Cerber 6 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 9,198 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 71,874 |
| First Seen: | March 4, 2016 |
| Last Seen: | September 11, 2023 |
| OS(es) Affected: | Windows |
The Cerber family of ransomware is known for its sophistication and its development of cutting- edge threats technology. PC security researchers have noticed a new variant in this family, the Cerber 6 Ransomware, which first appeared in April 2017. The Cerber 6 Ransomware is being delivered in a wide variety of ways and seems to include new encryption methods and attack strategies.
Table of Contents
The Threat Presented by a Cerber 6 Ransomware Attack
The members of the Cerber family have been near the top of the charts of most widely disseminated ransomware threats. In fact, threats in this family accounted for more than 85% of ransomware infections in the first quarter of 2017. The Cerber 6 Ransomware and its previous variants have been responsible for generating millions of dollars for its creators around the world. One of the reasons why the Cerber 6 Ransomware has been especially effective in generating revenue is that it is being distributed as a RaaS (Ransomware as a Service) currently, where con artists pay for the rights to distribute the Cerber 6 Ransomware, sharing the profits with the Cerber Ransomware's creators.
The New Features in the Cerber 6 Ransomware
The Cerber 6 Ransomware features new delivery methods and a newly updated encryption method. The Cerber 6 Ransomware also includes new defense mechanisms and obfuscation, which include techniques that allow the Cerber 6 Ransomware to bypass many security programs or to detect when it is running in a sandbox environment or virtual system (both of which may be used by PC security researchers to study these threats.) It is clear that threats in the Cerber family are being updated constantly and, since its appearance in 2016, with new versions in this family adding new features, staying ahead of malware researchers and security software.
The Cerber 6 Ransomware is being delivered to victims using spam email messages currently. The Cerber 6 Ransomware is being delivered in emails that use social engineering to trick computer users into opening a ZIP file attachment, which itself contains a JS, or JavaScript file. This corrupted JavaScript file downloads and installs the Cerber 6 Ransomware on the victim's computer. The Cerber 6 Ransomware uses a time delay that allows it to avoid certain sandbox environments. There are several features in the Cerber 6 Ransomware that have caught the attention of malware researchers. The Cerber 6 Ransomware will terminate file processes that could interfere with its encryption routine. The Cerber 6 Ransomware will use file extensions to avoid certain files during encryption. The Cerber 6 Ransomware can interfere with the Windows Firewall, blocking certain firewalls and interfering with security software and restrictions. The detection and removal of a Cerber 6 Ransomware infection will be more difficult due to this interference. The Cerber 6 Ransomware also can self-destruct if the computer has characteristics of a virtualized environment.
One aspect of the Cerber 6 Ransomware that makes it different from various other ransomware Trojans is that it has avoided the use of the RSA and RC4 encryption algorithms in its attacks, which are the most commonly used in these attacks. The Cerber 6 Ransomware attack favors the Cryptographic Application Programming Interface to carry out its encryption attack.
Protecting Your Computer from the Cerber 6 Ransomware and Similar Trojans
Despite that the Cerber 6 Ransomware includes advanced new features, the way to protect your computer from the Cerber 6 Ransomware remains the same as with the countless other ransomware variants that have preceded it. Having backup copies of your files on an external memory device remains (and will remain) the best protection against ransomware like the Cerber 6 Ransomware. This is because having the ability to restore the affected files from a backup copy undoes the Cerber 6 Ransomware attack completely since the con artists lose any power they have over the victim.
SpyHunter Detects & Remove Cerber 6 Ransomware
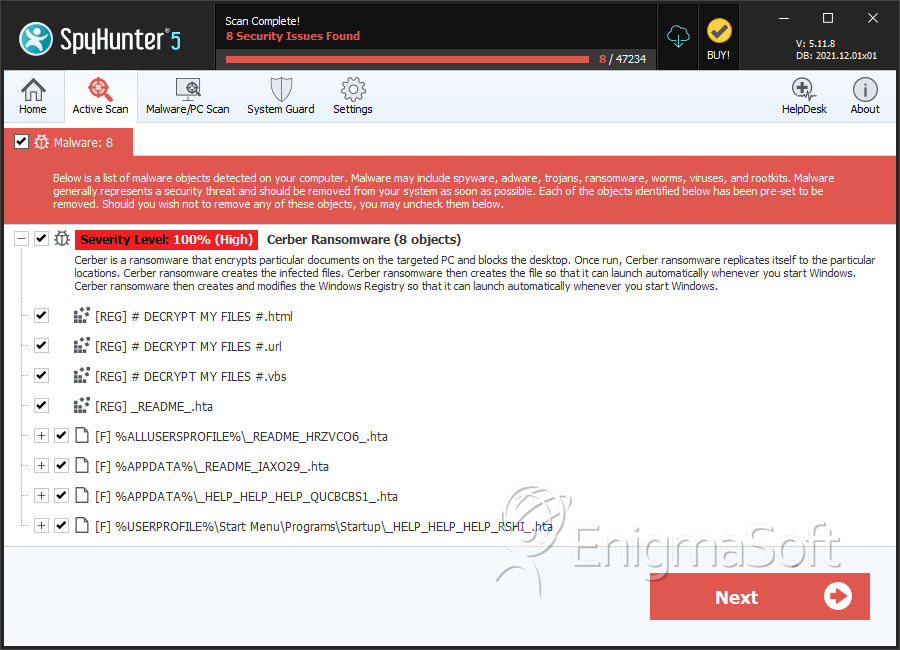
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Readme.hta | e125ef487472bfdd17d7e3e7e237d0d9 | 167 |
| 2. | Readme.hta | 8f85ab4bb455ce6d413eff9e9d47a506 | 54 |
| 3. | README.hta | 777e13c9a5cad4e1d2134d5104188ff6 | 43 |
| 4. | README.hta | c4fff6005b70cccd895082e6c79595b3 | 36 |
| 5. | README.hta | e189ce9640edc95a1ba19d0d4d85691b | 24 |
| 6. | README.hta | 107ab5eae352dab9defab24d3ba77b4a | 18 |
| 7. | _HELP_HELP_HELP_QUCBCBS1_.hta | c042f1d91619e9b4f91bf1e1b78fee85 | 14 |
| 8. | _HELP_HELP_HELP_RSHI_.hta | a46e5f2ce8a20bbb8548959debb9ac0c | 10 |
| 9. | _HELP_HELP_HELP_STOV8H1_.hta | 1632ca0953d5499bf251455159a80ea0 | 6 |
| 10. | _HELP_HELP_HELP_ND8FZ.hta | 041ef4b6a12e0b3165172884301b0d1e | 5 |
| 11. | _HELP_HELP_HELP_Z49XU_.hta | 243d0fd4f4bee5f11698c20d43b958ff | 4 |
| 12. | _HELP_HELP_HELP_XFCV_.hta | 01ec9e50d17de043a23997d6562293ad | 3 |
| 13. | _HELP_HELP_HELP_2AK4U21_.hta | 55790c64ce1ff75647d5cadcadf3876e | 3 |
| 14. | _HELP_HELP_HELP_3NNARI.hta | 0ef13a9213c456db231825061eec294c | 2 |
| 15. | _HELP_HELP_HELP_L41VV_.hta | c63b4a524713e4c5f3802463cb46dab8 | 2 |
| 16. | _READ_THI$_FILE_L81EB65A_.hta | 2a6828d2ba37bb97efb4773619b80715 | 2 |
| 17. | _HELP_HELP_HELP_2R9I63OS.hta | a2daec078c54bb6bc5e96038a1506f2c | 1 |
| 18. | _HELP_HELP_HELP_UYUR4YE.hta | bc0c75128b9cbc02c8c053c1155fb6d9 | 1 |
| 19. | _HELP_HELP_HELP_CKJ4GL.hta | 99d3fc208d3623107cfb18a9069e23bd | 1 |
| 20. | _HELP_HELP_HELP_SUXEZY_.hta | 5190e890725bf431ba44001e190c70f5 | 1 |
| 21. | _HELP_HELP_HELP_GLP9_.hta | 5f7533c663ddb4c0ae4dbbaafb50d491 | 1 |
| 22. | _HELP_HELP_HELP_HUUKTW_.hta | 0224da72bc3638b351cf509cdfc443c2 | 1 |
| 23. | _READ_THI$_FILE_DB3DT9_.hta | 7476a75b0680d99f5338b886bc7def62 | 1 |
| 24. | wP6fT.exe | 731279e3c09f8e52a849c0a9c1043bb5 | 1 |
| 25. | cmdkey.exe | 27cf39d205567505d840391e4761a7a0 | 1 |
| 26. | file.exe | 212fa73fd6ed39b4720bcfd8d97426d5 | 0 |

