9649f26c37cb853b6d299a28db545bb | 34 |
| 6. | nlWMQ8hHi64nwULM.hta | 31cbcf227f72ed21e6c4464f507de6df | 34 |
| 7. | xNMdZRgR14KE277A.hta | a927a6983d9836760c9d0d185152f480 | 28 |
| 8. | K5iZLnStEn3CsiGf.hta | dbfa225d7f12f37f0174d8932e1caba2 | 27 |
| 9. | N9j8i4izeKqJNWw0.hta | e7d1927faef12edf45a3638cf3f8b8b2 | 26 |
| 10. | Bwbs92eNScj8boVR.hta | c71f3eefb61b981954235bf0076d3f0b | 25 |
| 11. | MwcHhEltJeCQfIX3.hta | e84253cda0b507e1349de162a14e3f5e | 25 |
| 12. | BjtY2tiEvEPe3Ry2.hta | 1cf10df2bb9a5b11801fc4274a76a08a | 25 |
| 13. | MLJbvD3qyJb4zIH0.hta | e43fa0ca398b13ac402214e07b4c48e7 | 25 |
| 14. | CHnXlFujjUUky3bQ.hta | 65e45e01bb979e4a7d66fa6b4a43b182 | 20 |
| 15. | EiQFMggycluaM2KN.hta | 88cf3be3d48adc65412d9ccc8675c723 | 20 |
| 16. | xicv4xv3q21J45Wa.hta | c38d23e5779785cc13b1b92b1e4ab7c7 | 19 |
| 17. | bySuMRhTosRxNSVK.hta | 8c5b40e05cefde9fc15ff3e37f02c7b7 | 18 |
| 18. | 6GwJaYZhHMU12p5k.hta | f5ce39d833f444821c983e4729388c55 | 18 |
| 19. | uuHw7WEyukJ53uIF.hta | 9a3a780e1509f2f7ebd69bd4b5fd9e96 | 18 |
| 20. | xz8GmuIomid3j8xA.hta | 8a7aee85ee76f85128b6cec0b0a39658 | 17 |
| 21. | ebIxNHzdfyPxdNEi.hta | 2ba8f7c88debee948b54f4d278799c27 | 17 |
| 22. | 8J8Nq13d3SEnLFg5.hta | b0139d446e979eeac438789d89035013 | 17 |
| 23. | LARmeOIF7pqvE2Id.hta | 63a90494f3dbde0be1c6e966568e6bb9 | 17 |
| 24. | EPf93mYqDG8pOCfZ.hta | 5a6a4836670229fc3b83fa210c649d1b | 16 |
| 25. | ZDc4hrKMsjl8VvzD.hta | bac966c75a8034f4e4d9c3aef5227913 | 16 |
| 26. | 075f86e2db93138f3f3291bc8f362e5f54dfdeeb98b63026697b266fbebddb00 | 66c7ca7b642a531ea1f9bf611ef8f42b | 3 |
| 27. | bc39998bad128866015b7f0a2e160afba3629b3ef83fe84e664e9e117beeef75 | e4e2aa6df9a5ca1e7942472a13bcd79d | 2 |

