RemcosRAT
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 4,425 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 26,562 |
| First Seen: | October 16, 2016 |
| Last Seen: | August 5, 2024 |
| OS(es) Affected: | Windows |
Remcos RAT (Remote Access Trojan) is a sophisticated malware designed to infiltrate and control Windows operating systems. Developed and sold by a German company named Breaking Security as a legitimate remote control and surveillance tool, Remcos is frequently abused by cybercriminals for malicious purposes. This article delves into the characteristics, capabilities, impacts, and defenses related to Remcos RAT, as well as recent notable incidents involving its deployment.
Table of Contents
Deployment and Infection Methods
Phishing Attacks
Remcos is typically distributed through phishing attacks, wherein unsuspecting users are tricked into downloading and executing malicious files. These phishing emails often contain:
Malicious ZIP files disguised as PDFs, claiming to be invoices or orders.
Microsoft Office documents with embedded malicious macros designed to deploy the malware upon activation.
Evasion Techniques
To evade detection, Remcos employs advanced techniques such as:
- Process Injection or Process Hollowing: This method allows Remcos to execute within a legitimate process, thereby avoiding detection by antivirus software.
- Persistence Mechanisms: Once installed, Remcos ensures it remains active by employing mechanisms that allow it to run in the background, hidden from the user.
Command-and-Control (C2) Infrastructure
A core capability of Remcos is its Command-and-Control (C2) functionality. The malware encrypts its communication traffic en route to the C2 server, making it difficult for network security measures to intercept and analyze the data. Remcos uses Distributed DNS (DDNS) to create multiple domains for its C2 servers. This technique helps the malware evade security protections that rely on filtering traffic to known malicious domains, enhancing its resilience and persistence.
Capabilities of Remcos RAT
Remcos RAT is a powerful tool that offers numerous capabilities to attackers, enabling extensive control and exploitation of infected systems:
Privilege Elevation
Remcos can gain Administrator permissions on an infected system, allowing it to:
- Disable User Account Control (UAC).
- Execute various malicious functions with elevated privileges.
Defense Evasion
By using process injection, Remcos embeds itself within legitimate processes, making it challenging for antivirus software to detect. Additionally, its ability to run in the background further conceals its presence from users.
Data Collection
Remcos is adept at collecting a wide range of data from the infected system, including:
- Keystrokes
- Screenshots
- Audio recordings
- Clipboard contents
- Stored passwords
Impact of a Remcos RAT Infection
The consequences of a Remcos infection are significant and multifaceted, affecting both individual users and organizations:
- Account Takeover
By logging keystrokes and stealing passwords, Remcos enables attackers to take over online accounts and other systems, potentially leading to further data theft and unauthorized access within an organization's network. - Data Theft
Remcos is capable of exfiltrating sensitive data from the infected system. This can result in data breaches, either directly from the compromised computer or from other systems accessed using stolen credentials. - Follow-On Infections
An infection with Remcos can serve as a gateway for deploying additional malware variants. This increases the risk of subsequent attacks, such as ransomware infections, further exacerbating the damage.
Protection Against Remcos Malware
Organizations can adopt several strategies and best practices to protect against Remcos infections:
Email Scanning
Implementing email scanning solutions that identify and block suspicious emails can prevent the initial delivery of Remcos to users' inboxes.
Domain Analysis
Monitoring and analyzing domain records requested by endpoints can help identify and block young or suspicious domains that may be associated with Remcos.
Network Traffic Analysis
Remcos variants that encrypt their traffic using non-standard protocols can be detected through network traffic analysis, which can flag unusual traffic patterns for further investigation.
Endpoint Security
Deploying endpoint security solutions with the capability to detect and remediate Remcos infections is crucial. These solutions rely on established indicators of compromise to identify and neutralize the malware.
Exploitation of CrowdStrike Outage
In a recent incident, cybercriminals exploited a worldwide outage of the cybersecurity firm CrowdStrike to distribute Remcos RAT. The attackers targeted CrowdStrike customers in Latin America by distributing a ZIP archive file named 'crowdstrike-hotfix.zip.' This file contained a malware loader, Hijack Loader, which subsequently launched the Remcos RAT payload.
The ZIP archive included a text file ('instrucciones.txt') with Spanish-language instructions, urging targets to run an executable file ('setup.exe') to purportedly recover from the issue. The use of Spanish filenames and instructions indicates a targeted campaign aimed at Latin America-based CrowdStrike customers.
Conclusion
Remcos RAT is a potent and versatile malware that poses a significant threat to Windows systems. Its ability to evade detection, gain elevated privileges, and collect extensive data makes it a favored tool among cybercriminals. By understanding its deployment methods, capabilities, and impacts, organizations can better defend against this malicious software. Implementing robust security measures and staying vigilant against phishing attacks are crucial steps in mitigating the risk posed by Remcos RAT.
SpyHunter Detects & Remove RemcosRAT
RemcosRAT Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
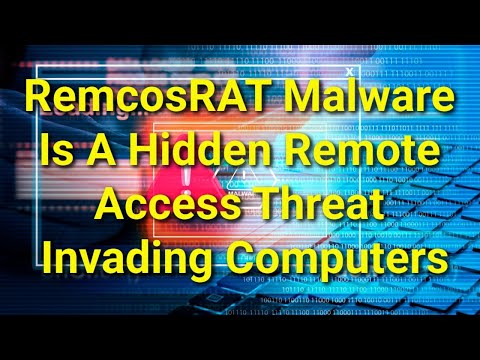
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 7g1cq51137eqs.exe | aeca465c269f3bd7b5f67bc9da8489cb | 83 |
| 2. | 321.exe | d435cebd8266fa44111ece457a1bfba1 | 45 |
| 3. | windslfj.exe | 968650761a5d13c26197dbf26c56552a | 5 |
| 4. | file.exe | 83dd9dacb72eaa793e982882809eb9d5 | 5 |
| 5. | Legit Program.exe | cd2c23deea7f1eb6b19a42fd3affb0ee | 3 |
| 6. | unseen.exe | d8cff8ec41992f25ef3127e32e379e3b | 2 |
| 7. | file.exe | 601ceb7114eefefd1579fae7b0236e66 | 1 |
| 8. | file.exe | c9923150d5c18e4932ed449c576f7942 | 1 |
| 9. | file.exe | 20dc88560b9e77f61c8a88f8bcf6571f | 1 |
| 10. | file.exe | c41f7add0295861e60501373d87d586d | 1 |
| 11. | file.exe | 8671446732d37b3ad4c120ca2b39cfca | 0 |
| 12. | File.exe | 35b954d9a5435f369c59cd9d2515c931 | 0 |
| 13. | file.exe | 3e25268ff17b48da993b74549de379f4 | 0 |
| 14. | file.exe | b79dcc45b3d160bce8a462abb44e9490 | 0 |
| 15. | file.exe | 390ebb54156149b66b77316a8462e57d | 0 |
| 16. | e12cd6fe497b42212fa8c9c19bf51088 | e12cd6fe497b42212fa8c9c19bf51088 | 0 |
| 17. | file.exe | 1d785c1c5d2a06d0e519d40db5b2390a | 0 |
| 18. | file.exe | f48496b58f99bb6ec9bc35e5e8dc63b8 | 0 |
| 19. | file.exe | 5f50bcd2cad547c4e766bdd7992bc12a | 0 |
| 20. | file.exe | 1645b2f23ece660689172547bd2fde53 | 0 |
| 21. | 50a62912a3a282b1b11f78f23d0e5906 | 50a62912a3a282b1b11f78f23d0e5906 | 0 |
Registry Details
Directories
RemcosRAT may create the following directory or directories:
| %ALLUSERSPROFILE%\task manager |
| %APPDATA%\Badlion |
| %APPDATA%\Extress |
| %APPDATA%\GoogleChrome |
| %APPDATA%\JagexLIVE |
| %APPDATA%\Remc |
| %APPDATA%\Shockwave |
| %APPDATA%\appdata |
| %APPDATA%\googlecrome |
| %APPDATA%\hyerr |
| %APPDATA%\loader |
| %APPDATA%\pdf |
| %APPDATA%\remcoco |
| %APPDATA%\ujmcos |
| %APPDATA%\verify |
| %APPDATA%\windir |
| %AppData%\remcos |
| %PROGRAMFILES(x86)%\Microsft Word |
| %TEMP%\commonafoldersz |
| %TEMP%\remcos |
| %Userprofile%\remcos |
| %WINDIR%\SysWOW64\Adobe Inc |
| %WINDIR%\SysWOW64\remcos |
| %WINDIR%\SysWOW64\skype |
| %WINDIR%\System32\rel |
| %WINDIR%\System32\remcos |
| %WINDIR%\notepad++ |
| %WINDIR%\remcos |
