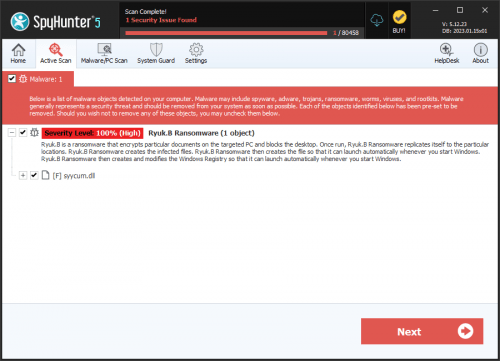
Ryuk Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 14,698 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 736 |
| First Seen: | August 28, 2018 |
| Last Seen: | September 14, 2023 |
| OS(es) Affected: | Windows |
Ryuk Ransomware Image
The Ryuk Ransomware is a data encryption Trojan that was identified on August 13th, 2018. It appears that private companies and healthcare institutions have been compromised with the Ryuk Ransomware. Threat actors were reported of infecting organizations in the USA and Germany. Initial analysis suggests the threat was injected in systems through compromised RDP accounts, but it is possible that there is a parallel spam campaign that carries the threat payload as macro-enabled DOCX and PDF files.
Table of Contents
General Facts and Attribution
Ryuk Ransomware appeared in the middle of August 2018 with several well-planned targeted attacks against major organizations worldwide, encrypting data on infected PCs and networks and demanding the payment of a ransom in exchange for a decryptor tool. Ryuk does not demonstrate extremely advanced technical skills, however, what distinguishes it from other ransomware is the huge ransom it demands. The amount depends on the size of the affected organization, while research shows the attackers have already pocketed nearly $4 million in extortion money from their victims with an average ransom payment of $71,000 worth of Bitcoin - ten times the amount typically demanded by other malware of that kind. As of January 2019, the lowest ransom amount that Ryuk has asked for is 1.7 BTC, while the highest is 99 BTC. The number of known transactions is 52, and the proceeds have been split across 37 BTC addresses.
Cybersecurity researchers have noticed similarities between the Ryuk campaign and another ransomware called HERMES which is attributed to a state-sponsored North Korean APT group known as Lazarus Group. At Ryuk's first appearance, researchers believed it had been built upon the HERMES source code, either by the same hacking group or by another actor who has obtained the code from underground malware forums. Certain similarities between Ryuk and HERMES lead to that conclusion. The two ransomware threats share identical code segments, several strings in Ryuk refer to Hermes, and also when Ryuk launches, it checks each encrypted file for a HERMES marker in order to find out whether the system has already been attacked by HERMES. There are some crucial differences as well, and since the final recipient of the fraudulent payments from Ryuk cannot be determined as the malware operators transfer the funds through many different Bitcoin wallets, the attribution of the ransomware is still a matter of speculation.
At the same time, there is evidence the cybercriminals behind Ryuk come from Russia or its former sateлlite states. For example, the Russian language has been found in some of the encrypted files, along with some cultural reference within the communication with the victims. Another theory is that more than one crew is operating Ryuk since in some reported cases the hacking group demanded a fixed amount, while in others it was ready to negotiate.
Notable Attacks
In October 2017 HERMES ransomware was used as part of a sophisticated SWIFT attack against a major bank in Taiwan that stole $60 million. Experts believe that at that time HERMES had been delivered to the bank's network only as a diversion. That is probably not the case with Ryuk as most researchers believe that its main goal is the extortion of the ransom from the targeted institutions.
Ryuk ransomware is used exclusively for tailored attacks, and its encryption mechanism is developed to serve small-scale operations that only affect crucial assets and resources stored in the targeted network. The greatest Ryuk blast happened around Christmas 2018 when the ransomware launched its Holiday campaign. First, the malware attacked the cloud hosting provider Dataresolution.net, according to the victim itself, by using a compromised login account. The company claims that no customer data has been compromised, however, considering how the malware makes its way into the targeted network, such claims do not sound very plausible.
Multiple newsprint organizations related to the Tribune Publishing media became the next victim of Ryuk right after Christmas. The ransomware attack prevented the organizations from printing their own papers, and it was discovered after an editor could not send finished pages to the printing press. Some researchers claim that the malware that attacked Dataresolution.net and Tribune Publishing is a new version of Ryuk named Cryptor2.0.
Previously, on October 15, 2018, Ryuk attacked the Onslow Water and Sewer Authority (OWASA), causing disruptions in their network. Though the main services and the customer data remained untouched, a significant number of databases and systems needed to be completely build up due to the ransomware attack.
This Week in Malware Video: Episode 1 covering the triple threat campaign of Emotet, Trickbot & Ryuk Ransomware are stealing and ransoming data.
Distribution
Previously, it has been assumed that Ryuk is distributed as a primary infection through malicious email attachments and insufficiently protected RDPs. However, the limited number of attacks against selected high-profile organizations suggest that Ryuk is distributed and operated manually. That means that each attack must be individually and carefully prepared, which includes extensive network mapping and collection of credentials. These observations suggest the attackers have been already familiar with the targeted domains through other malware infections before they could install Ryuk.
In confirmation of that theory, the latest research from January 2019 shows that Ryuk spreads mostly as a secondary payload, installed manually by attackers on machines that have already been infected with Emotet and TrickBot botnets. The primary method of infection that Emotet uses is through spam email campaigns with attached Microsoft Office documents corrupted with malicious scripts. The attackers use various social engineering techniques to make the user open the attachments and click "Enable content," which in turn, launches the malicious scripts and allows the malware to get installed on the target machine. The main hypothesis is that Emotet makes the initial infection, spreads laterally through the affected network, and then launches its own malicious campaign, sending additional malware across the infected network. Here, most commonly Emotet drops the TrickBot payload which steals credentials and also can spread laterally across the network. Both Emotet and TrickBot have the functionalities of worms, data stealers, and downloaders of additional malicious programs. Trickbot is then used to drop Ryuk ransomware on the systems of the selected institutions from which the attackers plan to try to extort ransom. The very small fraction of Ryuk infections observed among all Emotet and TrickBot detections suggests, however, that is not a standard operation of the two botnets to infect systems with Ryuk.
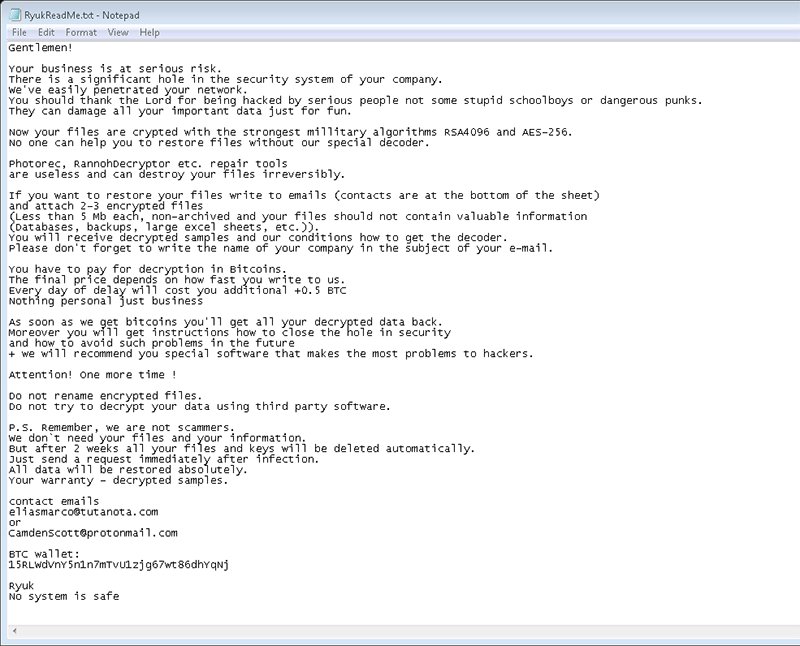
Ransom note
Ryuk ransom note is contained in a file named RyukReadMe.txt which is placed on the desktop, as well as in all folders. Ryuk displays two variants of ransom notes to its victims. The first one is long, well-written and nicely phrased, and it led to the payment of the highest recorded ransom up to date of 50 BTC, equivalent to $320,000. It looks like it has been displayed during some of the first Ryuk attacks. The second one is much shorter and simpler, however, it also demands fine ransom amounts ranging from 15 BTC to 35 BTC. That implies that there could be two levels of potential victims that the crooks have planned to attack.
Version 1:
"Gentlemen!
Your business is at serious risk.
There is a significant hole in the security system of your company.
We've easily penetrated your network.
You should thank the Lord for being hacked by serious people not some stupid schoolboys or dangerous punks.
They can damage all your important data just for fun.
Now your files are crypted with the strongest millitary algorithms RSA4096 and AES-256.
No one can help you to restore files without our special decoder.
Photorec, RannohDecryptor etc. repair tools are useless and can destroy your files irreversibly.
If you want to restore your files write to emails (contacts are at the bottom of the sheet) and attach 2-3 encrypted files
(Less than 5 Mb each, non-archived and your files should not contain valuable information
(Databases, backups, large excel sheets, etc.)).
You will receive decrypted samples and our conditions how to get the decoder.
Please don't forget to write the name of your company in the subject of your e-mail.
You have to pay for decryption in Bitcoins.
The final price depends on how fast you write to us.
Every day of delay will cost you additional +0.5 BTC
Nothing personal just business
As soon as we get bitcoins you'll get all your decrypted data back.
Moreover you will get instructions how to close the hole in security and how to avoid such problems in the future
+ we will recommend you special software that makes the most problems to hackers.
Attention! One more time !
Do not rename encrypted files.
Do not try to decrypt your data using third party software.
P.S. Remember, we are not scammers.
We don't need your files and your information.
But after 2 weeks all your files and keys will be deleted automatically.
Just send a request immediately after infection.
All data will be restored absolutely.
Your warranty - decrypted samples.
contact emails
eliasmarco@tutanota.com
or
CamdenScott@protonmail.com
BTC wallet:
15RLWdVnY5n1n7mTvU1zjg67wt86dhYqNj
No system is safe"
Version 2:
"All files on each host in the network have been encrypted with a strong algorithm.
Backups were either encrypted or deleted or backup disks were formatted.
Shadow copies also removed, so F8 or any other methods may damage encrypted data but not recover.
We exclusively have decryption software for your situation
No decryption software is available in the public.
DO NOT RESET OR SHUTDOWN - files may be damaged.
DO NOT RENAME OR MOVE the encrypted and readme files.
DO NOT DELETE readme files.
This may lead to the impossibility of recovery of the certain files.
To get info (decrypt your files) contact us at
MelisaPeterman@protonmail.com
or
MelisaPeterman@tutanota.com
BTC wallet:
14hVKm7Ft2rxDBFTNkkRC3kGstMGp2A4hk
Ryuk
No system is safe"
The body of Ryuk ransom notes does not change across cases with the exception of the contact email addresses and the given BTC wallet address. The ransom note usually contains one address at tutanota.com and one at protonmail.com, while the names of the emails often belong to Instagram models or other famous people. It is remarkable that the second version of Ryuk ransom note resembles very much BitPaymer ransom notes, yet it is unknown how the actors behind the two ransomware threats are related to each other.
Newer versions of Ryuk display a ransom note that contains only email addresses but no BTC wallet addresses. It reads the following:
"Your network has been penetrated.
All files on each host in the network have been encrypted with a strong algorithm.
Backups were either encrypted Shadow copies also removed, so F8 or any other methods may damage encrypted data but not recover.
We exclusively have decryption software for your situation. More than a year ago, world experts recognized the impossibility of deciphering by any means except the original decoder. No decryption software is available in the public. Antivirus companies, researchers, IT specialists, and no other persons cant help you encrypt the data.
DO NOT RESET OR SHUTDOWN - files may be damaged. DO NOT DELETE readme files.
To confirm our honest intentions.Send 2 different random files and you will get it decrypted. It can be from different computers on your network to be sure that one key decrypts everything. 2 files we unlock for free
To get info (decrypt your files) contact us at cliffordcolden93Qprotonmail.com Or Clif fordGolden93@tutanota.com
You will receive btc address for payment in the reply letter Ryuk No system is safe."
Technical Characteristics
Similarly to HERMES, Ryuk uses RSA-2048 and AES-256 encryption algorithms. Also, both malware threats use Microsoft SIMPLEBLOB format to store keys in the malware's executable, and both use the marker "HERMES" to check whether a file has been encrypted. A major difference is how Ryuk handles file access, as well as the use of a second embedded public RSA key. While HERMES generates a private RSA key for each victim, Ryuk uses two public RSA keys which are embedded into the executable. Since there is no victim-specific private key, all hosts can be decrypted with the same decryption key. That appears to be a weakness in the Ryuk build, however, that is not the case because the malware creates a unique key for each executable whereby a single executable is used for a single target organization. Therefore, even if the key is leaked, it will decrypt only the data encrypted by the corresponding executable. It seems very likely that Ryuk generates an RSA key pair for each victim before the attack.
Ryuk operation includes two types of binaries - a dropper and an executable payload. The dropper can rarely be analyzed as the executable payload deletes the dropper after installation is complete. Upon execution, the dropper creates an installation folder path depending on the version of Windows running on the target host. For example, for Windows XP the malware's folder path would be C:\Documents and Settings\Default User, while for Windows Vista it would be C:\Users\Public. Then, the malware creates a random name for the executable file consisting of five alphabetic characters. After that, the dropper writes and runs the corresponding 32- or 64-bit version of the embedded payload executable. It is, namely, this executable payload written by the dropper that contains Ryuk's logic for encrypting the files on the host. Ryuk tries to encrypt all accessible files and hosts which have Address Resolution Protocol (ARP) entries, except for CD-ROM drives. A file extension ".ryk" is appended to each encrypted file, while all directories also contain the ransom note RyukReadMe.txt.
Latest builds of Ryuk do not have any persistence functionalities. Unlike other known ransomware families, Ryuk currently does not have embedded process/service termination and anti-recovery functionalities as well. Also, In order to disable the Windows System Restore option through which victims might try to recover their data, Ryuk deletes any existing shadow copies of the encrypted files.
Unlike common ransomware threats, Ryuk does not put Windows system files on the whitelist of files that should not be encrypted, meaning that it has no mechanism to ensure the stability of the host. Remarkably, other executable file types are also not on the list of files that should not be encrypted, like system drivers (.sys) and OLE control extensions (.ocx). Many crucial folder names are not on the whitelist as well. For example, Ryuk has been often observed attempting to encrypt Windows Bootloader files, which threatens to make the infected machine unstable and even unbootable over time. In fact, Ryuk whitelists only three file extensions - .exe, .dll, and hrmlog, whereby the last one seems to be a debug log filename created by the original HERMES malware. Folder names that are on Ryuk's whitelist are Mozilla, Chrome, Microsoft, Windows, Recycle.bin, AhnLab. Here is another similarity to HERMES - both malware threats whitelist a folder named "AhnLab" - the name of popular security software from South Korea.
The Ryuk Ransomware is known to run from the Temp folder with a random name and save a ransom note on the user's desktop that is titled — 'RyukReadMe.tx.' The team behind the Ryuk Ransomware may attempt to drop the threat to connected computers via shared folders and non-password protected network drives. The Ryuk Ransomware enciphers text, spreadsheets, eBooks, presentations, databases, images, video and audio files securely. You need to have a good backup solution in place to counter the Ryuk Ransomware and restore data if need be. Strict access policy and active monitoring will help you limit the spread of the threat and the damages it can cause on your organization. AV companies block the files related to the Ryuk Ransomware and mark them as:
Ransom_RYUK.THHBAAH
TR/FileCoder.lkbhx
Trojan ( 0053a8e51 )
Trojan-Ransom.Ryuk
Trojan-Ransom.Win32.Encoder.em
Trojan.GenericKD.31177924 (B)
Trojan.Win64.S.Ryuk.174080
Trojan/Win64.Ryukran.R234812
W64/Trojan.PIZE-2908
Incidents reports show that the original threat developers switched to using the 'WayneEvenson@protonmail.com' and the 'WayneEvenson@tutanota.com' email accounts for their ransomware campaign. The 'wayneevenson@protonmail.com' Ransomware may run as 'PdTlG.exe' on compromised machines, but you should note that it may use random file names. A new trait introduced with the 'wayneevenson@protonmail.com' Ransomware appears to be the automatic loading of the ransom message via a Microsoft's Notepad application to the user's desktop. We continue to track the Ryuk Ransomware behavior and new attack vectors that are being exploited to deliver the product to unsuspecting users. You should employ the services of a powerful backup manager and disable loading macros from untrusted sources. Detection rules for the 'wayneevenson@protonmail.com' Ransomware are supported by most AV vendors that tag related files with the following alerts:
Dropper/Win32.Ryukran.R234915
Ransom.Jabaxsta!1.B3AA (CLASSIC)
Ransom/W32.Ryuk.393216
Ransom:Win32/Jabaxsta.B!dr
TR/FileCoder.biysh
Trojan ( 0053a8931 )
Trojan.Agentbypassg
Trojan.Invader.bsk
Trojan.Ransom.Ryuk
Trojan.Ransom.Ryuk.A (B)
Trojan.Ransom.Win32.1398
SpyHunter Detects & Remove Ryuk Ransomware
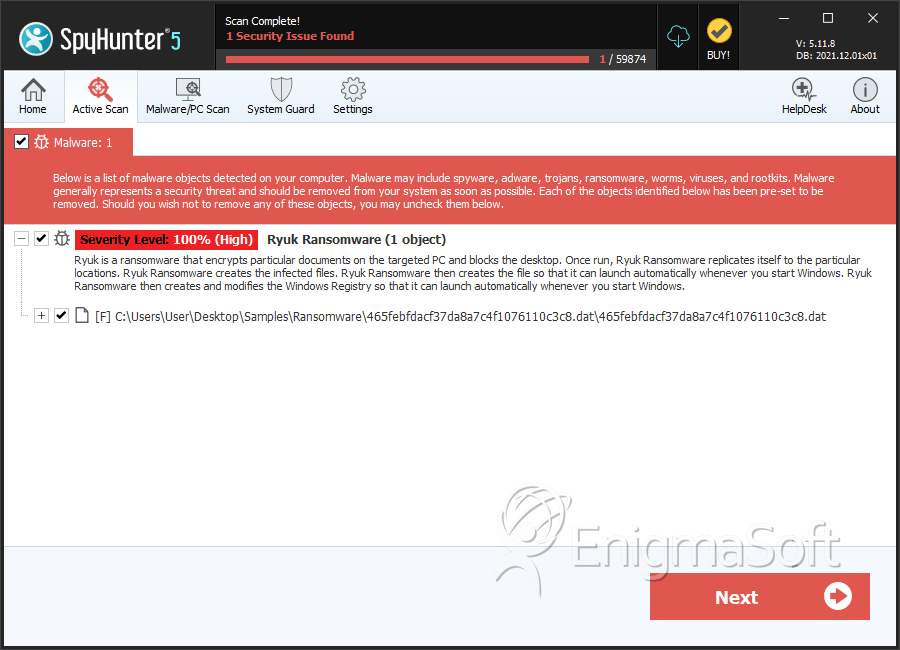
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 465febfdacf37da8a7c4f1076110c3c8.dat | 465febfdacf37da8a7c4f1076110c3c8 | 7 |
| 2. | RyukReadMe.txt |