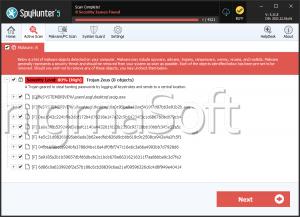
Zeus Trojan
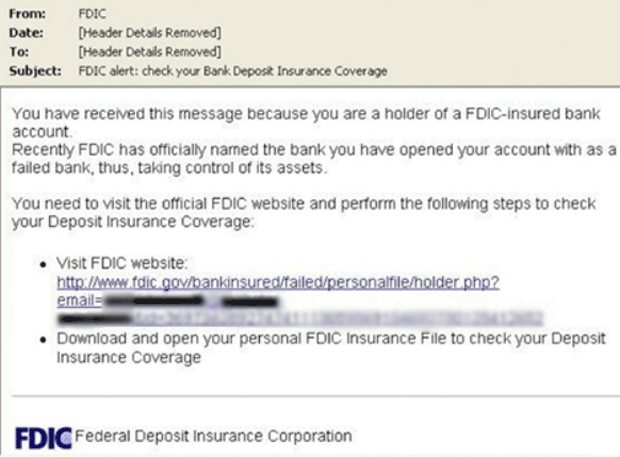
Zeus Trojan Image
The Zeus Trojan is the most widespread and common banking Trojan today. There are countless variants of the Zeus Trojan, also known as Zbot and Zitmo. There are regional variants that target computers in specific areas of the world as well as mobile-specific variants designed to attack mobile operating systems such as Android or BlackBerry platforms. In all cases, the Zeus Trojan is used to steal banking information. This dangerous malware infection can be used to steal account names and numbers, banking account passwords, and credit card numbers. The Zeus Trojan can also be utilized to capture particular information that can then be used to steal a victim's identity. ESG security researchers consider that the Zeus Trojan and its many variants are severe threats to a computer and to your security. Protect yourself by using reliable anti-malware software and keeping it constantly updated.
Table of Contents
Understanding the Zeus Trojan Infection
In its most basic form, the Zeus Trojan steals banking information and then sends this information to a remote host. Formerly, the Zeus Trojan was linked to a very large botnet. Although there are still very large botnets associated with the Zeus Trojan, these have diminished in size in the last few years. The most common tactic to distribute the Zeus Trojan is through malicious email messages which are often sent out by these very same botnets. Zeus Trojan infections spread through phishing email messages as well as social media scams. Often, the Zeus Trojan will be used in conjunction with the Black Hole Exploit Kit. Using this dangerous utility, criminals can set up attack websites that then infect a computer with the Zeus Trojan.
Dealing with a Zeus Trojan Infection
The main danger of a Zeus Trojan infection is that a computer user will rarely be aware of the presence of this threat. The Zeus Trojan and most of its variants are designed to reside on the victim's computer without causing overt symptoms. Apart from a slight increase in system resource usage, computer users will probably not notice the presence of a Zeus Trojan infection. This is why it is so important to update your security software. In most cases, the first sign of a Zeus Trojan infection will be its detection by an anti-virus application. To prevent a Zeus Trojan infection in the future, ESG malware analysts recommend never downloading unsolicited email attachments or clicking on embedded links contained in unsolicited email messages.
Even though variations of Zeus were originally sold on the dark web as a malware kit worth thousands of dollars, eventually the Zeus Trojan had its source code releases to the public in 2011 and that led to a number of recompiles and tweaks of the codebase, distributed as new threats by various bad actors. Those include the Terdot Trojan and Gameover, to name a couple. Gameover was upgraded to use encryption for all communication between infected systems and the command and control servers, which made fighting it more difficult. According to reports from around the time Zeus was open-sourced, the price to obtain a pre-made Zeus package as someone not familiar with coding was between two and ten thousand dollars, depending on the number of extra modules included in the package.
To counter the spread of the Zeus Trojan, a non-profit service tracking Zeus-related domains and URLs was established at zeustracker.abuse.ch. The service was discontinued in early July 2019. Still, computer users who may encounter Zeus will want to utilize the proper resources to safely detect and eliminate Zeus without hesitation to prevent system damages or theft of personal data.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | 088709.exe | |
| 2. | C:\WINDOWS\System32\ntos.exe | |
| 3. | C:\WINDOWS\System32\sdra64.exe | |
| 4. | C:\WINDOWS\System32\oembios.exe | |
| 5. | C:\WINDOWS\System32\sysproc64\sysproc86.sys | |
| 6. | C:\WINDOWS\System32\sysproc64\sysproc32.sys | |
| 7. | C:\WINDOWS\System32\wsnpoem\video.dll | |
| 8. | C:\WINDOWS\System32\wsnpoem\audio.dll | |
| 9. | C:\WINDOWS\System32\twext.exe | |
| 10. | C:\WINDOWS\System32\twain_32\local.ds | |
| 11. | C:\WINDOWS\System32\twain_32\user.ds | |
| 12. | C:\WINDOWS\System32\lowsec\user.ds | |
| 13. | C:\WINDOWS\System32\lowsec\local.ds |