XP Security 2012
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 41 |
| First Seen: | August 9, 2011 |
| Last Seen: | November 10, 2020 |
| OS(es) Affected: | Windows |
XP Security 2012 Image
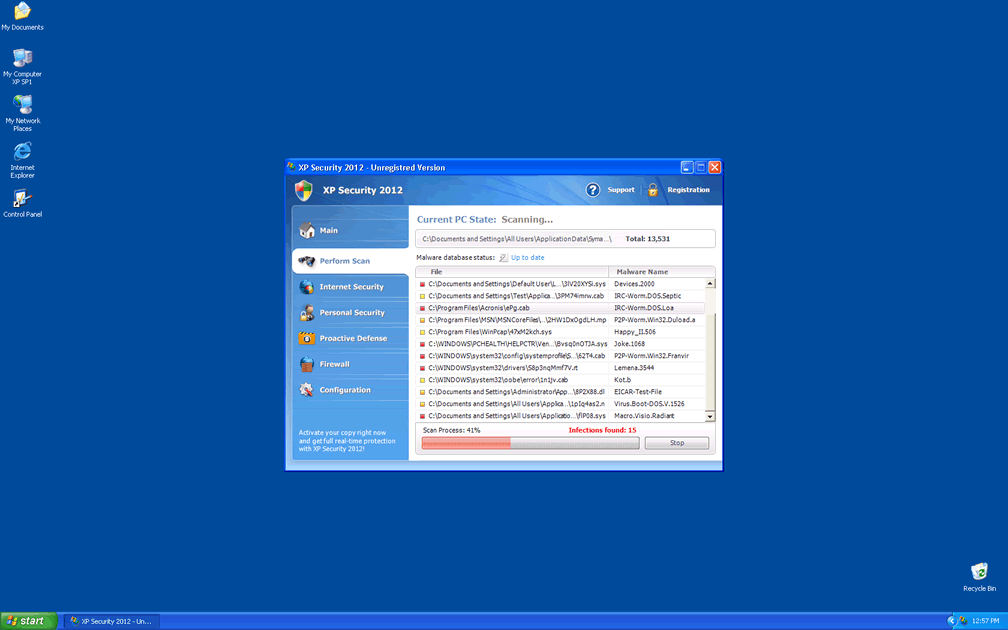
In the year 2011, the Internet was flooded with dozens of versions of the malicious file Ppn.exe. XP Security 2012 is one of the many different faces of this harmful file. Every day there are new names and skins for the Ppn.exe process, making it quite difficult for security experts to keep track of the exact number of disguises this shifty file can use.
Table of Contents
How XP Security 2012 Tries to Trick You
XP Security 2012 is part of a scam that tries to trick users into thinking that their computer is infected by any number of viruses and spyware. In fact, XP Security 2012 is in itself a malicious security program. XP Security 2012 is designed to disrupt the computer's normal operation and then to scare the user into paying to remove XP Security 2012. This kind of rogue anti-spyware application is known as scareware. XP Security 2012 basic way of working is by disrupting your computer, then running a fake scan, and then disguising itself as a legitimate security application. This rogue security application will then demand that the scared user enter his credit card information to get rid of the supposed virus attack.
What Makes XP Security 2012 Unique?
While the most common rogue anti-spyware applications that came before Ppn.exe could have dozens of clones (differently named copies of the same program,) XP Security 2012 and other versions of Ppn.exe are not technically clones. All of the different versions of Ppn.exe are the same program, with different names and skins to match the user's operating system. That means that a computer user using Windows Vista would not become infected with XP Security 2012 but rather with a version of Ppn.exe specific for Windows Vista. This version of Ppn.exe could be called Vista Security 2012, or any other number of names that make XP Security 2012 seem a legitimate Windows Vista security application.
How Does Ppn.exe Adapt to an Operating System?
Ppn.exe is acquired through a Trojan, a harmful bit of code that uses known security vulnerabilities to enter a computer and deliver XP Security 2012's dangerous payload. The first sign of the Trojan intrusion is a fake notification from the fake Windows Automatic Update which is used to install XP Security 2012. When Ppn.exe has been is been installed, it checks for the user's operating system and downloads skins corresponding to that operating system. There are three sets of skins, each containing a huge amount of possible versions of Ppn.exe with new ones being created each day. There is a Windows XP set, a Windows Vista set, and a Windows 7 set. This version of Ppn.exe, XP Security 2012, is part of the Windows XP set. Similar skins from the other two sets would be named Vista Security 2012 and Windows 7 Security 2012 or Win 7 Security 2012. The skins are designed to look similar to the normal windows and themes from the corresponding operating system. However, careful examination reveals grammatical errors that would never occur in the real Microsoft operating system. There are also slight differences in design, style, and color from the normal Windows themes and windows.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| AVG | Win32/Cryptor |
| Fortinet | W32/FakeAV.AT!tr |
| Symantec | VirusDoctor!gen12 |
| NOD32 | a variant of Win32/Kryptik.AHQA |
| Ikarus | Win32.SuspectCrc |
| Sophos | Troj/Spycos-A |
| AntiVir | TR/ATRAPS.Gen |
| DrWeb | Trojan.DownLoad3.8200 |
| BitDefender | Gen:Variant.Zusy.4821 |
| Kaspersky | Trojan.Win32.Zapchast.accf |
| Sophos | NirCmd |
| ClamAV | PUA.Packed.PECompact-1 |
| eSafe | Win32.Tool.NirCmd |
| McAfee | Artemis!22C79223CAB4 |
| Panda | Generic Trojan |
SpyHunter Detects & Remove XP Security 2012
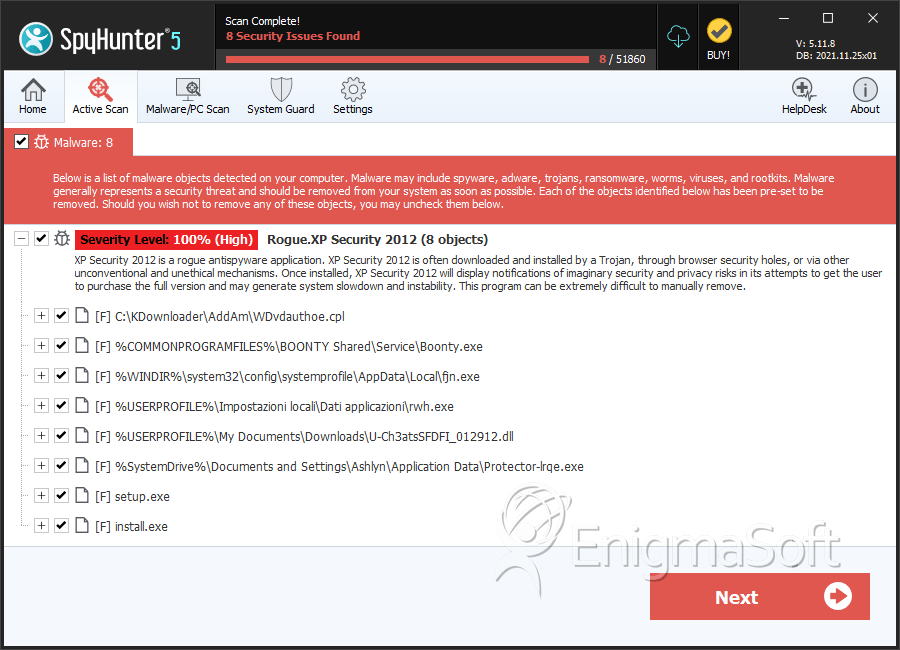
XP Security 2012 Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | WDvdauthoe.cpl | ae0c989485969d8b48a65b7c96b5a88a | 23 |
| 2. | Boonty.exe | 8842fabd13e8e3f1a85854aa70d15ba0 | 3 |
| 3. | fjn.exe | 5f4ef2db6bcaff93b96025b60ed03fae | 1 |
| 4. | rwh.exe | 31d5dbdc23d510e4fed060c167ce06f4 | 1 |
| 5. | U-Ch3atsSFDFI_012912.dll | 1d80d09144d6e714627dbdbd55b0acfd | 1 |
| 6. | Protector-lrqe.exe | 32b652fee344c25f4bfed0ca2a472b1f | 1 |
| 7. | %AppData%\Local\[random].exe | ||
| 8. | %AppData%\Roaming\Microsoft\Windows\Templates\[random] | ||
| 9. | %AppData%\Local\[random] | ||
| 10. | %AllUsersProfile%\[random] | ||
| 11. | %Temp%\[random] | ||
| 12. | setup.exe | d91454e0e028db3aad86196f404676af | 0 |
| 13. | install.exe | a8a1ec0be621d5e5237e5057d428640a | 0 |
| 14. | cht.exe | 01c8cd4e532465a3a3a90137cc200ccb | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.