DarkSide Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | January 23, 2014 |
| Last Seen: | May 16, 2021 |
| OS(es) Affected: | Windows |
 DarkSide Ransomware is a type of malware that is created for the purpose of extorting money from computer users through holding their PC for hostage. The task of DarkSide Ransomware accomplishing its money extortion scheme starts with it encrypting files, which takes place after loading on a system often due to the user opening a malicious spam email attachment.
DarkSide Ransomware is a type of malware that is created for the purpose of extorting money from computer users through holding their PC for hostage. The task of DarkSide Ransomware accomplishing its money extortion scheme starts with it encrypting files, which takes place after loading on a system often due to the user opening a malicious spam email attachment.
The DarkSide Ransomware is known to encrypt many files and append them with similar file extensions. While each file encrypted by DarkSide Ransomware can be easily identified and found, they cannot be accessed or opened due to undefeatable encryption. Due to such, a computer user wanting to get their system back to normal operation will have to make a choice of either paying the ransom or finding another process to remedy the issue.

DarkSide was found to be a culprit in the attack that has shut down the Colonial Pipeline, considered the largest US fuel pipeline responsible for carrying nearly half of the fuel consumed by the East Coast of the United States. Officials are currently investigating the attack where it looks to be a ransomware threat attacking systems controlling the pipeline, which could negatively affect the prices of fuel and make a massive economic impact to the area.
Table of Contents
What Does DarkSide Want?
Since the DarkSide Ransomware campaign shut down the Colonial Pipeline, it is natural to suspect that there could be political aims behind the attack. After all, the scopes of cyberwarfare have only been growing in the last few years, and it would not be surprising if this were a nation-funded attack. Some researchers also suggest that that an Eastern European hacker group could be behind DarkSide Ransomware because this infection does not encrypt a system if its language is set to Russian, Ukrainian, and Armenian. Nevertheless, through their website, DarkSide’s developers claimed that disrupting the fuel system was never one of their aims, and their only objective was financial gain.

It should also be pointed out that DarkSide does not manage every single attack directly. The hackers have many affiliates that use DarkSide Ransomware, and those affiliates can choose their own targets. It would seem that the Colonial Pipeline happened to be picked as a target by one of those affiliates. Consequently, DarkSide claims that they are going to try and avoid social consequences in the future by introducing a clear target review. Not that it sounds any more promising because it just means that the hackers are going to continue infecting other systems.
What Exactly Happened with Colonial?
The most common ransomware distribution method is spam email attachments. With DarkSide Ransomware, it seems that the attack vector was slightly different. The infection must have exploited the COVID-19 pandemic situation, where tons of office workers are now working from home. The same applies to the Colonial Pipeline employees, too.
When someone is working from home, they face a lot more security threats because their home network is seldom as secure as the network at the office. DarkSide Ransomware uses remote desktop protocol applications (such as TeamViewer or Microsoft Remote Desktop) to gain access to Colonial’s systems. They basically brute-forced the account login details that belonged to the Colonial’s employees and entered the sensitive inner system. This would also mean that employees do not use strong passwords to protect their accounts, but that is yet another issue.
Either way, once DarkSide locates the weak link that can be used to access the system, they enter the compromised Virtual Desktop Infrastructure (VDI). Then they make sure that the connection does not get interrupted by deploying another Remote Desktop Protocol through an exploited server. If the original vulnerability used to access the target system gets patched, DarkSide would still retain the system access.
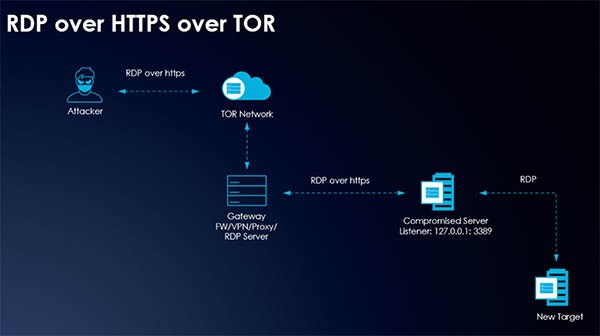
DarkSide Command and Control. Source: Varonis.com
Once the hackers are inside the system, they infect it with DarkSide Ransomware. There are three main stages of the infection. The first one is self-injection, where the malware drops a copy of itself in the %AppData% directory and uses a CMD command to inject its code into an existing process. During this step, DarkSide may stop running if its programming detects that it is being run on a virtual machine.
If the malware does not find any obstructions to its processes, it proceeds to run a stealthy PowerShell command that deletes all backup and shadow copies of the targeted data on the affected machine. That is a common practice among most ransomware infections.
Finally, the third step involves the main pièce de résistance, which is file encryption. Before everything begins, DarkSide Ransomware closes a list of processes that might hinder the encryption process. All the affected files receive an 8-character string at the end of their names, which indicates that they have been encrypted by DarkSide Ransomware.
The same happened to Colonial’s system, where DarkSide successfully stole almost 100GB of data taking it hostage. They threatened to leak it onto the Internet by displaying the following ransom note:
Your network has been locked!
You need pay $2,000,000 now, or $4,000,000 after doubled.
After payment we will provide you universal decryptor for all network.
The amount of $2,000,000 or more demanded by the hacker group, as shown in the actual ransom note image (below) that appears on the pipeline controlling computers, is outrageous.
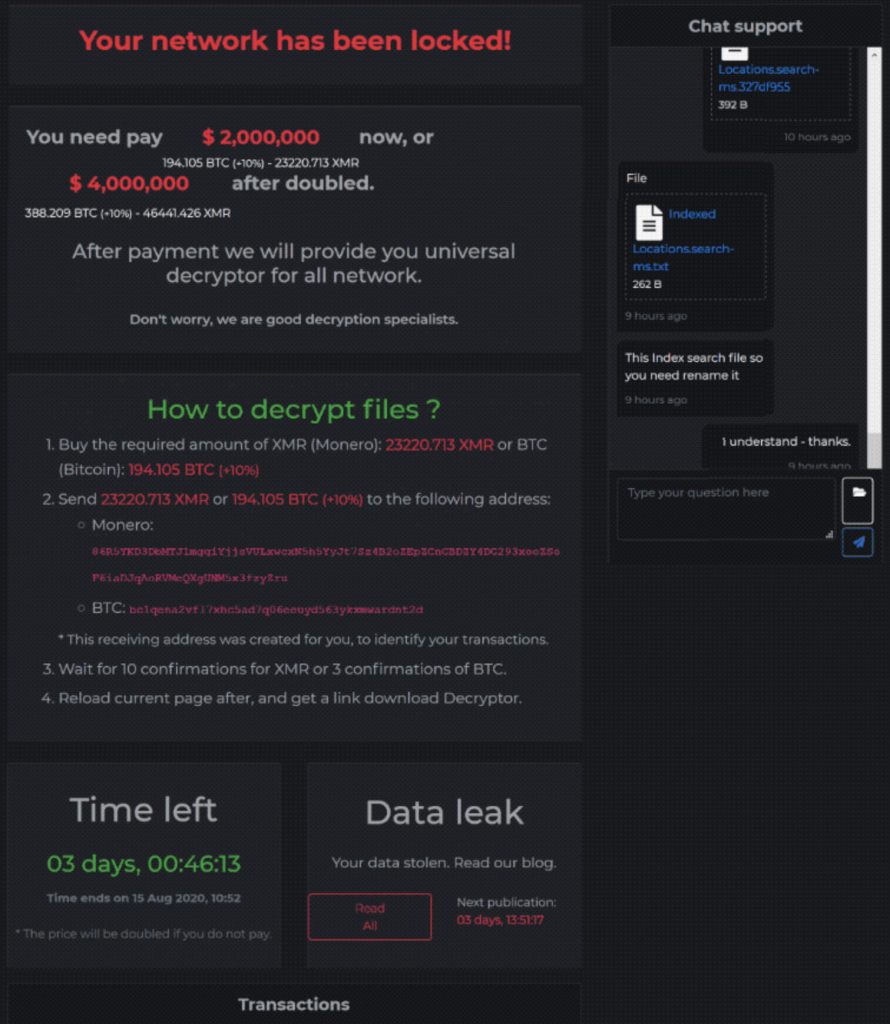
DarkSide Ransomware ransom note image
The ransom note above pops up on the victim’s screen. However, there is another ransom note that is dropped on the target system in a TXT format file. It usually has the "READ ME" phrase in its file name. That note comes with instructions on how to contact the DarkSide team, and here is what it has to say:
------------ [ Welcome to DarkSide ] ------------>
What happend?
-------------------------------------------------
Your computers and servers are encrypted, private data was downloaded. We use strong encryption algorithms, so you cannot decrypt your data.
But you can restore everything by purchasing a special program from us - universal decryptor. This program will restore all your network.
Follow our instructions below and you will recover all your data.
Data leak
-------------------------------------------------
First of all we have uploaded more then _ data.
Your personal leak page (TOR LINK): http://darkside . onion/
On the page you will find examples of files that have been downloaded.
The data is preloaded and will be automatically published in our blog if you do not pay.
After publication, your data can be downloaded by anyone, it stored on our tor CDN and will be available for at least 6 months.
We are ready:
- To provide you with the evidence of stolen data
- To delete all the stolen data.
What guarantees?
-----------------------------------------------
We value our reputation. If we do not do our work and liabilities, nobody will pay us. This is not in our interests.
All our decryption software is perfectly tested and will decrypt your data. We will also provide support in case of problems.
We guarantee to decrypt one file for free. Go to the site and contact us.
HOW TO CONTACT US?
-----------------------------------------------
Use a TOR browser:
1) Download and install TOR browser from this site: https://torproject.org/
2) Open our website: http://darkside. onion/
Needless to say, the ransom is supposed to be paid in BTC, but instead of scrambling to pay for the stolen data, Colonial addressed the FBI and other government and private agencies to help them mitigate the damage. The cloud computing systems that contained the encrypted information were taken offline to contain the threat, and that was essentially what caused the disruption in the East Coast’s fuel supply.
With the story still developing, no actual ransom payments were announced, and we can only guess how much Colonial will pay for the encrypted data or whether it would be paying anything at all. Previous attack instances suggest that DarkSide does not show empathy to companies that earn billions of dollars in annual revenue. However, it is possible to negotiate with them, and the negotiation can be swift and effective because DarkSide uses instant chat to communicate with their victims.
Back in January 2021, another U.S. company was hit by the DarkSide Ransomware attack. The cybercriminals demanded $30 million in ransom payment, but the company managed to negotiate an $11 million payment instead, cutting down the price by almost two-thirds.
On the other hand, aside from the encrypted data and the double-extortion tactics, where the victims are being pressured to pay up, DarkSide can also engage in blackmailing. Together with encrypting the sensitive data, the group can also steal it and threaten to leak it if the affected companies refuse to pay for the data release.
What’s more, DarkSide may also harvest login details from various organizations. Instead of notifying those organizations about their security flaws, they sell the harvested information to the highest bidders, thus allowing them to carry out other attacks.
Common Ransomware Trends
This ransomware attack is a clear example of the latest ransomware trends where such attacks can cause a lot of damage on a national level. Ransomware attacks have always targeted businesses as opposed to individual users, but it is now easy to see that vital industrial infrastructure could also be affected by it. Even if DarkSide Ransomware does not become as notorious as WannaCry, it gives additional puzzles to cybersecurity specialists worldwide.
DarkSide Ransomware also displays currently the most prominent ransomware business model where the main developers (DarkSide, in this case) create the malware and then sell it or rent it to its "affiliates." So far, security researchers have identified at least five affiliates associated with the DarkSide ransomware attacks.
In order to become a DarkSide "affiliate," the potential partner has to pass an interview first. Some of the groups that have passed the interview and are working with DarkSide are identified by allocated codenames. Researchers at FireEye indicate some of those groups as UNC2628, UNC2659, and UNC2465.
UNC2465 has been active since April 2019. This group employs phishing emails to deliver DarkSide to its potential victims. The group also uses the Smokedham backdoor to access the target system. UNC2659 and UN2628 are relatively new groups that have been active since the beginning of 2021. UNC2628 tends to proceed with the encryption within two or three days after the infiltration, and it is also believed that this group used to work with REvil, too. UNC2628 takes around ten days after the infection on average before it proceeds with the file encryption, and it maintains persistence on the affected computer by exploiting the TeamViewer software.
Disregarding different infiltration and encryption patterns, when the affiliates infect predetermined targets, the main hacker team receives a percentage of the affiliates’ earnings. Based on various reports, Dark Side gets a 25% cut from the collected ransom payments if the affiliates receive less than $500,000 in ransom payments. If the partners collect over $5ml, the cut goes down to 10% of the earnings. This business model is called ransomware-as-a-service.
To make itself more attractive to potential customers, DarkSide runs a competitive marketing campaign on its website. Even when the ransomware was first released in August 2020, the new product was also announced through a "press release," so the group is very keen and eager to promote themselves.
The team says that although they present a new product, they are by no means newbies in the ransomware field. They also show that they have integrity because they say that they do not attack healthcare, funeral service, education, non-profit, and government institutions. Again, this supports the earlier mentioned claim that DarkSide did not intend to cause social disruptions with its attack on Colonial.
Potential victims are not forgotten in their ad either. DarkSide says the victims can be guaranteed that they will get a one test file decryption and that a decryption key for all the files will be issued once the ransom payment is transferred. They also promise to delete the uploaded files from their servers.
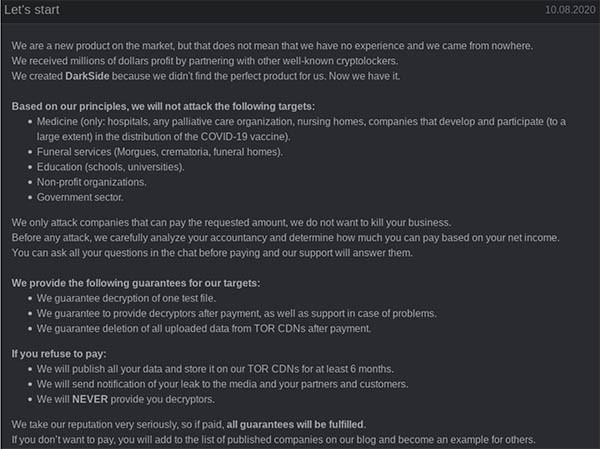
The DarkSide Ransomware advertisement. Source: KrebsOnSecurity.com
Although security experts cannot be 100% sure about this, it is believed that some of the members of the DarkSide team were behind another ransomware infection called REvil. In turn, REvil is thought to be another name for GandCrab, which is yet another ransomware-as-a-service that extorted more than $2bn from its victims before closing its store in 2019.
Such comprehensive threats require multi-faceted solutions. Using powerful anti-malware programs is just one steppingstone in this battle against dangerous hacker groups. It is also important to educate your employees about the potential security threats and vital cybersecurity practices. If an employee manages sensitive information, they have to use strong passwords and secure network configurations when they access the organization’s systems. Otherwise, it would be too easy for something like DarkSide Ransomware to carry out yet another attack.
The obvious is that ransomware is not going anywhere, and such attacks are becoming a pressing issue not only for businesses but also for national security. The average ransomware payments went up by 31% from the second to the third quarter of 2020. And more than 2,400 government agencies, healthcare institutions, and schools were affected by ransomware attacks in the U.S. alone within 2020.
In the DarkSide’s case, they say that the institutions mentioned above are not their main targets, but the attacks are becoming hard to avoid, and this pressing situation is also acknowledged by the Cybersecurity and Infrastructure Security Agency (CISA). On May 11, 2021, the agency released a set of recommendations for "preventing business distribution from ransomware attacks." The list of recommendations includes (but is not limited to):
- Employing multi-factor authentication
- Using spam filters to avoid phishing attacks
- Encouraging user/employee training to help prevent cyberattacks
- Filtering network traffic
- Regular software updates
- Regular data backups
Various news outlets have reported that Colonial did pay almost $5 million in ransom. The company was hit by DarkSide Ransomware last Friday, May 7th, and it reportedly paid the ransom in cryptocurrency merely a few hours after the attack. It is clear that the company paid the ransom to restore stolen data, but such swift payment also raises concerns about future ransomware attacks. It encourages criminals to continue targeting high-profile companies and other businesses that have deep pockets and are more likely to pay the ransom fees.
Also, despite the fact that DarkSide provided the decryption tool to restore the encrypted data, Colonial still had to use their own backups to restore their network because the said tool reportedly was too slow. It is very likely that the decryption tool has its limitations when it has to decrypt hundreds of gigabytes of data.