Windows No-Risk Center
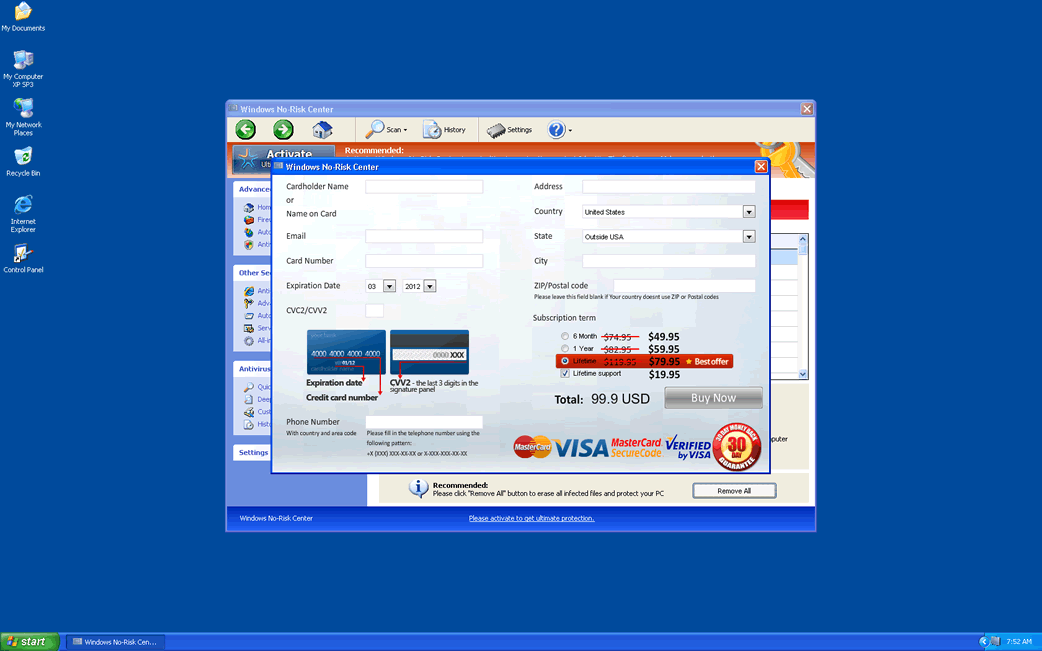
Windows No-Risk Center Image
Windows No-Risk Center is a fake security tool that belongs to the FakeVimes family of malware. Fake security programs in the FakeVimes family have been around since 2009 and are a typical example of the rogue anti-virus' scam. Windows No-Risk Center is part of a Trojan attack which will typically involve several malware threats working together to attack a computer system. Windows No-Risk Center is part of a batch of FakeVimes's clones released in 2012.
These include such malware as Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst.
Despite their different names, each of these programs is practically the same application with slight changes to the outward appearance in order to fool computer security researchers. All of these fake security applications are designed to try to convince inexperienced computer users that their computer system has become compromised due to a severe virus and Trojan infection. While the victim's computer actually is under attack – from Windows No-Risk Center itself – this fake security program detects a variety of malware threats taken straight out of a virus encyclopedia. With a constant stream of fake error messages, alarming pop-up notifications and other invasive tactics, Windows No-Risk Center does everything in its power to convince computer users that it is necessary to purchase a 'full version' of Windows No-Risk Center, so it will solve nonexistent malware infections on their computer.
Table of Contents
A Dangerous Rootkit Component may Accompany a Windows No-Risk Center Infection
FakeVimes and its clones usually do not pose a significant challenge to PC security researchers and most legitimate security programs. This is because this family of malware has remained practically unchanged since 2009. However, the recent batch of Windows No-Risk Center clones that includes Windows No-Risk Center has been known to include a ZeroAccess rootkit component. This makes Windows No-Risk Center particularly difficult to remove and detect, since ZeroAccess has the ability to hide the presence of other malware on the victim's computer, as well as disabling the most popular anti-malware programs on the market. Because of this, ESG security analysts recommend that removal of Windows No-Risk Center should include an anti-rootkit tool or an anti-malware program with anti-rootkit technology. It is also quite rare for a Windows No-Risk Center infection to appear without other malware infecting the victim's computer. Windows No-Risk Center will usually be associated with the aforementioned rootkit component, some kind of browser hijacker, and a dropper Trojan responsible for installing Windows No-Risk Center in the first place.





Windows No-Risk Center Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\NPSWF32.dll | |
| 2. | %AppData%\Protector-[RANDOM CHARACTERS].exe | |
| 3. | %CommonStartMenu%\Programs\Windows No-Risk Center.lnk | |
| 4. | %Desktop%\Windows No-Risk Center.lnk | |
| 5. | %AppData%\result.db |

