Lisa Ransomware
The STOP/Djvu Ransomware's activity is still not dying down. This infamous file-locker has allowed dozens of cybercriminals to craft their personalized ransomware variant quickly – such as the Lisa Ransomware. This malware is able to encrypt a wide range of files such as images, archives, documents, media and many others. Just like original STOP/Djvu Ransomware variants, this one also appends a unique suffix to files it locks – '.lisa.' The malware also will create the ransom document '_readme.txt' on the desktop.
How is the Lisa Ransomware Spread?
This threat is likely to reach systems through fake downloads, pirated content or corrupted email attachments. The latter propagation method is certainly the most popular. The criminals approach victims through phishing emails, which urge them to download a fake document or archive that supposedly contains important details. Instead of the file they expect, victims will end up executing the threatening Lisa Ransomware payload.
The ransomware attack takes just a few minutes and renders the majority of the victim's files inaccessible. The '_readme.txt' ransom note tells users that they should not explore data recovery tools because this could cause more damage to their files. Instead, they advise them to buy a specialized decryptor for $490, paid via Bitcoin. However, trusting them is not an option. There is nothing to stop them from getting your money and leaving you empty-handed.
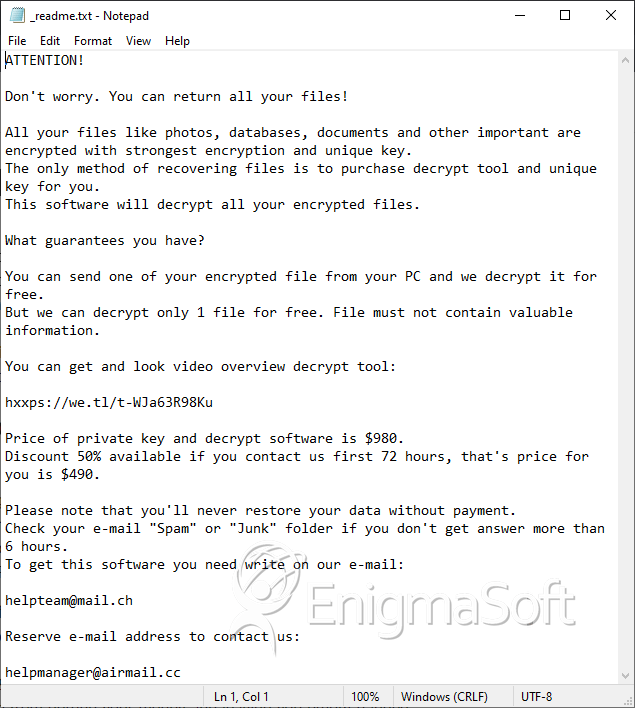
The document that the Lisa Ransomware drops, also advises users to send questions to manager@mailtemp.ch and supporthelp@airmail.cc. However, the only reason to contact the criminals is to take advantage of their offer to decrypt one file for free.
The best thing to do if the Lisa Ransomware has infiltrated your computer is to run a malware removal tool, and then try using alternative data recovery tools and techniques.