AZORult
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 4,445 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 228,774 |
| First Seen: | February 24, 2017 |
| Last Seen: | September 19, 2023 |
| OS(es) Affected: | Windows |
'AZORult' is an Infostealer Trojan that was added to AV databases in 2016 and received a major update in July 2018. The AZORult Infostealer Trojan includes downloader capabilities and may be used as first-stage and second-stage malware. The AZORult threat is introduced to computers via exploit kits primarily, but there are plenty of cases where AZORult was installed by users opening a corrupted Microsoft Word file received via spam emails. The AZORult dropper module was reported to be part of a campaign that delivered the Hermes Ransomware to users. The creators of AZORult have used forums on the Dark Web to promote their product and invite other threat actors to buy AZORult for their campaigns. The AZORult malware was promoted to include the following features:
- AZORult can copy browsing history from Internet clients based on Chromium and Mozilla Firefox.
- AZORult can hijack cryptocurrency wallets like Exodus, Jaxx, Mist, Ethereum, Electrum and Electrum-LTC.
- The new AZORult loader is said to be customizable and detect certain objects on the infected host, which can be uploaded to the 'Command and Control' server.
- AZORult can connect to the Internet through proxies installed on the infected host.
The AZORult Trojan can be used to collect information from users and drop more malware on compromised devices. The version 2 of AZORult make it one of the most versatile cyber threats of 2018. The AZORult Trojan is observed to encrypt the collected information using an XOR algorithm and a 3-byte key. AZORult can copy cookies from the browser and potentially allow cloned browser sessions.
This Week In Malware Ep 11: AZORult Trojan Using Fake ProtonVPN Installer to Trick Computer Users
The AZORult downloader module might enable threat actors to use a single PC and spread over a company network. The AZORult Trojan is deemed as an advanced threat that should be countered with multi-level defenses and reliable access policies. PC users that may be infected with AZORult may notice questionable process names in the task manager and unusual network communications. It is recommended to remove AZORult using a reputable anti-malware suite. Detection names associated with AZORult include:
BehavesLike.Win32.PWSZbot.dh
HW32.Packed.71D8
Heur.Win32.VBKrypt.3!O
Ransom.Win32.HERMS.SMTH
Spyware.Infostealer.Azorult
TROJ_GEN.R020H09GO18
Trojan ( 00538c421 )
Trojan-PSW.Win32.Coins.fjd
Trojan.PonyStealer.3
Trojan/Win32.Hermesran.R232399
Trojan:Win32/Skeeyah.A!rfn
Win32.Trojan-qqpass.Qqrob.Szvd
a variant of Win32/Injector.DZKP
Table of Contents
SpyHunter Detects & Remove AZORult
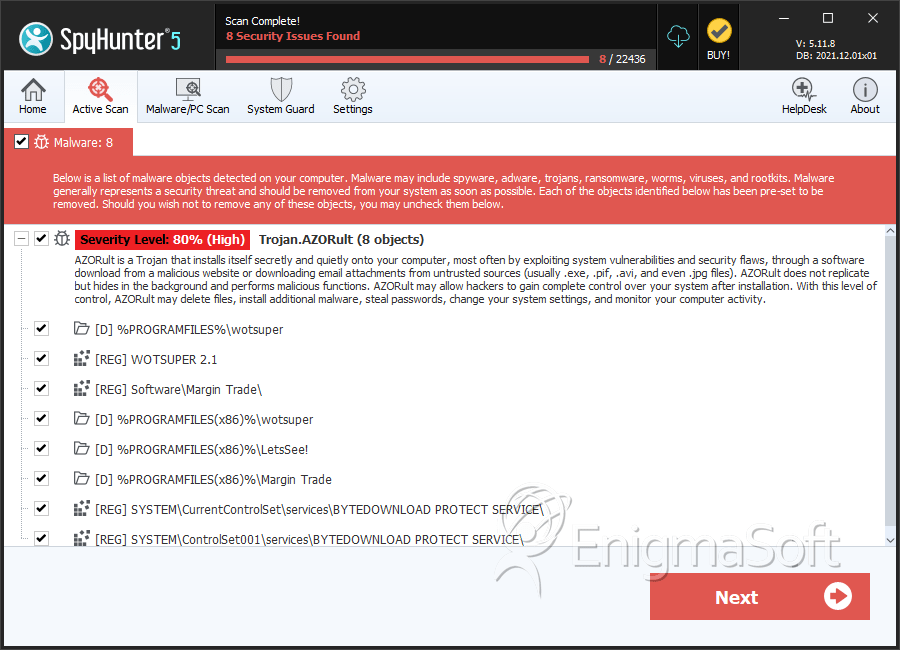
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | binances.exe | 6439131def75c6ef73cb43467c9444ff | 96 |
| 2. | 69ef96c982cd06ab342adbc051adb990 | 69ef96c982cd06ab342adbc051adb990 | 2 |
| 3. | file.exe | ab9330711166d04bd3814aa5a4873357 | 1 |
| 4. | 9994f688218d3c00c68937f2295fe6cd | 9994f688218d3c00c68937f2295fe6cd | 0 |
Registry Details
Directories
AZORult may create the following directory or directories:
| %APPDATA%\Margin Trade |
| %PROGRAMFILES%\Dada\softsinn |
| %PROGRAMFILES%\Issue\softsinn |
| %PROGRAMFILES%\LetsSee! |
| %PROGRAMFILES%\LetsSeeI |
| %PROGRAMFILES%\Margin Trade |
| %PROGRAMFILES%\karim\softsinn |
| %PROGRAMFILES%\rundll\softsinn |
| %PROGRAMFILES%\wotsuper |
| %PROGRAMFILES(x86)%\Dada\softsinn |
| %PROGRAMFILES(x86)%\Issue\softsinn |
| %PROGRAMFILES(x86)%\LetsSee! |
| %PROGRAMFILES(x86)%\LetsSeeI |
| %PROGRAMFILES(x86)%\Lov\softsinn |
| %PROGRAMFILES(x86)%\Margin Trade |
| %PROGRAMFILES(x86)%\karim\softsinn |
| %PROGRAMFILES(x86)%\rundll\softsinn |
| %PROGRAMFILES(x86)%\wotsuper |
| %WINDIR%\SysWOW64\softsinn |
| %WINDIR%\System32\softsinn |

