Mal/FakeAV-OY
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 70 % (High) |
| Infected Computers: | 39 |
| First Seen: | January 16, 2013 |
| Last Seen: | April 18, 2020 |
| OS(es) Affected: | Windows |
ESG security researchers have observed a wave of malware attacks involving fake email messages from ADP urging computer users to update their security settings. These kinds of tactics are actually quite common when it comes to malware. Many malware developers will convince their victims to download malicious files by disguising them as security patches or anti-virus programs updates. These kinds of attacks are especially effective today when, due to highly publicized zero-day vulnerabilities in Java 7 and Internet Explorer, most computer users are looking for ways to make their computer more secure. In this way, this kind of publicity actually has the unintended effect of providing criminals with social engineering scams that can be used to distribute malware. Mal/FakeAV-OY is one of the many malware infections being distributed in this way.
ADP is a payroll processing company. Mal/FakeAV-OY is distributed through a fake email message from ADP supposedly containing a security update. These email messages contain subjects claiming that the email contains an attached '2013 anti-fraud update'. However, downloading and opening the attached ZIP archive infects the victim's computer with Mal/FakeAV-OY. The email message containing the Mal/FakeAV-OY infection includes an introductory letter assuring the victim that the attachment is an update to protect their computer from fraud. Next, Mal/FakeAV-OY lists all the new 'features' in this supposed update. The wording and letterhead of this email message is designed to convince victims of its authenticity, despite the fact that it is a trap, which results in a severe malware infection on the victim's computer.
Table of Contents
How Mal/FakeAV-OY’s Payload Affects Your Computer
The Mal/FakeAV-OY malicious email message has been known to download and install rogue security software, also known as scareware or as fake anti-virus applications on the victim's computer. This is in line with the supposed security upgrade offered in Mal/FakeAV-OY's malicious email message. These kinds of fake security programs harass computer users, warning them of fake malware infections on their computer. This is done so that the victims will pay for a 'full version' of the rogue security program, usually handing over their credit card information in the process. It is necessary to be aware of computer security news and updates. However, it is important to be aware that many criminals disguise their malware as anti-virus software, meaning that not all anti-virus programs claims are what they seem.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| GData | Win32:LockScreen-SZ |
| AhnLab-V3 | Trojan/Win32.Foreign |
| AntiVir | TR/Urausy.EB.3 |
| Kaspersky | Trojan-Ransom.Win32.Foreign.aqok |
| Avast | Win32:LockScreen-SZ [Trj] |
| McAfee | RDN/Generic FakeAlert!bi |
| AVG | Generic32.XZC |
| AhnLab-V3 | Win-Trojan/Winlock.131072 |
| AntiVir | TR/Rogue.kdz.12063 |
| BitDefender | Trojan.Generic.KDZ.12063 |
| Kaspersky | Trojan-Ransom.Win32.Foreign.ayat |
| Avast | Win32:LockScreen-TY [Trj] |
| McAfee | RDN/Suspicious.bfr!i |
| AVG | Generic_s.AZA |
| Fortinet | W32/Kryptik.AXUE!tr |
SpyHunter Detects & Remove Mal/FakeAV-OY
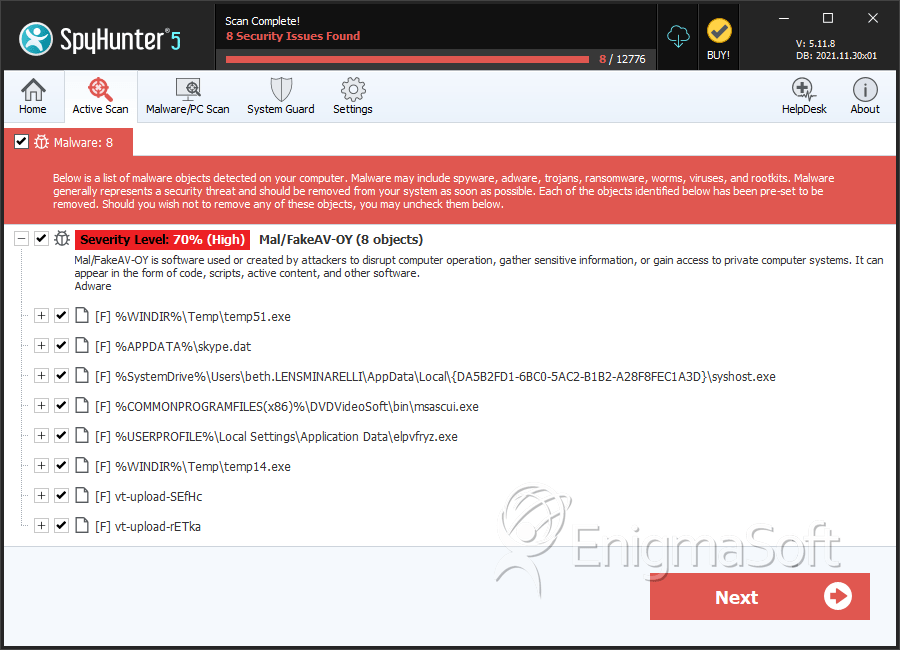
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | syshost.exe | 5e052a45be0d57ac2773527cffce53cf | 10 |
| 2. | temp51.exe | 96fe140aa5f043cf444ed09b5b68a06e | 5 |
| 3. | skype.dat | 5ee7d9868882bde05a1959dfca1c5cc7 | 5 |
| 4. | skype.dat | 8e8d0b99bdc661f184066530fd350458 | 4 |
| 5. | syshost.exe | 55c1be98bc83e01b1f0d32f464f9a49e | 3 |
| 6. | msascui.exe | 08aabc4524d0497b9b605f12facc6865 | 2 |
| 7. | skype.dat | 546e94e145adb806390bd026f5d1fc77 | 2 |
| 8. | elpvfryz.exe | 9d40748f2857fc4cdac5d3cc2909eff7 | 1 |
| 9. | skype.dat | ed3dff7d175b5e63a9e91a1342fb5ed1 | 1 |
| 10. | temp14.exe | c852e49b1522e6d133d2b167dda13d6f | 1 |
| 11. | C:\WINDOWS\system32\Packet.dll | ||
| 12. | C:\WINDOWS\system32\wpcap.dll | ||
| 13. | C:\WINDOWS\system32\drivers\npf.sys | ||
| 14. | vt-upload-SEfHc | f72b5e642e1bac0a7f7aa785f9eefa9e | 0 |
| 15. | vt-upload-rETka | 83ef1298e16845896c3ec95653e33dc0 | 0 |
| 16. | vt-upload-1kf4Y | 9756fce36f22c0f31cdade3f48ab9643 | 0 |
| 17. | vt-upload-VZ7J9 | 8f60c2dd18945811b315d430f0cea485 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.