CoronaVirus Malware
 With the world facing the unfortunate Coronavirus (COVID-19) pandemic, cybercrooks and hackers have taken to the techie world to exploit the virus in many ways. One particular way that hackers are leveraging the popularity and hyped uncertainty of the Coronavirus is by distributing malware threats. Such malware threats, some in the form of ransomware such as CoronaVirus Ransomware, are all playing on the worldwide hysteria surrounding Coronavirus.
With the world facing the unfortunate Coronavirus (COVID-19) pandemic, cybercrooks and hackers have taken to the techie world to exploit the virus in many ways. One particular way that hackers are leveraging the popularity and hyped uncertainty of the Coronavirus is by distributing malware threats. Such malware threats, some in the form of ransomware such as CoronaVirus Ransomware, are all playing on the worldwide hysteria surrounding Coronavirus.
Table of Contents
Coronavirus Malware Threats come in many Different Forms
Among the malware threats utilized in the efforts by hackers to leverage the popularity and scary factors of Coronavirus, apart from CoronaVirus ransomware, we have seen the Emotet trojan horse, the AZORult information-stealer, Lokibot threat, KPOT, Vicious Panda, Trickbot, BlackWater, and the Remcos malware all being actively spread. With many of these threats coming out of the woodwork by hackers who seek to have such threats gain popularity along with the Coronavirus, we have informally grouped them in the family of Coronavirus Malware.
Not only are cybercrooks spreading malware leveraging the popularity of Coronavirus, but they are also launching multiple campaigns designed to lure inquiring minds of the Coronavirus. Through these channels, cybercrooks look to get the attention of gullible computer users so they may install their malware. Such cases may range from simple spam emails that may tout the latest scary news about Coronavirus spreading, or a phishing site created to trick computer users out of their personal information. The possibilities are virtually endless.
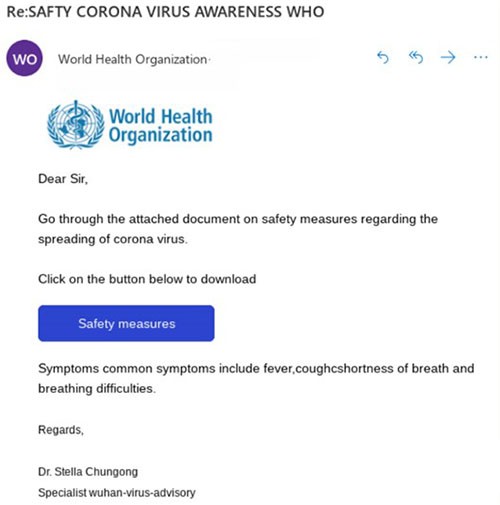
Example of fake Coronavirus COVID-19 email claiming to be from World Health Organization
Coronavirus malware threats may consist of different variations that, for the most part, share a common goal of being able to either steal personal data from victimized computer users or leverage computer users in a way to gain monetarily.
With the Coronavirus being a global health crisis where thousands of people have either contracted the virus or fear that if appropriate action is not taken – they too may end up on the list of the next Coronavirus victims. Hackers thrive off of events such as these where there is a global health crisis that’s highlighted in just about every news cycle, news website, or social media outlet in existence. In knowing such, the family of Coronavirus Malware is here to stay and grow into unseen epidemics that affect the tech world in ways we have yet to see.
A Trend Micro analysis for the first quarter of 2020 shows coronavirus-related malware and spam attacks were mostly aimed at the Europe, Middle East and Africa Regions (EMEA). Other areas of far smaller activity include the Asia Pacific Region (APAC), Latin America Region (LAR) and the North American Region (NABU).

Source: TrendMicro.com
The World is Facing a Surge of COVID-19-Themed Cyber Attacks
The current global pandemic crisis appears to bring out the worst of humanity in the digital world. Even the threat of a massive outbreak doesn't slow cybercriminals down, as the current surge of cyber attacks, scams, phishing campaigns, new malware, and more goes to show.
What may look like an innocent-looking email from your supervisor may hide an attachment that holds a poisoned payload. The massive move toward working from home for millions of employees around the world has sparked an increase in attacks that aim at tricking people. Credentials theft is also on the rise, according to security researchers.
USA Today Video: Coronavirus symptoms, spread, and treatment explained
Proofpoint's Sherrod DeGruppo, head of threat research, shared they had never seen anything like this before. There are campaigns with volumes of up to hundreds of thousands of emails that make use of the coronavirus crisis to proliferate digital infections. The pandemic has created the perfect situation for cyber attacks, with millions of people now working from home. The unfamiliar, new environment with far less secure circumstances made it necessary for the implementation of new organizational policies.
The new avenue of attack opens the way for malicious actors to use phishing emails and massive social engineering efforts to gain access to sensitive information from employees.
Companies are more vulnerable during the crisis, as employees will not have the same level of protection they may have within their workplace. When people have experience working remotely with properly configured computers or equipment, experience plays a significant role in operational security. The current situation allows the use of people's fears of COVID-19, making people more vulnerable to opening malicious attachments and links. Other possible attempts at scamming may include fake crowdfunding pages set up for Coronavirus victims.
"This Week in Malware: A CoronaVirus Malware Alert" video discusses how hackers are continually leveraging the COVID-19 epidemic to spread malware, phishing emails, fake apps, fake websites, and malware-laced advertisements.
With Italy facing the pandemic with massive infections and reported deaths, threat actors continue using the crisis to their advantage. A spam campaign was reported as active and aimed at Italian citizens. The emails are written in Italian, claiming to have important information on Coronavirus precautions. The spam emails come with an attached document allegedly prepared by the World Health Organization, but the attachment contains a Trojan instead.
Healthcare Organizations are Susceptible to Ransomware
As the Brno University Hospital found out earlier this month, healthcare organizations are very vulnerable to ransomware attacks, as these may shut down their operations temporarily. Similar attacks occurred before the pandemic, but the current situation makes them especially dangerous. The Brno University Hospital fell victim to an unspecified attack aimed at the hospital systems that forced them to take urgent measures. The medical facility is one of 18 Czech centers used to test patients for COVID-19 infections. The increased load of patients in medical facilities across the globe makes hospitals particularly vulnerable in this time of crisis.
Stepping up on Warnings against Cyber Attacks
The potential of increased attacks has prompted various organizations to warn users and businesses to step up their vigilance. The French public-private cybersecurity alliance warned businesses to be on alert for fake emails imitating orders or bank transfers, phone calls aimed at financial account information, and more.
The US Department of Homeland Security also issued an alert warning about the COVID-19 pandemic increasing cyber threats. They also warned that emails with malicious attachments or links to fraudulent websites might trick victims into revealing sensitive information. Emails claiming to be from the Center for Disease Control and Prevention or experts that have information about the virus might be highly suspect. Scammers may even end up offering fake vaccines and medical products that claim to help with the illness.
At this time, all the cyber schemes related to the pandemic appear to be financially motivated, so users should keep in mind that new plans and techniques may arise during the crisis.
New Threats are Emerging during the Pandemic:
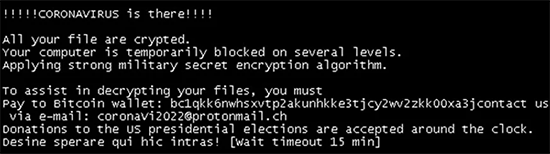
Coronavirus Ransomware – The Coronavirus Ransomware, also known as CoronaVi2022, is a newly made file-locker making the rounds during the pandemic. This threat encrypts data, but also overwrites the contents of the Master Boot Record (MBR) on affected drives. The extra step may block the infected system from loading up the operating system. Instead of booting it up, it shows a copy of the Coronavirus Ransomware ransom note. It was reported to spread through a fake Wise Cleaner site, a website that promoted an alleged system optimization tool.
Vicious Panda – A currently unknown Advanced Persistent Threat (APT) group. They are using the chaos surrounding the Covid-19 pandemic to spread an unknown malware. The campaign was dubbed Vicious Panda by security researchers. Tools used in the attack were linked to Chinese threat actors in past campaigns and aimed at Mongolian citizens.
AZORult – The AZORult malware was first spotted in the wild in 2016. It is an information stealer that gets away with cookies, ID/passwords, browsing history, cryptocurrency information, and more. AZORult is currently used in fake COVID-19 statistical maps online to fool users. Johns Hopkins University's interactive dashboard of the infections and deaths was recently being used in malicious websites with infected content.
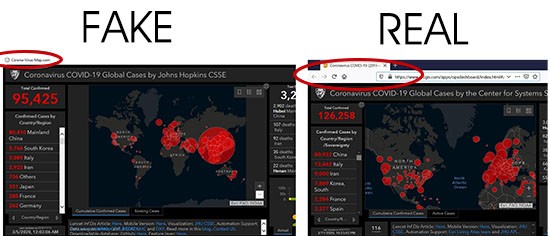
Snapshot image of the Johns Hopkins Coronavirus data map, available at coronavirus.jhu.edu.
The image above is of the legitimate Johns Hopkins University's interactive dashboard of Coronavirus COVID-19 infections around the globe. However, hackers are exploiting the same interactive map and utilizing it on various phishing and malicious websites to trick computer users in a way that they may either relinquish personal data or download malware.
Difference of fake map versus real map. The fake map requires a download and the real map is loaded directly from the legitimate Johns Hopkins University website in a web browser.
KPOT – Used alongside the Coronavirus Ransomware at the moment, and potentially other ransomware to exfiltrate information from web browsers. It also works with instant messengers, VPN, RDP, FTP, gaming software, cryptocurrency, and more. The Coronavirus Ransomware has been seen used as a cover KPOT to steal sensitive data in this time of crisis.
Emotet – An Emotet malware spam campaign has been reported targeting the people of Japan, focused on the Osaka, Gifu and Totori prefectures. The spam emails are disguised as official notifications about the coronavirus, allegedly coming from disability welfare service providers and public health centers. Each of the malspam emails contains a warning note attempting to push users to take action. This is done by downloading a malicious Word document attachment that contains the Emotet banking Trojan.
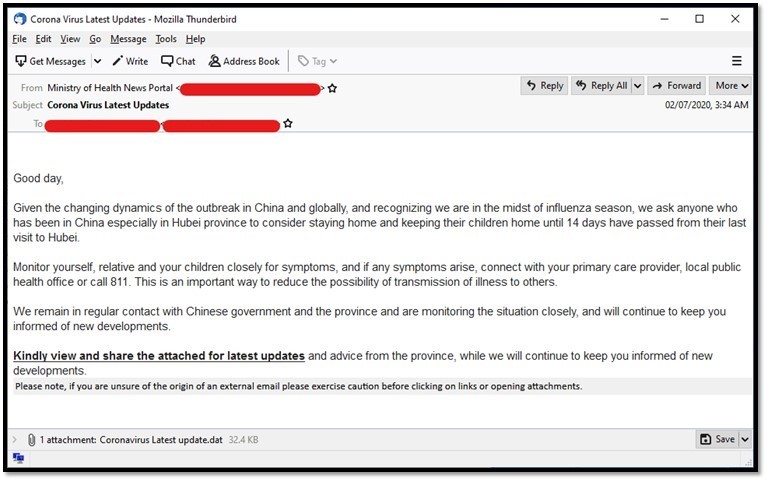
COVID--19 email spam masquerading as an official Ministry of Health email.
CovidLock – A mobile ransomware coming from a malicious Android app, allegedly offering to track cases of COVID-19. The ransomware locks infected phones, giving them a deadline of 48 hours to pay a ransom of US$100 paid in Bitcoin. Threats made include the deletion of any data stored on the device, as well as leaking any social media account details online.
Agent Tesla – A remote access tool (RAT) focused on remote control of devices. This tool is available for purchase from an official website and developers present it as a legitimate program. In reality, Agent Tesla is an info stealer used to take control and exfiltrate data, employed by cyber criminals in their schemes and scams. The malware is purchasable and available to many, so threat actors have been spotted taking interest in it.
Subject: Coronavirus (2019 -nCov) Safety Measures
Dear Sir/Madam,Go through the attached document on safety measures regarding the spreading of corona virus.
This little measure can save you.
WHO is working closely with global experts, governments and partners to rapidly expand scientific knowledge on this new virus and to provide advice on measures to protect health and prevent the spread of this outbreak.
Symptoms to look out for; Common symptoms include fever, cough, shortness of breath, and breathing difficulties.
Regards
Dr Liang -
Intensive Care Physician
WHO Plague Prevention & Control
Coronavirus email virus files reside inside infected attachments to spam emails like this one.
LokiBot – A threat used to collect information from affected computers. LokiBot has a keylogger used to collect the passwords and login data, sent off to an external server. The criminals may then access the victim's data and online accounts. The main way in which LokiBot is being distributed at this time is through a Coronavirus spam campaign, which may often use infected email attachments. Once LokiBot is installed, it is capable of collecting usernames, passwords, as well as cryptocurrency wallet information and more.
RemcosRAT – Remcos (Remote Control and Surveillance) is a Remote Access Trojan (RAT) that anyone can purchase and use for whatever purpose they wish. The tool itself is is presented as legitimate. The developers of Remcos forbid misuse, but that doesn't stop cyber criminals from using the tool to generate revenue. Remcos is now also used in Coronavirus spam campaigns.
Trojan.Trickbot – A trojan-type malware designed to steal users' private data and banking details. It often proliferates using spam emails, right now acting as a Coronavirus email virus. It might also spread using fake Adobe Flash Player updates. Trojan.Trickbot targets various financial institutions, banks, and credit card providers.
FormBook – A Coronavirus email virus, also used before the pandemic, designed to steal personal data. Also spread via spam emails that contain malicious attachments. The FormBook developers offer this threat for sale - cyber criminals may pay a subscription to gain access to the FormBook tool. FormBook infections have been detected in the US and South Korea.
Ave Maria – A trojan designed to steal information and to cspread more infections. It proliferates using spam email campaigns. Criminals send thousands of emails in a Coronavirus spam campaign that contain infectious attachments. Most of those are Microsoft Office files. Emails contain messages pushing users to open the attached document, resulting in an Ave Maria infection.
Trojan.LimeRAT – An open source malicious tool that may operate as ransomware, a information stealer, cryptocurrency miner, keylogger or worm.
Crimson Rat – A remote access Trojan (RAT) developed using Java. Much like other threats of this kind of a similar nature, it is used to take control of infected devices and to steal information. Crimson Rat may also delete files from infected machines. Criminals spread Crimson Rat using Coronavirus spam campaigns that contain malicious Microsoft Office document attachments.
Remote Work Vulnerabilities – With the increase in remote work that companies are turning to in lieu of the coronavirus pandemic, new risks to organizations are made more obvious. The major problem in this case is communication happening entirely online, which opens the way to threat actors and their deceptive practices. Social engineering scams and hacks are on the rise, ones that rely more on old-fashioned con-artistry than brute forcing of corporate and government networks. These vulnerabilities may be exploited to not only steal information, but to disseminate false data inside affected networks and organizations.
Business Email Compromise Scams (BEC)
A BEC attack was reported by Agari Cyber Intelligence Division (ACID), a continuation of an earlier campaign done by the cybercrime group Ancient Tortoise. The threat actors target accounts receivables into forwarding aging reports. The next step is posing as legitimate companies to use the customer information from these reports to send emails informing customers of changes in back and payment methods due to the COVID-19 pandemic. This type of scam is aimed at companies conducting wire transfers with suppliers abroad. Email accounts of corporate executives or high-level employees are spoofed or compromised via phishing or keyloggers. These accounts are then used to perform fraudulent transfers. In 2016 alone BEC attacks resulted in US$140,000 worth of losses for companies globally.
How to Avoid Malware Infections During the Pandemic?
- Don't click on unfamiliar links from unknown people.
- Only download/install software from legitimate, trusted sources.
- Make sure you verify the URL of websites asking for a password, since hackers may setup a fake URL to collect login data.
Coronavirus-themed phishing emails may take different forms:
Fake CDC and health authority alerts – Cybercriminals have been using phishing emails that look like they come from legitimate sources, such as the US Centers for Disease Control (CDC). The email might claim to contain a link to an alleged list of coronavirus cases in your area. The phishing text may insist you need to click on the link immediately to find out more information or for your safety.
Health advice emails – Phishing attempts using emails that claim to have legitimate medical advice to help protect against the virus. Emails may pretend to be from medical experts in China or your country. They will ask to download a file or click on a link to find out more.
Workplace policy emails – Cybercriminals may have work on targeting workplace email accounts used by employees. As one phishing email shows, they are using safety precautions as bait, claiming a company is instituting a new policy regarding the disease. If that fake company policy is clicked on, a malicious download begins.
What can we do to avoid scammers?
Don't fall prey to requests for personal information – The fake ads and scams are focused on creating fear and claiming to offer treatment and prevention for the coronavirus. They use words such as "Buy now, limited supply" etc. Clicking on these links and downloading anything might lead to installing malware on your device, or you might be scammed out of your money. Do not share personal information, such as credit card numbers, names, and addresses. Legitimate government agencies will never ask for information. Never respond to emails with any personal data.
Check incoming email addresses and links – Hovering your mouse over a URL may show where it leads, and in such cases, it may indicate the address isn't legitimate. Keep in mind phishing attempts may create links that look very close to the real addresses. Delete such emails and don't open them under any circumstances.
Watch for grammar and spelling mistakes – If your allegedly official email has punctuation, spelling, and grammar errors, it may be a sign of a phishing email. Make sure you get rid of it without opening or downloading anything.
Watch out for generic greetings – Phishing emails are often very unlikely to use your name, as they are blanket solutions for scammers. Emails starting with a generic 'Dear Sir or Madam" may be a sign it was criminals who sent the email.
Avoid emails pressing you to take urgent action – Phishing emails are often made with the idea of urgency or demanding immediate attention. The goal is to push you to click on links due to fear and to get your device infected. Avoid those and delete the messages.
File names and SHA256 hashes:
| File Name | SHA256 |
| CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm | ab533d6ca0c2be8860a0f7fbfc7820ffd 595edc63e540ff4c5991808da6a257d |
| CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm | 17161e0ab3907f637c2202a384de67fca 49171c79b1b24db7c78a4680637e3d5 |
| CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm | 315e297ac510f3f2a60176f9c12fcf9 2681bbad758135767ba805cdea830b9ee |
| CoronaVirusSafetyMeasures_pdf.exe | c9c0180eba2a712f1aba1303b90cbf12c11 17451ce13b68715931abc437b10cd |
| CoronaVirusSafetyMeasures_xls.exe | 29367502e16bf1e2b788705014d0142 d8bcb7fcc6a47d56fb82d7e333454e923 |
| LIST OF CORONA VIRUS VICTIM.exe | 3f40d4a0d0fe1eea58fa1c71308431b5c2c e6e381cacc7291e501f4eed57bfd2 |
| POEA HEALTH ADVISORY re-2020 Novel Corona Virus.pdf.exe | 3e6166a6961bc7c23d316ea9bca87d82 87a4044865c3e73064054e805ef5ca1a |
| POEA Advisories re-2020 Novel Corona Virus.2.pdf.exe | b78a3d21325d3db7470fbf1a6d254e23d34 9531fca4d7f458b33ca93c91e61cd |
Identified domains:
- acccorona[.]com
- alphacoronavirusvaccine[.]com
- anticoronaproducts[.]com
- beatingcorona[.]com
- beatingcoronavirus[.]com
- bestcorona[.]com
- betacoronavirusvaccine[.]com
- buycoronavirusfacemasks[.]com
- byebyecoronavirus[.]com
- cdc-coronavirus[.]com
- combatcorona[.]com
- contra-coronavirus[.]com
- corona-armored[.]com
- corona-crisis[.]com
- corona-emergency[.]com
- corona-explained[.]com
- corona-iran[.]com
- corona-ratgeber[.]com
- coronadatabase[.]com
- coronadeathpool[.]com
- coronadetect[.]com
- coronadetection[.]com
Created files:
| Corona-virus-Map.com.exe | C:\Users\%username%\AppData\Local\Temp\aut9BDA.tmp |
| Corona-virus-Map.com.exe | C:\Users\%username%\AppData\Roaming\Z11062600\Corona[.]exe |
| Corona-virus-Map.com.exe | C:\Users\%username%\AppData\Local\Temp\aut9DFE.tmp |
| Corona-virus-Map.com.exe | C:\Users\%username%\AppData\Roaming\Z11062600\ Corona-virus-Map.com[.]exe |
| Corona.exe | C:\Users\%username%\AppData\Local\Temp\RarSFX0\Corona[.]bat |
| Corona.exe | C:\Users\%username%\AppData\Local\Temp\RarSFX0\Corona.sfx[.]exe |
| Corona.exe | C:\Users\%username%\AppData\Local\Temp\autA83E.tmp |
| Corona.exe | C:\Users\%username%\AppData\Roaming\Z58538177\bin[.]exe |
| Corona.exe | C:\Users\%username%\AppData\Local\Temp\autAAB0.tmp |
| Corona.exe | C:\Users\%username%\AppData\Roaming\Z58538177\Build[.]exe |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-console-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-datetime-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-debug-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-errorhandling-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-file-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-file-l1-2-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-file-l2-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-handle-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-heap-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-interlocked-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-libraryloader-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-localization-l1-2-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-memory-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-namedpipe-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-processenvironment-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-processthreads-l1-1-0.dl |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-processthreads-l1-1-1.dl |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-profile-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-rtlsupport-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-string-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-console-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-synch-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-synch-l1-2-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-sysinfo-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-timezone-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-util-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-conio-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-convert-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-environment-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-filesystem-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-heap-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-locale-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-math-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-multibyte-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-private-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-process-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-runtime-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-stdio-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-string-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-time-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-c |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-synch-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-synch-l1-2-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-sysinfo-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-timezone-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-util-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-conio-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-convert-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-environment-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-filesystem-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-heap-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-locale-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-math-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-multibyte-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-synch-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-synch-l1-2-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-sysinfo-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-timezone-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-core-util-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-conio-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-convert-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-environment-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-filesystem-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-heap-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-locale-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-math-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda \api-ms-win-crt-multibyte-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-private-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-process-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-runtime-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-stdio-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-string-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-time-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ api-ms-win-crt-utility-l1-1-0.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\freebl3.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\mozglue.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\msvcp140.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\nss3.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\nssdbm3.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\softokn3.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ucrtbase.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\vcruntime140.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\nss3.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\nss3.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\mozglue.dll |
| Bin.exe | C:\Users\%username%\AppData\Local\Temp\2fda\ vcruntime140.dll |
| Build.exe | C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ ENU_64B5614D0F4B35423983 |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\LocalLow\Microsoft\ CryptnetUrlCache\MetaData\ EB2C4AB8B68FFA4B7733A9139239A396_ D76DB901EE986B889F30D8CC06229E2D |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\Local\Temp\autB628.tmp |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ Windows.Globalization.Fontgroups.sqlite3.module.dll.2 |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ Windows.Globalization.Fontgroups.sqlite3.module.dll |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\LocalLow\Microsoft\ CryptnetUrlCache\MetaData\ 223DE96EE265046957A660ED7C9DD9E7_ EFF9B9BA98DEAA773F261FA85A0B1771 |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\Local\Microsoft\Windows \INetCache\IE\2KY2PE8H\getMe[1].json |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\LocalLow\Microsoft\ CryptnetUrlCache\MetaData\ 6BADA8974A10C4BD62CC921D13E43B18_ 74167E25E5476CCA2A5946AAA61BF9E1 |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\Local\Microsoft\Windows \INetCache\IE\1OZ94YX5\json[1].json |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\Roaming\amd64_netfx4-system.runti..dowsruntime.ui.xaml\1\Information.txt |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\Local\Temp\autCC51.tmp |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ Windows.Globalization.Fontgroups.module.exe.2 |
| Windows.Globalization. Fontgroups.exe |
C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ Windows.Globalization.Fontgroups.module.exe |
| Windows.Globalization. Fontgroups.module.exe |
C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ ENU_64B5614D0F4B35423983.7z |
| Windows.Globalization. Fontgroups.module.exe |
C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ ENU_64B5614D0F4B35423983.7z |
| Windows.Globalization. Fontgroups.module.exe |
C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ ENU_64B5614D0F4B35423983.7z |
| Windows.Globalization. Fontgroups.module.exe |
C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ ENU_64B5614D0F4B35423983.7z |
| Windows.Globalization. Fontgroups.module.exe |
C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ ENU_64B5614D0F4B35423983.7z |
| Windows.Globalization. Fontgroups.module.exe |
C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ ENU_64B5614D0F4B35423983.7z |
| Windows.Globalization. Fontgroups.module.exe |
C:\Users\%username%\AppData\Roaming\ amd64_netfx4-system.runti..dowsruntime.ui.xaml\ ENU_64B5614D0F4B35423983.7z |
Modified registers:
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntrane
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Notifications\Data\418A073AA3BC3475
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content\CachePrefix
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies\CachePrefix
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History\CachePrefix
HKLM\System\CurrentControlSet\Services\bam\State\UserSettings\S-1-5-21-3887374624-1885671809-3229943349-1001\\Device\HarddiskVoume4\Windows\SysWOW64\cmd.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Notifications\Data\418A073AA3BC3475
HKCU\Software\Classes\Local Settings\MuiCache\56\52C64B7E\LanguageList
HKCU\Software\Classes\Local Settings\MuiCache\56\52C64B7E\LanguageList
HKCU\Software\Classes\Local Settings\MuiCache\56\52C64B7E\LanguageList
HKCU\Software\Classes\Local Settings\MuiCache\56\52C64B7E\LanguageList
Mutexes Created:
\Sessions\1\BaseNamedObjects\A4B6CE24-E72D679B-BE9A182F-D7CE305A-FB62BB342
\Sessions\1\BaseNamedObjects\IESQMMUTEX_0_208
\Sessions\1\BaseNamedObjects\417087542ENU_FE97A6DDE921C7562535
\Sessions\1\BaseNamedObjects\MSIMGSIZECacheMutex
\Sessions\1\BaseNamedObjects\GdiplusFontCacheFileV1
\Sessions\1\BaseNamedObjects\Global\CPFATE_2304_v4.0.30319
\Sessions\1\BaseNamedObjects\Local\c:!users!user!appdata!roaming!microsoft!windows!ietldcache!
\Sessions\1\BaseNamedObjects\Local\_!MSFTHISTORY!_LOW!_
\Sessions\1\BaseNamedObjects\Local\c:!users!user!appdata!local!microsoft!windows!temporary internet files!low!content.ie5!
\Sessions\1\BaseNamedObjects\Local\c:!users!user!appdata!roaming!microsoft!windows!cookies!low!
\Sessions\1\BaseNamedObjects\Local\c:!users!user!appdata!local!microsoft!windows!history!low!history.ie5!
\Sessions\1\BaseNamedObjects\A4B6CE24-E72D679B-BE9A182F-DACC8B0F-7324685F3
\Sessions\1\BaseNamedObjects\417087542ENU_687FE9797AC054582535
\Sessions\1\BaseNamedObjects\Global\CPFATE_1308_v4.0.30319
Network Communication:
| Process | Ip Address | Url |
| Bin.exe | 104.24.103.192:80 | Coronavirusstatus[.]space/index.php |
| Windows.Globalization. Fontgroups.exe |
149.154.167.220:443 | api.telegram.org |
| Windows.Globalization. Fontgroups.exe |
104.26.9.44:443 | ipapi.co/json |
| Windows.Globalization. Fontgroups.exe |
93.184.220.29:80 | ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCG gUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU 5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5 hY5qj0aEmX0H4s05bY%3D |
| Corona-virus-Map.com.exe | 18.205.183.153:443 | gisanddata.maps.arcgis[.]com |
| Corona-virus-Map.com.exe | 54.192.87.49:443 | https://js.arcgis.com/3.31/dijit/form/_ListBase[.]js |
| Corona-virus-Map.com.exe | 54.192.87.49:443 | https://js.arcgis.com/3.31/dijit/form/MappedTextBox[.]js |