CovidLock Ransomware
CovidLock Ransomware Image
It would appear that cybercriminals like to follow the ‘Never let a serious crisis go to waste’ motto as many of them are attempting to cash in on the Coronavirus outbreak that is plaguing every continent in the world. One of the newest threats affiliated with the Coronavirus, also known as COVID-19, is called the CovidLock Ransomware. This file-locking Trojan is specifically designed to target Android devices.
They say the Chinese use the same word flor "crisis" as they do "opportunity". It seems that hackers are taking the crisis of the coronavirus epidemic and using it as an opportunity to exploit fears to make some money for themselves. They have taken to using websites and applications that claim to provide information about coronavirus to trick their targets.
The cybersecurity threat researchers with DomainTools have discovered one such new ransomware, which goes by the name CovidLock. CovidLock was found on the website coronavirusapp.site, which is one more to add to list of "sites to not visit or trust".
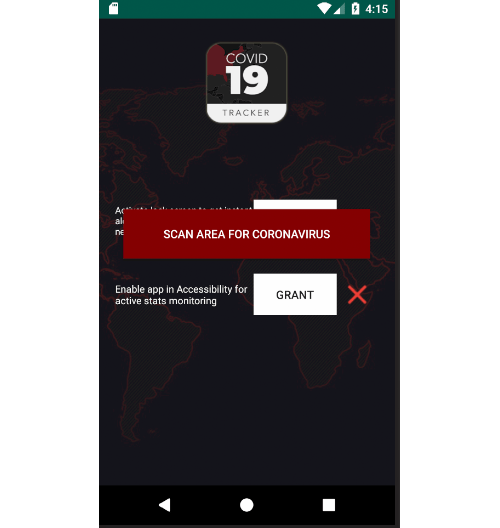
The website recommends users download and install an app that they claim offers regular updates about coronavirus, including notifying users when the virus reaches where they live. It also claims to offer heatmap visuals that show the spread of infection across an area.
Table of Contents
CovidLock Locks Users Out of Computers
While the website appears to display information straight from the World Health Organization and the Centers for Disease Control and Prevention, it actually serves as a host for the "CovidLock" ransomware. The ransomware, as expected, locks users out of their devices and demands a ransom payment.
The ransomware works by changing the lock screen on the infected device, demanding a ransom of $100 in bitcoin. Victims are told if they pay the ransom they will receive a decryption key to unlock their screen and get back control over their device.
CovidLock threatens that all information on the device will be erased if payment isn’t received within 48 hours. All of the information on the phone, including photos, videos, messages, and contacts, will all be deleted.
The ransom note is written in a way to scare victims into complying with the hackers demands. The message reads:
"YOUR GPS IS WATCHED AND YOUR LOCATION IS KNOWN. IF YOU TRY ANYTHING STUPID YOUR PHONE WILL BE AUTOMATICALLY ERASED."
The good news is that DomainTools claims they have reverse engineered the decryption key for the CovidLock ransomware. They say that they will post the decryption key publicly for anyone affected by it.
Propagation
The CovidLock Ransomware is hosted on a shady website called ‘coronavirusapp.site.’ It would appear that visitors of the site were urged to download and install an application that will provide them with information regarding the number of COVID-19 infections in their area via a heatmap interface. To make this application appear legitimate, its creators claim that this utility has been licensed by the CDC (Center for Disease and Prevention) and WHO (World Health Organization). Rest assured that these are fake licenses, and neither the CDC nor WHO have anything to do with this fake website. Since many people are worried about the number of infections in their area and would like to keep track of this crucial data, they may be misled into installing the application promoted by the dodgy site. However, installing the application hosted on the ‘coronavirusapp.site’ page will not provide you with a useful tool. Instead, the CovidLock Ransomware will compromise your device and lock your screen.
Demands
Once your screen has been locked by the CovidLock Ransomware, you will be asked to pay $100 in the shape of Bitcoin. The majority of cyber crooks prefer cryptocurrencies as a payment method, as it barely leaves any traces, which helps the conmen evade the authorities. The authors of the CovidLock Ransomware give victims a deadline – unless the ransom fee is paid within 48 hours, all the data present on the infected device will be wiped out. Furthermore, the CovidLock Ransomware claims to be able to access the user’s GPS location and issues a warning – ‘YOUR GPS IS WATCHED AND YOUR LOCATION IS KNOWN. IF YOU TRY ANYTHING STUPID YOUR PHONE WILL BE AUTOMATICALLY ERASED.’
The good news is that malware researchers are working on releasing a free decryption tool publicly in the near future. This means that the victims of the CovidLock Ransomware should keep an eye on the latest news regarding the threat online. Avoid downloading applications from third-party websites or application stores – they are far more likely to host compromised applications. Choose to download applications from the Google Play Store only, and even then be very careful what applications you trust. Make sure your Android device is protected by a genuine anti-virus utility.

