Windows Antivirus Rampart
Windows Antivirus Rampart Image
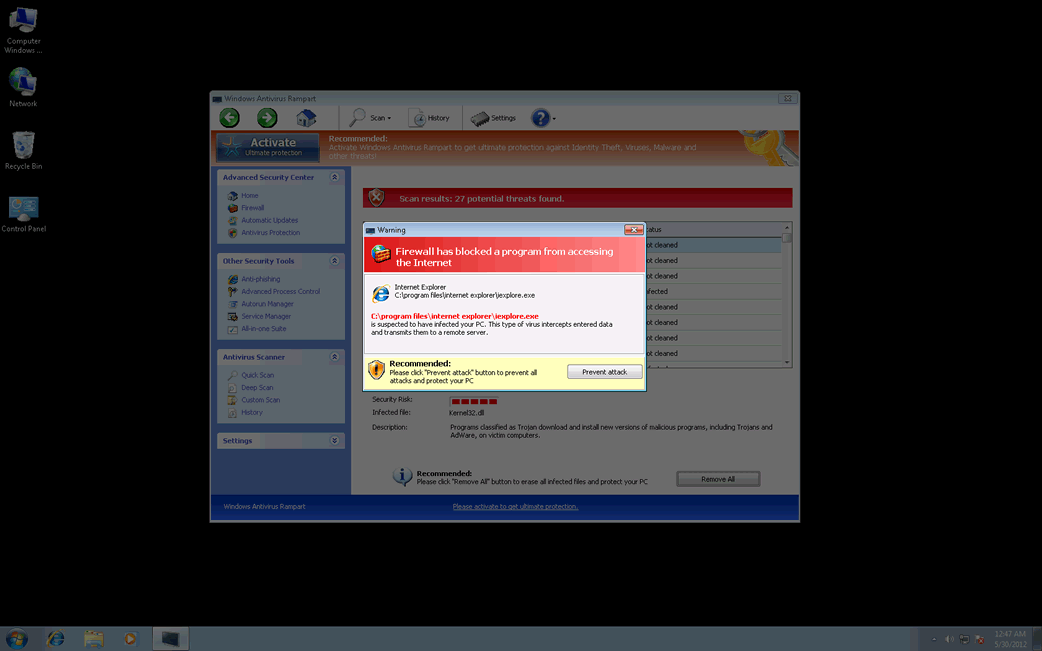
Windows Antivirus Rampart is one of the many fake security applications in the FakeVimes family of rogue security programs. Such malware infections mimic legitimate security programs while not having any legitimate anti-malware capabilities. Rather, Windows Antivirus Rampart and its clones are designed to carry out a scam consisting in convincing computer users that they need to purchase useless, bogus security programs. With this in mind, ESG malware analysts highly advise removing Windows Antivirus Rampart immediately with a real anti-malware application.
Table of Contents
Windows Antivirus Rampart’s Large Family of Rogue Security Programs
Windows Antivirus Rampart's family of malware has been active since 2009, which means that most legitimate security programs can deal easily with FakeVimes fake security programs. Unfortunately, ESG malware researchers have detected that malware in the FakeVimes family released in 2012 will often be accompanied with a ZeroAccess rootkit infection. This associated malware infection makes this newest generation of malware in the FakeVimes family considerably more difficult to remove. Other examples of fake security software in the FakeVimes family of malware also released in 2012 and previous years include Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst.
To steal your money, Windows Antivirus Rampart will try to persuade you that your PC is dangerously infected with malware. To do this Windows Antivirus Rampart uses numerous bogus error messages, both in the form of pop-up notifications and system alerts from the Task Bar. All of these messages will claim that your computer system is under attack or vulnerable in various ways. However, trying to use Windows Antivirus Rampart to remove these supposed malware problems results in more error messages claiming that you need to purchase a 'complete version' of Windows Antivirus Rampart to be able to deal with these nonexistent malware problems. Since Windows Antivirus Rampart has no real anti-malware capabilities, ESG security analysts strongly advise against purchasing this bogus security program.
Dealing with a Windows Antivirus Rampart Infection
Instead of paying for Windows Antivirus Rampart's 'full version', it is important to remove this fake security program with the help of an anti-malware application with anti-rootkit technology. However, it is not necessary to purchase Windows Antivirus Rampart in order to obtain a serial number. The registration code 0W000-000B0-00T00-E0020 can be used to 'unlock' Windows Antivirus Rampart. While this will not remove Windows Antivirus Rampart (it still needs to be removed with a reliable anti-malware tool), entering that registration number can help stop most of Windows Antivirus Rampart's irritating error messages.
Windows Antivirus Rampart Video
Tip: Turn your sound ON and watch the video in Full Screen mode.

File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\Protector-[RANDOM 4 CHARACTERS].exe | |
| 2. | %AppData%\Protector-[RANDOM 3 CHARACTERS].exe | |
| 3. | %AppData%\NPSWF32.dll | |
| 4. | %CommonStartMenu%\Programs\Windows Antivirus Rampart.lnk | |
| 5. | %AppData%\result.db | |
| 6. | %AppData%\1st$0l3th1s.cnf | |
| 7. | %Desktop%\Windows Antivirus Rampart.lnk |

