Are You Sure You’re NOT Infected with Malware?
Don’t Fall Victim to Malware or Ransomware Attacks!
Detect and remove malware, viruses, ransomware & other threats for FREE! Get Protected with SpyHunter.
Download SpyHunter (FREE Trial!)*A rogue anti-virus program is a type of computer parasite not unlike that of a Trojan horse virus. Rogue anti-virus programs are typically installed onto your computer system due to web-surfing activities and the acceptance of advertisements claiming that leaving the current website will leave a trace or bug infection that their product can remove.
Rogue anti-virus applications differ from Trojan viruses by utilizing scare tactics in order to intimidate you into purchasing their product. In the case that one has already been installed on your system, many infections are possibly installed along with it will not appear in any “Add or Remove Programs” menu.
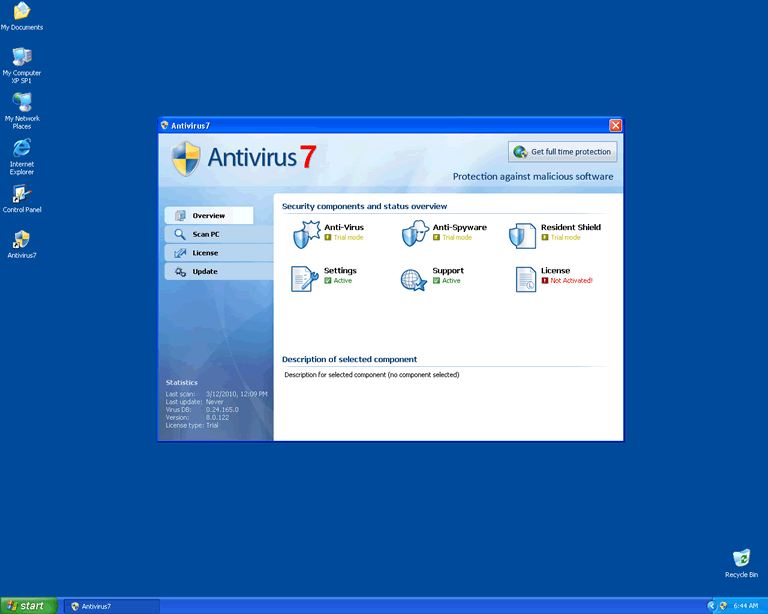
Example of a Rogue Anti-Virus program interface
The Internet landscape is peppered with distributors of rogue anti-virus programs, thus making it hard for PC users to distinguish between the good anti-virus programs and the bad or rogue anti-virus programs. So what makes a program rogue? A rogue computer program is any program that is dishonest and on the surface offers one thing but in actuality does another, especially something that is harmful.
Rogue anti-virus programs mimic the look and behaviors of legitimate anti-virus programs to fool unsuspecting PC users into trusting its offers. Rogues anti-virus programs offer to block or remove infections, when in fact they do the opposite. Rogue anti-virus programs stage a security breach and use fake alerts, scans, and reporting in hopes of scaring the victim into buying fraudulent software, much like rogue anti-spyware programs. However, while the victim eyes are busy absorbing the explosion on their screen (i.e. presentation of fake alerts, scans, and reporting), the rogue anti-virus program, courtesy of its engineer, a Trojan, wages an underlying attack.
Most rogue anti-virus programs are distributed as follows:
Most rogue anti-virus programs behave the same:
Hidden (happening in the background)
Visual (happening in the foreground)
The above is typical behavior of most rogue anti-virus programs. Unfortunately, buying the rogue anti-virus program will not end the nightmare. In fact, by entering your credit card information you will be helping a cybercriminal possibly ruin your financial future. Unless you like throwing away your money and turning your computer over to a hacker, you will need to remove the rogue anti-virus program and associated files or components. However, removal may be easier said than done. Trojans and other malicious programs are known to use rootkit technology to mask and bury malicious files from persons or tools hoping to remove it. So while manual removal is not impossible, it will be hampered by obfuscation tricks, i.e. polymorphic coding and rootkits.
Trojans are stealth and can make system changes comparable to that of an IT expert. One change will involve editing the registry and adding an auto run key that runs the malicious executable each time the operating system is booted. Another change, thanks to rootkit technology, involves masking file names so they read the same as legitimate operating system files. If you are not familiar with the operating system structure, you may not realize the malicious file is mapped incorrectly. However, if you delete the wrong file, you could corrupt your own hard drive and erase valuable data. Therefore, use of a professional antimalware solution containing an anti-rootkit component is highly recommended. A stealth antimalware solution can not only uproot hidden malware in the kernel or BIOS and remove without causing further harm, but too restored corrupted files, i.e. operating system files the Trojan hooked or injected with malicious code.
In order to keep malware at bay, it will be important to keep an antimalware solution in effect at all times, keep software updated and patched, and follow safety guidelines when using the Internet. Otherwise, if you are using Microsoft Windows, you can expect a repeat performance at next and every boot thereafter.
| # | Threat Name |
Severity Level
Severity Level: The determined severity level of an object, represented
numerically, based on our risk modeling process and research, as explained in our
Threat Assessment Criteria.
|
Alias(es) |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|---|
| 1. | Powerful PC Protection | |||
| 2. | Win 8 Defender 2013 | 20 % (Normal) | 1 | |
| 3. | Antivirus PC 2010 | |||
| 4. | XRJ Antivirus | 100 % (High) |
WindowsAntivirusPro Trojan.Win32.Generic.pak!cobra Suspicious file |
18 |
| 5. | Proven Antivirus | 20 % (Normal) | ||
| 6. | Win 7 Home Security 2013 | 20 % (Normal) | ||
| 7. | SFX Fake AV | 20 % (Normal) | 2,412 | |
| 8. | Windows Antivirus Master | 100 % (High) | 5 | |
| 9. | Win 7 2012 | 80 % (High) | 1 | |
| 10. | AV Security Essentials | 100 % (High) | 12 | |
| 11. | BitMefender | 10 % (Normal) | 4,717 | |
| 12. | Windows Protection Tool | 20 % (Normal) | 25,775 | |
| 13. | MS Recovery Tool | |||
| 14. | Win 8 Protection 2014 | |||
| 15. | Win 7 Antivirus 2014 | |||
| 16. | Win 7 Virus Protection | |||
| 17. | Microsoft Antivirus 2013 | 20 % (Normal) | ||
| 18. | Securebit Technologies | 100 % (High) | 4 | |
| 19. | Antivir Antispyware | |||
| 20. | Windows Daily Advisor | 20 % (Normal) | ||
| 21. | Win 8 Antivirus 2013 | 20 % (Normal) | ||
| 22. | AntivirSolution | |||
| 23. | Vista Antivirus 2010 | |||
| 24. | XP Antivirus Pro 2010 | |||
| 25. | Windows Processes Organizer | 100 % (High) | 2 | |
| 26. | Macro Virus | 100 % (High) | 7 | |
| 27. | Green Shield Antivirus | |||
| 28. | White Shark Virus | |||
| 29. | Best Antivirus 2011 | |||
| 30. | Windows Secure Kit 2011 | 20 % (Normal) | 14,734 |
Last updated: 2026-02-07
| Threat Name |
Severity Level
Severity Level: The determined severity level of an object, represented
numerically, based on our risk modeling process and research, as explained in our
Threat Assessment Criteria.
|
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 'Internet Security – designed to protect' Fake AV | 100 % (High) | 1,240 |
| A-Fast Antivirus | 100 % (High) | 13 |
| A-Secure 2015 | 100 % (High) | 0 |
| Activeris Antimalware | 10 % (Normal) | 5,486 |
| AKM Antivirus 2010 Pro | 100 % (High) | 22 |
| Albinos Defender | 20 % (Normal) | 0 |
| AlfaAntivirus | 100 % (High) | 10 |
| Anit-Virus Scanner | 20 % (Normal) | 68,679 |
| Anti Virus Armor | ||
| Antimalware - Proven Antivirus Protection | 20 % (Normal) | 0 |
| Antiprotect | ||
| Antivir 2010 | ||
| Antivir Antispyware | ||
| Antivir Pro | ||
| Antivir Solution Basic | ||
| Antivir Solution Plus | ||
| Antivirii 2011 | 100 % (High) | 11 |
| AntivirSolution | ||
| Antivirus 10 | 100 % (High) | 9 |
| Antivirus 2010 RTK | ||
| Antivirus 2010 Security Center | ||
| Antivirus 7 | 100 % (High) | 15 |
| Antivirus Action | 100 % (High) | 0 |
| Antivirus Antimalware 2011 | ||
| Antivirus Center | 100 % (High) | 355 |