Vicious Panda
There have been several stories in recent months of cyber criminals using the very real threat of Coronavirus to spread malware and ransomware. These threats have been propagated all across the world, but there have been a number coming out of China in particular. To the point that state-sponsored Chinese hacking group Vicious Panda has started to spread their own malware through coronavirus.
The information about the attack comes from Check Point, who published research showing that a Chinese APT has "weaponized" legitimate information about coronavirus to spread their malicious malware to the masses.
Table of Contents
The Second Attack
The Vicious Panda attack is actually the second major Coronavirus (COVID-19) related malware campaign to come out of China in the past few weeks. The first happened at the start of March when the Vietnamese cyber-security group VinCSS noticed an attack by Mustang Panda. Mustang Panda is another Chinese state-sponsored hacking group.
Their attack was known for distributing emails with an attached RAR file that claimed to contain a message from the Vietnamese Prime Minister about the coronavirus. Rather than containing any kind of important message, the RAR file contained a backdoor trojan that installed itself on victim’s computers and opened them up to the hacking group.
Vicious Panda Attacks Mongolian Government
The Vicious Panda attack was spotted by Check Point, who said they were keeping tabs on the group as they were targeted Mongolian government organizations. Like the first attack, the group claimed to have vital information about coronavirus that users should download to access.
Check Point was able to intercept a cyber attack from a "Chinese APT group on a public sector entity of Mongolia." The attack leveraged the fears of coronavirus during the social engineering phase. It contained two documents. One of the documents was related to COVID-19 and both of them claimed to be from the Mongolian Ministry of Foreign Affairs. The documents came packaged with a unique malware threat that allowed for remote access of victim’s computers.

Email attachment - Source: research.checkpoint.com
The Tip of the Iceberg
Unfortunately, this latest attack is nothing new and merely represents the tip of the proverbial iceberg. Hackers have always used these kinds of crises to their advantage so there was no way they would be able to resist taking advantage of COVID-19.
The latest Chinese APT document was, according to Check Point, titled ‘About the Spread of New Coronavirus Infections’. It cites the National Health Committee of China in order to appear more authentic and be more effective. While there have been a number of cyber threats related to COVID-19, this appears to be the first one conducted by a state-sponsored hacking group against a foreign government.
As well as being the latest in a series of coronavirus-related hacking attacks, Check Point says that the attack is just the latest in an ongoing campaign by Chinese hackers against other governments and organizations. The difference is that this one leveraged coronavirus as part of the deployment method.
The attack was described as "exploiting public interest in coronavirus for [China’s] own agenda through a novel cyber infection chain." They say that Vicious Panda are targeting countries across the world – not just Mongolia. They urge every public sector entity and telco to be on alert over potential cyber threats, particularly anything that claims to be about coronavirus.
The email and documents claim to come from within Mongolia’s own government. At least one of them claimed to come from the Minister of Foreign Affairs. The campaign targeted other parts of the Mongolian public sector. The aim of the campaign appeared to be grabbing information and screenshots from government computers, editing and deleting files, and taking remote control of those computers.
How Does the Vicious Panda Ransomware Work?
The malicious attachment contains a remote access trojan (RAT) that can take control of computers. The trojan is programmed to have limited connections to the command and control server, which can make it more difficult to detect. The structure of the payload suggests that it could include other modules that are scheduled for installation later on as part of a larger campaign. From what Check Point can tell, the malware used in the attack is a completely unique and custom-designed strain, but exactly how it works – and what it does – are fairly common.
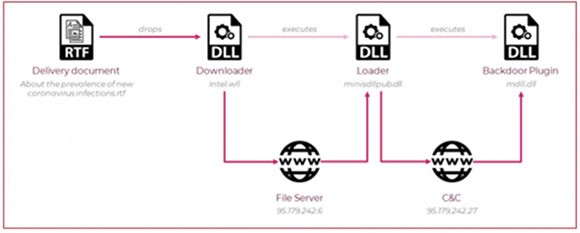
Vicious Panda Infection Chains - Source: research.checkpoint.com
Check Point broke down other parts of the campaign, such as where the command and control center was hosted. At the end of the day though, this malware is nothing short of a state-sponsored campaign. It uses social engineering to encourage users to download and open an attachment. The attachment loads another file and installs a backdoor to the computer. China can then exploit that backdoor to spy on government targets.
Cybercrooks Will Continue to Leverage China and the Coronavirus
While the top-level signposts don’t offer enough information to pinpoint exactly who is behind the attack, Check Point dug into the malware code and found that it was similar to code used in other malware related to China. Those campaigns were also aimed at China’s enemies.
China – the epicenter of coronavirus – is using the virus to its own advantage in many deceptive methods.. It’s not surprising that they would use the coronavirus though, as it is currently the best social engineering tool available to threat actors. Even regular cybercriminals are leveraging it in their own campaigns.

