Dharma Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 20,339 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 26,331 |
| First Seen: | November 17, 2016 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The Dharma Ransomware is an encryption ransomware Trojan that is being used to extort computer users. There have been numerous computers around the world that have been infected by the Dharma Ransomware. The Dharma Ransomware seems to target only the directories inside the Users directory on Windows, with encrypted files receiving the suffix [bitcoin143@india.com].dharma added to the end of each file name. Variants of the Dharma Ransomware will sometimes not have a ransom note. The Dharma Ransomware does not stop the affected computer from working properly, but every time a file is added to the targeted directories, it will be encrypted unless the Dharma Ransomware infection is removed.
Table of Contents
The Dharma Ransomware may Change It’s Name
Some computer users have reported that the file being used to deliver the Dharma Ransomware also may be named 'skanda.exe,' although this depends on the variant being used in the attack. Once the Dharma Ransomware has encrypted a file, it will no longer be readable by the victim's applications until it is decrypted. Unfortunately, to decrypt the files that have been affected by the Dharma Ransomware, it is necessary to have the decryption key, which the people responsible for the Dharma Ransomware will hold until the victim pays a ransom. A different variant of the Dharma Ransomware is contained in a folder named 'opFirlma,' which contained the application 'plinck.exe.' It is highly likely that these are randomly generated. Some variants of the Dharma Ransomware will include a ransom note contained in a text file named 'README.txt,' which will deliver the following message:
'ATTENTION!
At the moment, your system is not protected.
We can fix it and restore files.
To restore the system write to this address:
bitcoin143@india.com'
How the Dharma Ransomware Infection Works
PC security analysts suspect that the Dharma Ransomware is one of the many variants of the infamous Crysis Ransomware family, which was responsible for numerous attacks since Summer of 2016. The Dharma Ransomware and its variants seem to be distributed using corrupted email attachments that will often exploit vulnerabilities in macros on the victim's computer. It is possible that the Dharma Ransomware is still under development since some samples of the Dharma Ransomware appear to be incomplete, often not containing ransom notes or other basic functions of these attacks. The Dharma Ransomware infection is fairly typical of these encryption ransomware attacks. The Dharma Ransomware uses the AES-256 encryption to take over the victim's data, preventing computer users from accessing their files. The Dharma Ransomware attacks will target the following directories:
- %UserProfile%\Desktop
- %UserProfile%\Downloads
- %UserProfile%\Documents
- %UserProfile%\Pictures
- %UserProfile%\Music
- %UserProfile%\Videos
Dealing with the Dharma Ransomware
PC security analysts strongly advise computer users against paying the Dharma Ransomware ransom. It is very unlikely that the people responsible for the Dharma Ransomware will provide the means to decrypt the infected files, especially in the case of the Dharma Ransomware, where it is clearly still under development. In fact, it is equally likely that the people responsible for the Dharma Ransomware attack will simply ask the victim to pay more money or simply ignore the victim's requests.
As with most encryption ransomware Trojans, the best solution to the attack is to take steps to establish a good backup system. This way, computer users can recover from a Dharma Ransomware attack by restoring their files from the backup copy, with no need to pay the ransom. In fact, if having file backups becomes a regular, widespread practice, attacks like the Dharma Ransomware will likely cease to exist, since the people responsible for these threats will no longer have any way to force computer users into paying the ransom to regain access to their own files. Malware analysts also advise computer users to take care when handling emails, since the Dharma Ransomware may spread through corrupted email attachments.
SpyHunter Detects & Remove Dharma Ransomware
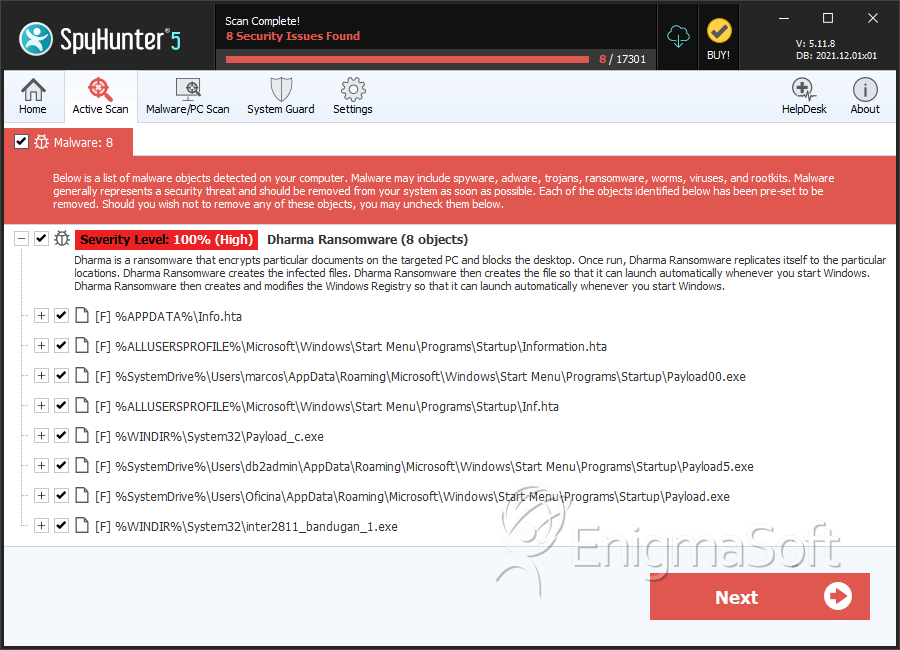
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Payload00.exe | faccdfb32516a9c2dbe714a73712b764 | 104 |
| 2. | Information.hta | 16ccedd463222fbfa8b7e2678d892a7c | 51 |
| 3. | Inf.hta | 1bf867566ccfc201dcf9688a9a21d80b | 46 |
| 4. | Payload5.exe | b097e84cd3abd15f564f1e0b77cb2d50 | 26 |
| 5. | inter2811_bandugan_1.exe | 703c42e5456731444cf68cc27fdfbe96 | 24 |
| 6. | explorer.exe | 674bfb3719ce1b9d30dd906c20251090 | 22 |
| 7. | setap28.exe | 1e1bf7697917466739cb5d8c9b31f7d3 | 19 |
| 8. | Payload(1)_c.exe | 7fb036338464c8dcf226c8b269227b65 | 17 |
| 9. | Payload2.exe | a9f94a2a8501bf15d8ac1eef95cce3e4 | 16 |
| 10. | Payload0.exe | 17bf92deca1953c6ebf2aafb5bf8ebf1 | 15 |
| 11. | Info.hta | 6dddb8c4f20b570a0200beca9bb1f7f2 | 12 |
| 12. | payload.exe | d1487253cee49b68aebae1481e34f8fd | 11 |
| 13. | setap30.exe | eb39803ca6b4540d3001562e07e30ed7 | 10 |
| 14. | setap2.exe | b57d4e839a2f367c64c93ac0860c933c | 10 |
| 15. | Payload31.exe | db2a372dfcaa0dbba4aaff2eaeb5e516 | 9 |
| 16. | Payload30.exe | f6fafa7b9508f9f03ed6c8e4f43f3bb4 | 8 |
| 17. | Payload12.exe | d8f6ff36e853b4ea86b7d8b771ea2a89 | 8 |
| 18. | payload_CHKS26_c.exe | 52d740c82f8d0437cf877d688c7a91a7 | 8 |
| 19. | Payloadn_c.exe | 8d88bb7595cc40e311740c9487684020 | 7 |
| 20. | Payload03.exe | cdc19024a2e99c62987dc2c29b7c4322 | 7 |
| 21. | setap00.exe | 5c2fda3a416193055cc02a6cc6876ca7 | 3 |
| 22. | 1801.exe | 44d550f8ac8711121fe76400727176df | 3 |
| 23. | setap_c.exe | 72ec9b3d1079d3236481a626295a9bb6 | 1 |
