Upatre
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 452 |
| First Seen: | June 22, 2015 |
| Last Seen: | May 22, 2023 |
| OS(es) Affected: | Windows |
Upatre is a Trojan downloader that is used to set up other threats on the victim's PC. Upatre has been used recently in several high profile Trojan attacks involving the Gameover Trojan. Trojan downloaders like Upatre are essential parts of threats distribution process. Trojans are characterized by the fact that they cannot distribute themselves or spread on their own. Unlike viruses, which corrupt executable files in order to ensure that they are multiplied on the victim's computer, or worms, which may use removable memory devices and other channels to spread from one computer to another, Trojans rely on the computer users themselves or on other threats to spread from one computer to another. In fact, the term 'Trojan' comes from the Trojan Horse, from the Iliad due to the fact that Trojans use similar tactics, entering a computer disguised as something beneficial and then releasing a payload or hidden harmful component. Trojan downloaders like Upatre are specific threats designed to deliver Trojan infections to the victim's computer, connecting to an outside server and downloading and setting up the threatening component on the victim's computer.
Table of Contents
Attacks Associated with this Trojan Downloader
Security analysts have monitored attacks involving a group of criminals that carry out their operations using a modified version of the infamous ZeuS Trojan. This Trojan, known as Gameover, incorporates many of the ZeuS Trojans' known spy and banking functions but also leverages the power of peer-to-peer (P2P) networks to carry its attacks, spread from one computer to another and prevents detection. Recent attacks involving the Gameover Trojan have incorporated the use of the Upatre Trojan downloader to deliver Gameover to the victim's computer.
Upatre itself is contained in a very small file, and Upatre carries its operation in a way that is simple, straightforward and hard to detect. Basically, Upatre connects to a specific URL that uses an encrypted SSL connection to download and install the Gameover Trojan. Once this is done, Upatre deletes itself to prevent PC security researchers from studying and preventing this infection. Upatre itself is distributed using unsafe email attachments specifically designed to trick inexperienced computer users into opening unreliable files that include Upatre's unsafe code. Typical examples of unsafe email attachments include fake invoices or receipts attached to bogus emails from known businesses or popular institutions.
SpyHunter Detects & Remove Upatre
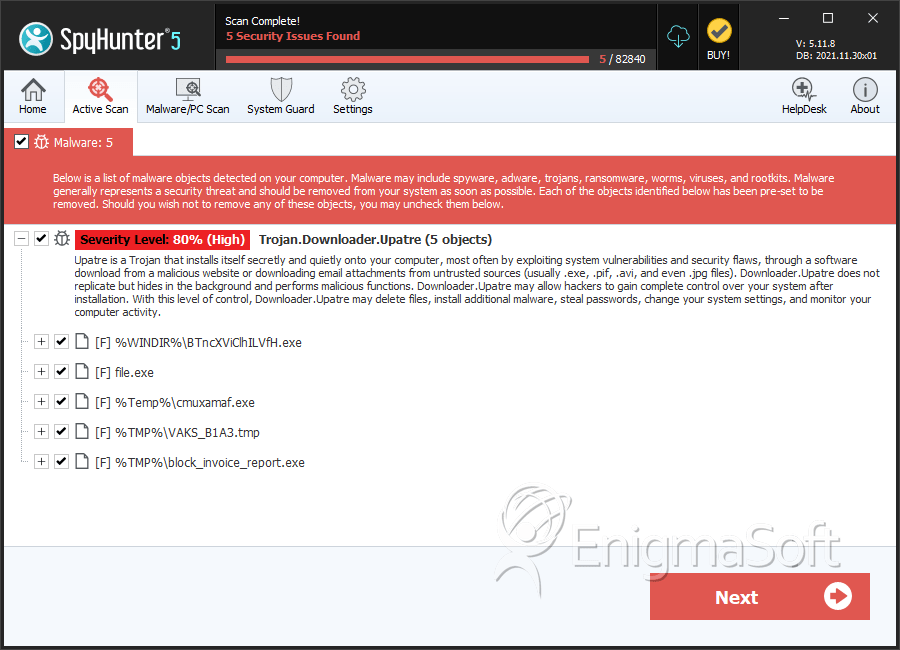
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | BTncXViClhILVfH.exe | fa1d581cd5997ee4854149c6ad5c044d | 1 |
| 2. | file.exe | 2833485ee2d5f6d43e44c2c223c00d25 | 0 |
| 3. | cmuxamaf.exe | dab3c55d2942d57d096efb18ab53b39c | 0 |
| 4. | VAKS_B1A3.tmp | 076464eafd55a39970cce66d5ca9d435 | 0 |
| 5. | block_invoice_report.exe | f3f26fc27d36c5cf3b3db901b591e0e7 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.