CoronaVirus Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
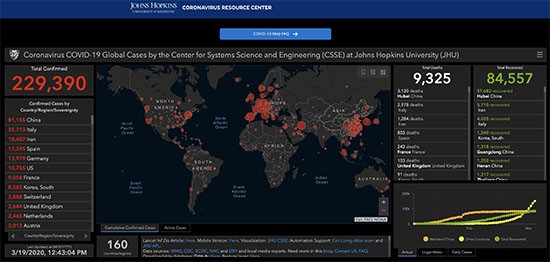
| Threat Level: | 100 % (High) |
| Infected Computers: | 11 |
| First Seen: | January 19, 2011 |
| Last Seen: | March 27, 2020 |
| OS(es) Affected: | Windows |
CoronaVirus Ransomware Image
The CoronaVirus Ransomware (also called CoronaVi2022 Ransomware) is a file-locker, which was released in the wild recently, and it seems that its author has opted to use the name of the Coronavirus (also known as COVID-19), which is a disease that is threatening users worldwide. Just like the disease it is named after, the CoronaVirus Ransomware also threatens users worldwide, but in a different way – it will try to encrypt their files, and also overwrite the contents of their drive's Master Boot Record (MBR). The latter operation may cause a lot of trouble, since the victims' computers will not load their operating system and, instead, they will display a copy of the CoronaVirus Ransomware's ransom message.
The authors of the CoronaVirus Ransomware are likely to employ more than one strategy when it comes to distributing their threat. Some popular malware propagation techniques involve fake downloads, corrupted advertisements, phishing emails and pirated software or media. We advise you to avoid interacting with unknown online content, as well as to invest in a reliable anti-malware software suite. In the case of the CoronaVirus Ransomware, the attackers have opted to set up a fake website that mimics the name of a legitimate Windows PC optimization utility – WiseCleaner. The bogus domain hosts a modified copy of the WiseCleaner that is meant to install the CoronaVirus Ransomware and KPOT, an info-collector Trojan.
Table of Contents
Can You Take Coronavirus Ransomware Preventative Measures?
If preventive measures are not taken, the CoronaVirus Ransomware may be able to inflict a lot of damage to your files. On top of overwriting the MBR, the CoronaVirus Ransomware also will encrypt spreadsheets, documents, presentations, text files, archives, databases, pictures and others. Usually, file-lockers mark the names of the files they lock, but the CoronaVirus Ransomware operates in a different way – it uses the suffix 'coronaVi2022@protonmail.ch___' to mark locked files. For example, if you had the file 'image.png' on your computer, it would go by the name 'coronaVi2022@protonmail.ch___image.png' after the attack.
Another change that the CoronaVirus Ransomware brings is to create the ransom message 'CoronaVirus.txt.' It has similar contents to the text found in the overwritten MBR. According to the message, victims will not be able to rely on free decryption utilities, and their only option is to purchase a decryption service from the attackers. The price of this service has been set to 0.08 Bitcoin ($460 as of 03.13.20) – we assure you that paying the ransom fee is a terrible idea, since you may not get anything in return.
Unfortunately, there is not much to do when it comes to the recovery of your files. If you have an up-to-date backup copy of your data, then you should be able to recover from the attack with ease. However, if you do not possess a backup to work with, then we suggest experimenting with alternative data recovery software. Last but not least, you should ensure the full removal of the CoronaVirus Ransomware with the use of an up-to-date anti-malware application.
CoronaVirus Ransomware and KPOT Malware Threats Further COVID-19 Pandemic in the Digital World Through Theft of Personal Data
They say nothing brings people together like a crisis. Unfortunately, it can also bring out the worst in people; like the people who are using the very real threat of the coronavirus (COVID—19) to spread malware. In particular, the CoronaVirus ransomware together with the KPOT trojan horse, are looking to pilfer data from infected computers and at the same time leverage the hysteria surrounding the COVID-19 Coronavirus pandemic.
This Week in Malware Video: A CoronaVirus Malware Alert discussing how hackers are continually leveraging the COVID-19 epidemic to spread malware, phishing emails, fake apps, fake websites, and malware-laced advertisements.
There have been several examples of malware related to coronavirus. The newest threat, simply called CoronaVirus ransomware, is being spread through a fake website set up to appear like the website of the legitimate system optimizing software WiseCleaner.
What makes this attack so dangerous is that aside from infecting computers with ransomware, it also comes with the information-stealing Trojan called KPOT.
The Fake Website WiseCleaner Spreads Coronavirus Ransomware
The ransomware is being spread through the use of a website designed to look just like WiseCleaner.com; a website that offers system utility tools for Windows computers.

WiseCleaner.com fake website
The website – discovered by the MalwareHunterTeam – contains a download file called WSHSetup.exe. This .exe file contains the CoronaVirus ransomware as well as the KPOT trojan, which is known to steal passwords and other information from infected computers.
When someone runs the program, it downloads several files from another website. The key downloads are "file1.exe" and "file2.exe", but accessing the website will show there are seven downloads in all.
The KPOT trojan hides inside the "file1.exe" executable file. The trojan steals cookies and login information from web browsers, email accounts, gaming accounts, VPNs, and FTP servers. The ransomware also grabs a screenshot of the active desktop and scans for bitcoin wallets to steal from.
All of the information gathered by the trojan is sent to another website where it is collected by attackers. Most of the time these attackers will sell the information instead of using it themselves.
The actual CoronaVirus ransomware is hidden in the "file2.exe" file. When this file is downloaded and run, it attempts to encrypt all of the files on the computer that have the following file extensions:
.bak, .bat, .doc, .jpg, .jpe, .txt, .tex, .dbf, .xls, .cry, .xml, .vsd, .pdf, .csv, .bmp, .tif, .tax, .gif, .gbr, .png, .mdb, .mdf, .sdf, .dwg, .dxf, .dgn, .stl, .gho, .ppt, .acc, .vpd, .odt, .ods, .rar, .zip, .cpp, .pas, .asm, .rtf, .lic, .avi, .mov, .vbs, .erf, .epf, .mxl, .cfu, .mht, .bak, .old
The encrypted files are renamed to the email address of the attacker. It will still retain the same extension though. It’s just that almost every file on the computer will be renamed to some variation of 'coronaVi2022@protonmail.ch'.
A ransom note is placed in every encrypted folder on the computer. A copy of the ransom note is also placed on the desktop. The ransom demands that victims pay 0.008 bitcoin (around $50) to a static bitcoin address.
CoronaVirus ransomware ransom note
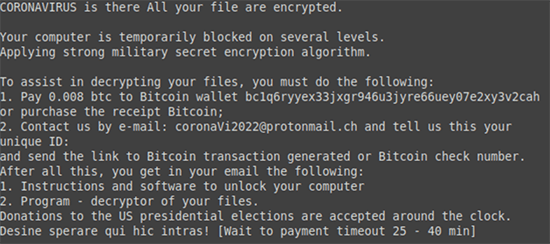
CoronaVirus ransomware ransom note
The CoronaVirus ransom note reads:
CORONAVIRUS is there All your file are encrypted.
Your computer is temporarily blocked on several levels.
Applying strong military secret encryption algorithm.To assist in decrypting your files, you must do the following:
1. Pay 0.008 btc to Bitcoin wallet bc1q6ryyex33jxgr946u3jyre66uey07e2xy3v2cah or purchase the receipt Bitcoin;
2. Contact us by e-mail: coronaVi2022@protonmail.ch and tell us this your
unique ID:
and send the link to Bitcoin transaction generated or Bitcoin check number.
After all this, you get in your email the following:
1. Instructions and software to unlock your computer
2. Program - decryptor of your files.
Donations to the US presidential elections are accepted around the clock.
Desine sperare qui hic intras! [Wait to payment timeout 25 - 40 min]
Last but not least, the ransomware renames the C: drive of the computer to "CoronaVirus", which seems to be nothing more than a bit of a "joke" on the attacker’s part.
CoronaVirus Ransomware Adds Additional Lock Screen at Boot
CoronaVirus also changes the Windows registry settings on the computer to display a lock screen when the computer is rebooted. The lock screen shows the same message as the ransom note before finally loading the actual operating system.
The lock screen changes after 45 minutes, but still doesn’t allow access to the computer. It will eventually boot into Windows after a further 15 minutes, where users are presented with the ransom note again after logging in.
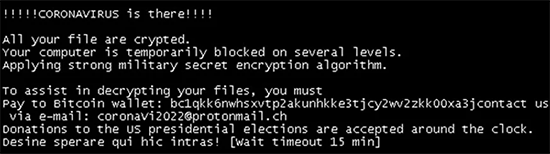
Coronavirus ransomware alternate lock screen
Coronavirus ransomware alternate lock screen message reads:
!!!!!CORONAVIRUS is there!!!!
Applying strong military secret encryption algorithm.
your file are encrypted.To assist in decrypting your files, you must Pay to Bitcoin wallet: bdgkk6nwhsxvtpzakunhkke3tjcyzww2zkk00xa3jcontact us via e-mail: coronavi2022@protonma11.ch
Donations to the US presidential elections are accepted around the clock.
Desine sperare qui hic intras! (wait timeout 15 min
Is the endgame the ransom or your data?
Given that the ransomware has a relatively low ransom demand, a static address, and a political message, it’s likely that it’s nothing more than a diversion. The real threat in the package is the KPOT trojan. Actually, at the time of writing, the bitcoin address has yet to receive any payments, which only adds credence to this theory.
By making users worried about the ransomware it distracts away from KPOT, which steals passwords, cookies, cryptocurrency, and plenty of other information worth more than $50 and sends the collected information to an attacker. The most important thing anyone who gets hit with the CoronaVirus ransomware should do is to change their online passwords before they can be used and abused.