Windows First-Class Protector
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 3,671 |
| Threat Level: | 20 % (Normal) |
| Infected Computers: | 8,701 |
| First Seen: | March 31, 2012 |
| Last Seen: | September 17, 2023 |
| OS(es) Affected: | Windows |
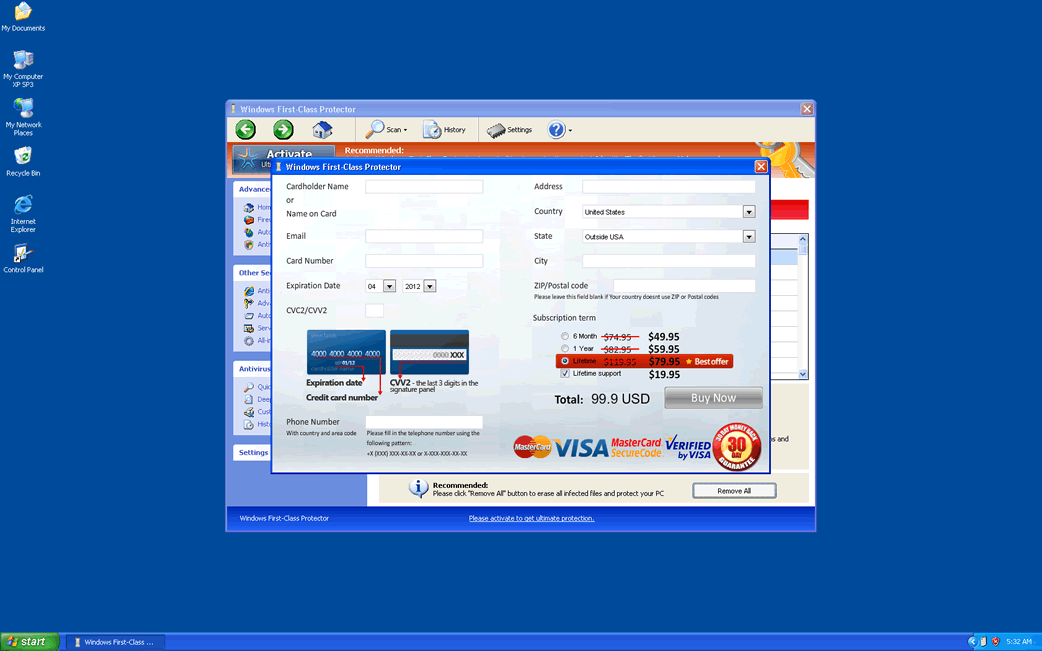
Windows First-Class Protector Image
If Windows First-class Protector is installed on your computer, you will need protection to get rid of this supposed protector! This is because Windows First-class Protector is not a real security program, but is, in reality, a type of malware infection named rogue anti-virus program. Rogue anti-virus programs are usually misleading applications that are installed as a result of a Trojan infection. These impersonate legitimate security programs in order to scam a computer user, convincing their victims to purchase useless, fake anti-virus software. There are dozens of versions of the Windows First-class Protector, known as clones. Criminals make these in order to make the task of PC security analysts more difficult, as keeping track of multiple versions of a threat is exponentially more difficult than dealing with a single malware application.
Some examples of Windows First-class Protector clones include fake security programs named Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst.
Like most rogue security programs in the FakeVimes family of rogue security software, Windows First-class Protector uses files names that contain a three-letter string made up of three random letters. These are usually preceded with the string 'protector-', which is a characteristic of a large batch of FakeVimes rogue security programs released in 2012.
Table of Contents
Dealing with a Windows First-Class Protector Attack
It is crucial to understand when dealing with a Windows First-class Protector infection, that this program is part of a scam. Windows First-class Protector makes alarming claims which can cause inexperienced computer users to panic. However, these are all lies. The next thing to understand about Windows First-class Protector is that its main objective is to get you to purchase a fake 'full version' of Windows First-class Protector. After all, the ultimate goal of any malware infection is to profit in some way from harassing computer users. Because of this, you should beware of paying any amount for Windows First-class Protector or disclosing your credit card information, regardless of how annoying the constant error messages and browser redirects become. FakeVimes rogue security programs have been around for several years, so most reliable (and, of course, real) anti-malware programs should be able to deal with Windows First-class Protector. However, members of the batch of FakeVimes clones released in 2012 are often coupled with a ZeroAccess rootkit infection, which can make removal of Windows First-class Protector more problematic. Fortunately, using a specialized anti-rootkit tool or an anti-malware program with anti-rootkit feature you should be capable to handle this problem.


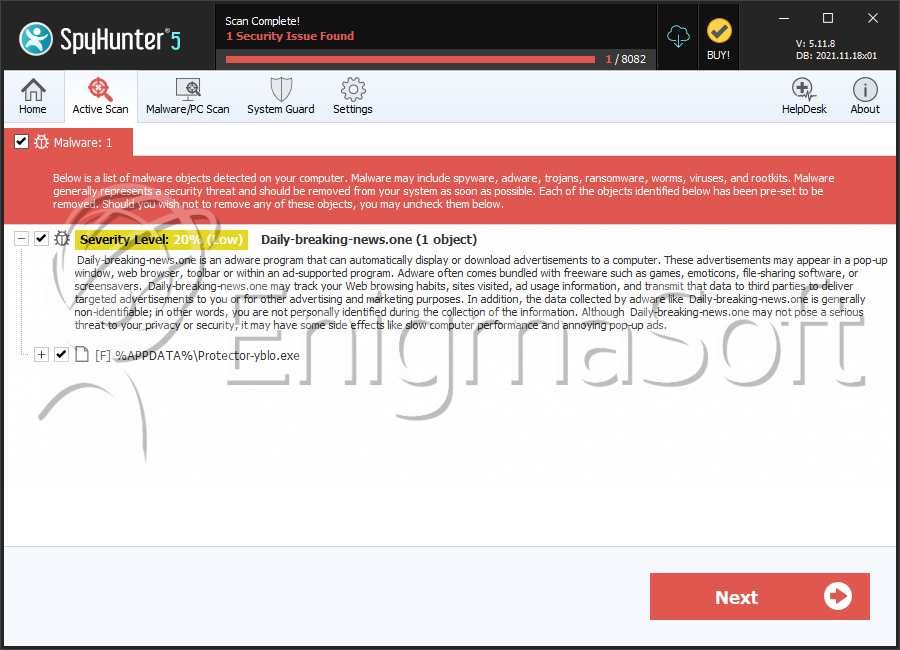
SpyHunter Detects & Remove Windows First-Class Protector
Windows First-Class Protector Video
Tip: Turn your sound ON and watch the video in Full Screen mode.

File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | %AppData%Protector-[RANDOM 3 CHARACTERS].exe | ||
| 2. | %AppData%NPSWF32.dll | ||
| 3. | %StartMenu%ProgramsWindows First-Class Protector.lnk | ||
| 4. | %Desktop%Windows First-Class Protector.lnk | ||
| 5. | %AppData%\result.db | ||
| 6. | Protector-yblo.exe | 3b5d18ed6417b4d7b729dee0a7944449 | 0 |
Registry Details
URLs
Windows First-Class Protector may call the following URLs:
| daily-breaking-news.one |

