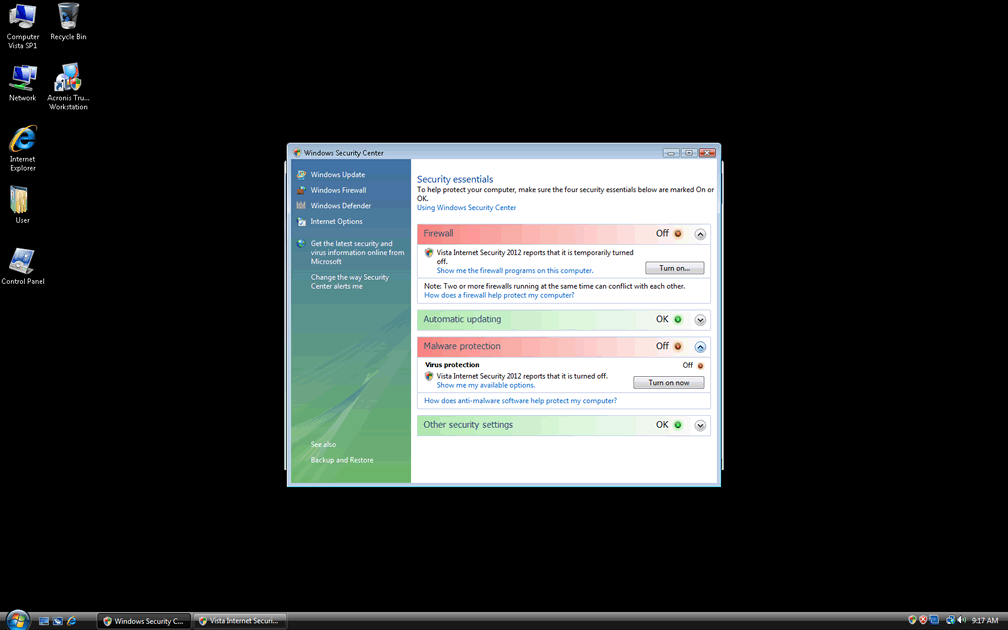
Windows Vista Internet Security 2012
Windows Vista Internet Security 2012 is a fake security program that is part of a huge family of rogue anti-spyware programs. Some clones of Windows Vista Internet Security 2012 include Windows 7 Internet Security 2012, Windows XP Internet Security 2012, Windows Vista Antivirus 2011 and many others. According to ESG security researchers, Windows Vista Internet Security 2012 is nothing more than a clone of previous incarnations of the FakeRean family, the malware infection behind this dangerous rogue anti-spyware application. Criminals have simply made slight tweaks to this program's interface and design in order to add '2012' to its name, fooling users into thinking that there was some kind of update to a previous security program. However, since no version of Windows Vista Internet Security 2012 has legitimate anti-malware capabilities, it makes no difference whether the program is supposedly designed for Windows XP, Vista or Windows 7, or whether Windows Vista Internet Security 2012 is the supposed 2010, 2011, or 2012 version; all versions of Windows Vista Internet Security 2012 are fake and designed to prey on inexperienced computer users.
FakeRean is a big family of rogues security programs. Among its members we can mention Antivirus 2008, Windows Antivirus 2008, Vista Antivirus 2008, Antivirus Pro 2009, AntiSpy Safeguard, ThinkPoint, Spyware Protection 2010, Internet Antivirus 2011, Palladium Pro, XP Anti-Virus 2011, CleanThis, PC Clean Pro, XP Home Security 2012, Windows Clear Problems, XP Security 2012, Antivirus PRO 2015.
Table of Contents
How Windows Vista Internet Security 2012 Steals Its Victims’ Money
Like most rogue security applications, Windows Vista Internet Security 2012 pretends that the victim's computer system is severely infected with malware and then attempts to charge the victim for a useless 'license' in order to remove the imaginary problems. In fact, there is a malware infection on the victim's computer, but not the ones that Windows Vista Internet Security 2012 supposedly detects. Rather, it is Windows Vista Internet Security 2012 itself that is infecting the victim's computer system and causing a series of problems. Some symptoms of a Windows Vista Internet Security 2012 infection include a constant stream of error messages and fake system alerts, a noticeable system slowdown and constant crashes and problems connecting to the Internet or accessing certain files and applications. ESG security researchers strongly advice against falling for Windows Vista Internet Security 2012's scam. Instead of paying attention to the claims that Windows Vista Internet Security 2012 makes, ESG malware analysts recommend using a legitimate (and real, of course) anti-malware program to remove Windows Vista Internet Security 2012 and all other malware that may be accompanying this infection. Do not become a victim and do not let the criminals behind Windows Vista Internet Security 2012 profit from infecting your computer. Fight back by using a reliable anti-malware program and following basic online security guidelines when browsing the Internet.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\Local\[RANDOM CHARACTERS].exe | |
| 2. | %Temp%\[RANDOM CHARACTERS] | |
| 3. | %AppData%\Local\[RANDOM CHARACTERS] | |
| 4. | %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS] | |
| 5. | %AllUsersProfile%\[RANDOM CHARACTERS] |