WannaCryptor or WanaCrypt0r Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | March 29, 2017 |
| Last Seen: | November 15, 2019 |
| OS(es) Affected: | Windows |
WannaCryptor or WanaCrypt0r Ransomware Image
The WanaCrypt0r Ransomware is an encryption Trojan that features a worm-like attack tactic. The WanaCrypt0r Ransomware is recognized as one of the most threatening and widespread encryption Trojans up until May 12th, 2017. The WanaCrypt0r Ransomware managed to compromise more than hundreds of thousand systems across one hundred and forty countries on its first release to the real world. The brunt of the attack was taken by PC users in Russia and the National Healthcare System in Great Britain. The Trojan managed to block access to most of the computers connected to the National Healthcare System and nearly 70% of the cases that involve the WanaCrypt0r Ransomware are recorded in Russia. The WanaCrypt0r Ransomware is a standalone ransomware Trojan, which managed to infect vulnerable machines that run the Windows XP and the Windows Server 2003. The countries that suffered the most damages are the Russian Federation, Ukraine, India, Great Britain and Taiwan.
Table of Contents
Who is Behind the Attack with the WanaCrypt0r Ransomware?
The malware authors behind WanaCrypt0r Ransomware took advantage of a vulnerability that was discovered by the NSA and published for sale by a group of hackers known as 'The Shadow Brokers.' The team wanted to sell a set of tools misappropriated from the NSA but nobody wanted to buy their "products, " and the group uploaded all available resources to the Internet. Evidently, the creators of the WanaCrypt0r found a vulnerability with the code CVE-2017-0145 a.k.a. 'EternalBlue,' which allows a programmer to send a data package crafted specially to an SMB server and execute a corrupted code on the receiver end. The attackers managed to install the 'DoublePulsar' Backdoor Trojan, which allowed them to introduce the WanaCrypt0r Ransomware to the compromised machine and other computers that were connected to it.
Is the WanaCrypt0r Ransomware a Persistent Threat?
PC security researchers reported that the authors of the WanaCrypt0r Ransomware had released three versions, one after the other. Most encryption Trojans are not updated the same week as they are released, but WanaCrypt0r proves that a determined team of hackers can distribute updates and patches comparatively fast. We have seen the Trojan use the names WannaCry, WanaCrypt0r, WCrypt and WCRY. The WanaCrypt0r Ransomware behaves like the infamous Cerber 6 Ransomware and scans the local data storage units for available files. The WanaCrypt0r Ransomware proceeds to connect to a 'Command and Control' server to report the infiltration and download a set of a private encryption key and a public decryption key. The threat is designed to use a customized AES-256 cipher to corrupt text, images, audio, video, presentations, spreadsheets and databases stored on the compromised device. Enciphered objects may feature the following extensions:
- .WNCRY
- .WNCRYT
- .WRCY
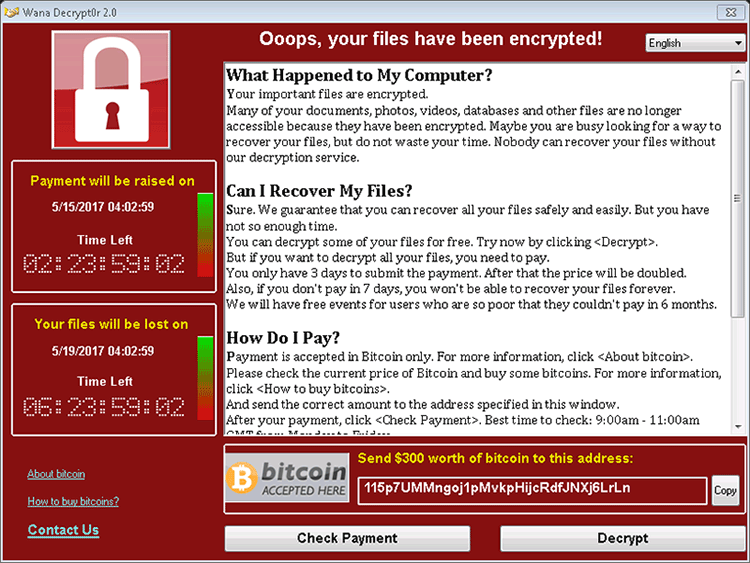
For example, 'The impact of street lighting on months and disruption of nocturnal pollen transport.pptx' may be renamed to 'The impact of street lighting on months and disruption of nocturnal pollen transport.pptx.WNCRYPT.' The encryption may take a few hours on the computers that are used for data storage and thanks to its distribution mechanism the WanaCrypt0r Ransomware might corrupt backups as well. You should note that the WanaCrypt0r Ransomware can terminate the processes of database managers like MySQL, Microsoft Exchange Server and OracleDB. The ransom note is presented in three forms—a TXT file named '@Please_Read_Me@.txt,' a desktop wallpaper named '@WanaDecryptor@.bmp,' and a program window titled 'Wana Decrypt0r 2.0'. The desktop wallpaper offers a brief explanation on why you can't load data on the device and reads:
'Ooops, your important files are encrypted.
If you see this text, but don't see the "Wana DecryptOr" window, then your antivirus removed the decrypt software or you deleted it from your computer.
If you need your files you have to run the decrypt software.
Please find an application file named "@WanaDecryptor@.exe" in any folder or restore from the antivirus quarantine.
Run and follow the instructions!
Cyberattacks come in many different forms
Many people have wondered what exactly happened in the WannaCry cyberattacks and who was mostly affected. It turns out that services across England and Scotland in the healthcare sector where among the entities hit by the large-scale attack that rooted from WannaCrytor (WannaCry). The National Healthcare System in the UK was hit by the attack that ended up compromising countless computers.
The type of cyberattack from the WannaCrytor (WannaCry) threat was initially delivered through email. In the past, we have seen where ransomware threats are primarily spread through emails, which are in the form of spam messages that contain attachments. The attachment within the spam messages that spread WannaCrytor (WannaCry) are malicious and must be accessed or opened by the computer user in order to initiate the malware.
In the past, there are have been many cases of malware spreading through spam message attachments, many of which were known to be malicious PDF or MS Word documents. Such document types are extremely popular and common methods of transmitting information through email. As a cyberattack, the form used by hackers behind WannaCrytor (WannaCry) are well aware of the success rates in spreading malware as an attachment to an email, which often appears to unsuspecting computer users as a harmless attached document.
Spam volume increases equals more malicious attachments spreading WannaCryptor
The volume of spam or phishing-type emails has steadily grown while email is still the number one delivery method for most malware, including ransomware. According to F-Secure, the five most dangerous email attachments remain to be .DOC, .XLS, .PDF, .ZIP and .7z, with 85% of all malicious emails having such files attached. You may recognize the file extension types with .DOC being a MS Word document, .XLS being a MS Excel document, .PDF an Adobe Acrobat file, .ZIP being a compressed Zip file, and .7z being another form of a compressed zip file.
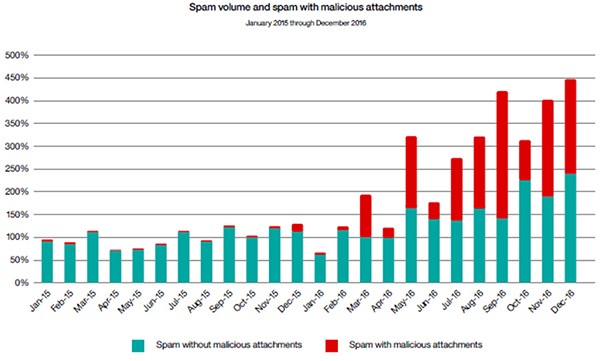
The proliferation of spam emails containing malicious attachment files that are among the top five most dangerous mentioned above has only emboldened hackers further. With such, the spread of WannaCrytor (WannaCry) Ransomware threats and similar variations has been an ongoing struggle that has no end in sight. In 2015 to 2016 alone, spam volumes increased over 350% with nearly half of the volume accounting for spam messages with malicious attachments, as demonstrated below in Figure 1 of the IBM Threat Intelligence Index 2017 chart. Among the malicious spam attachments, ransomware accounted for 85%.
Figure 1. Spam Volume Report Chart from BM Threat Intelligence Index 2017
You Might Have a Way to Avoid Paying
The program window 'Wana Decrypt0r 2.0' offers a countdown timer and urges the user to pay 300 USD via the Bitcoin digital currency to acquire the correct decryption key and initiate the decryption process. As of writing this, there are a little more than one hundred payments made to the wallet address associated with the WanaCrypt0r Ransomware. Given the scale of the attack, there may be more users that are willing to pay since the WanaCrypt0r Ransomware may have deleted backups as well. However, the threat cannot corrupt and erase files that are stored on unmapped memory devices, and you should be able to use offsite backups to rebuild your data structure. Experts recommend regular PC users and companies invest in an offline and cloud-based backup storage for maximum protection against modern-day encryption Trojans. You should take into consideration that the WanaCrypt0r Ransomware is reported to target 166 types of files that include:
.123, .3dm, .3ds, .3g2, .3gp, .602, .accdb, .aes, .ARC, .asc, .asf, .asm, .asp, .avi, .backup, .bak, .bat, .bmp, .brd, .bz2, .cgm, .class, .cmd, .cpp, .crt, .csr, .csv, .dbf, .dch,.der, .dif, .dip, .djvu, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .edb, .eml, .fla, .flv, .frm, .gif, .gpg, .hwp, .ibd, .iso, .jar, .java, .jpeg, .jpg, .jsp, .key, .lay, .lay6, .ldf, .m3u, .m4u, .max, .mdb, .mdf, .mid, .mkv, .mml, .mov, .mp3, .mp4, .mpeg, .mpg, .msg, .myd, .myi, .nef, .odb, .odg, .odp, .ods, .odt, .onetoc2, .ost, .otg, .otp, .ots, .ott, .p12, .PAQ, .pas, .pdf, .pem, .pfx, .php, .png, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .ps1, .psd, .pst, .rar, .raw, .rtf, .sch, .sldm, .sldx, .slk, .sln, .snt, .sql, .sqlite3, .sqlitedb, .stc, .std, .sti, .stw, .suo, .svg, .swf, .sxc, .sxd, .sxi, .sxm, .sxw, .tar, .tbk, .tgz, .tif, .tiff, .txt, .uop, .uot, .vbs, .vcd, .vdi, .vmdk, .vmx, .vob, .vsd, .vsdx, .wav, .wb2, .wk1, .wks, .wma, .wmv, .xlc, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .zip.

