Malware Protection
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 5 |
| First Seen: | May 27, 2011 |
| Last Seen: | April 18, 2018 |
| OS(es) Affected: | Windows |
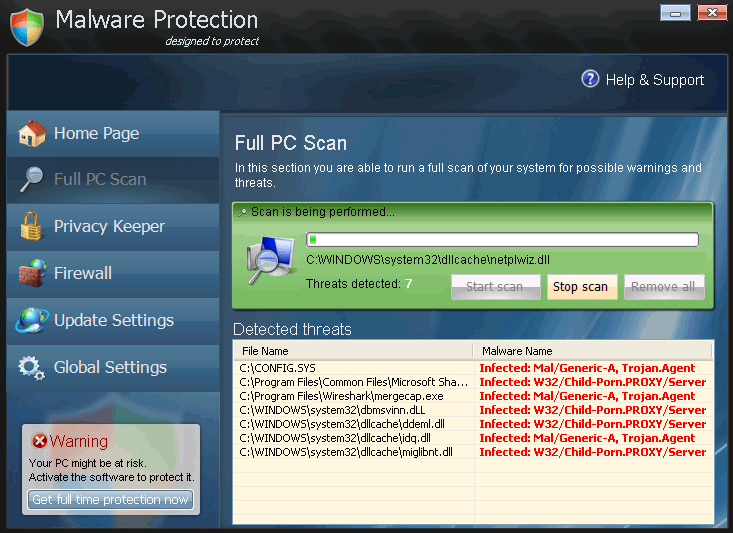
Malware Protection Image
As far as names for fake anti-virus programs go, you can't get more generic than "Malware Protection." It certainly ought to seem suspicious if you have a program popping up on your computer, telling you all kinds of things about the state of your system's security, and it will not even tell you which company produced it! Of course, because Malware Protection is a typical rogue security application, Malware Protection expects you to believe that the name of Malware Protection's company is Malware Protection, which is downright ridiculous. Needless to say, the fake anti-virus application Malware Protection is nothing but a scam.
Table of Contents
How Malware Protection Runs its Scam, and What Symptoms You’ll See as a Result
The crooks behind Malware Protection are out to defraud people out of a maximal amount of money with a minimal amount of effort, so Malware Protection is just a clone of existing malware. The symptoms caused by Malware Protection are common for this type of scam. Basically, Malware Protection uses scare tactics to try to get you to pay for a nonexistent software license. In order to increase the likelihood that you'll give in, Malware Protection takes steps to prevent you from removing Malware Protection for as long as possible.
Fake system scans and security alerts are central to Malware Protection's way of trying to scare money out of the users of infected computers. Malware Protection will configure itself to run every time Windows is started, and every time Malware Protection runs, it will load a fake interface and run a fake scan. The interface is supposed to look realistic, and it is laid out to look like a window within Windows XP. However, the scans that are run from this interface are nothing more than animations, and the lists of results are false and pre-written. After each of these "scans," Malware Protection will tell you that the only way for you to protect your PC is to activate Malware Protection by paying a fee. In multiple locations on Malware Protection's interface and other screens, Malware Protection will refer to this as "Ultimate Protection," as if Malware Protection is a layer of protection on top of what would already be provided through Microsoft Security Essentials.
The fake security programs in Malware Protection's family,the FakeVimes family, are notorious for causing huge, unmanageable numbers of pop-up alerts. The alerts will claim that Malware Protection has found a bunch of threats, that someone is trying to steal your identity by targeting your "Microsoft Corporation keys" (whatever that's supposed to mean), and that there is malicious software on your computer. All of these phony alerts will urge you to scan your computer or to "register" Malware Protection, and if you click on the buttons provided, you will be taken to the payment page for Malware Protection. That assumes that you would be able to take the time to read any of the alerts, which might not be possible considering how fast the alert windows appear. Even if you try to close each new one as it pops-up, you may not be able to keep up with them all. It's like an especially nasty game of whack-a-mole.
Malware Protection will make a large number of changes to your computer's Registry and Internet Settings in order to prevent you from removing the malware or getting help online. Malware Protection will specifically tell Windows to prevent real anti-virus software from running, and Malware Protection will make other Registry changes so that Malware Protection runs every time that Windows starts. Malware Protection will also prevent you from viewing any website other than the Malware Protection payment site, which Malware Protection does by telling Windows that you are using a proxy server, thereby causing all of your Internet traffic to loop back to your own computer. Furthermore, while Malware Protection is active on your PC, you will be unable to run any other program, with the exception of your crippled web browser.
Where Does Malware Protection Come From?
Malware Protection installs itself secretly, using Trojans in order to find a way into the computers Malware Protection infects. That way, the user of an infected PC might be more likely to believe that Malware Protection is a preexisting Windows program that has some kind of advanced module that costs money. So, when you download the Trojan, you aren't aware of it, because it is hidden in some other file or disguised as something else. It is very common for the Trojan associated with Malware Protection to be disguised as a program update or video codec, or for it to be downloaded by a fake online virus scanner. Once the Trojan is on your machine, it drops the files for Malware Protection into the Application Data folder, to add to the illusion that Malware Protection is a legitimate program that behaves in an ordinary way. However, one of the files that the Trojan drops is nowhere near ordinary, because it is a .ini file. That file is what really tells your computer what to do, although you will not be able to see its contents. It is not usual for an everyday, consumer program to install a .ini file. In any case, once all of these changes have been made, Malware Protection will go active the next time you start Windows – and it will suddenly have shortcuts in every location where a program can have shortcuts.
Malware Protection began causing problems in late March 2011, but Malware Protection is from a family of rogue anti-virus applications that go back at least to 2009, if not 2008. Over time, these fake security programs have gone through some minor changes in appearance, but under the surface, they are essentially the same and they are created and propagated by the same people. Malware Protection is part of a vast Russian-operated Internet-based scam.
Other members of Malware Protection's malware family, which are part of this same scam, include Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst.

SpyHunter Detects & Remove Malware Protection
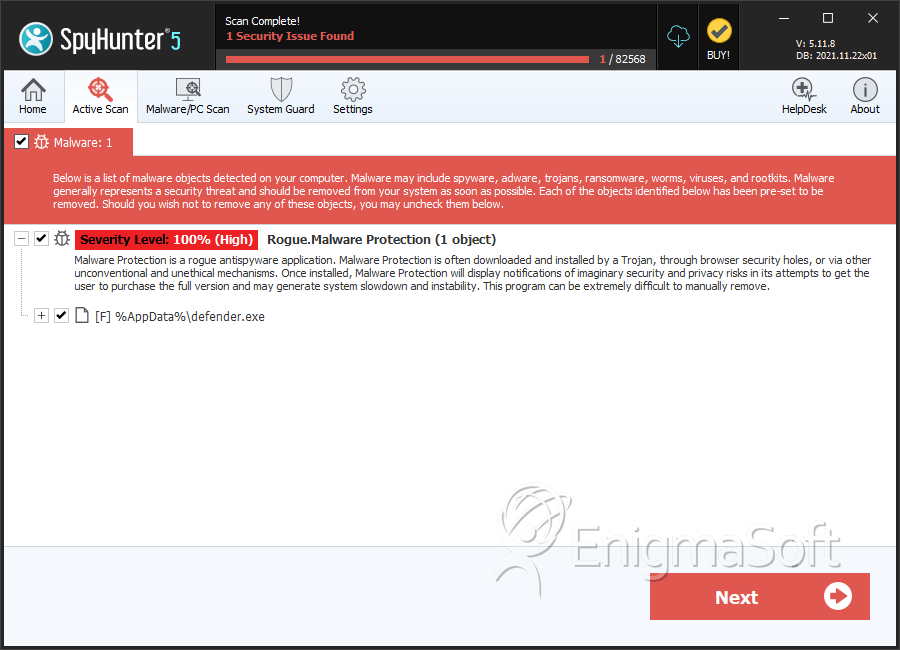
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | defender.exe | 63cc8941ba65952edf8ddab1a6809260 | 1 |

