Windows Safety Toolkit
Windows Safety Toolkit Image
ESG security analysts have observed that a large batch of FakeVimes rogue anti-virus software has been causing trouble since January of 2012. Windows Safety Toolkit is one of the many fake security programs belonging to this particular release of rogue security programs in the FakeVimes family. This specific family of malware has been around for several years, at least since 2009. Even though PC security researchers know enough about Windows Safety Toolkit and its clones to remove them without too much trouble, this latest batch of FakeVimes programs will often include a rootkit component (usually in the ZeroAccess or Sirefef family) which can make removal of Windows Safety Toolkit much more difficult than normal.
Like most FakeVimes programs, Windows Safety Toolkit uses file names that contain three random letters, often preceded with a short string that can vary from one clone to another. Windows Safety Toolkit can detect legitimate anti-malware software running on the victim's computer system and can take steps to disable it. Windows Safety Toolkit has many clones, including Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst. Removal of Windows Safety Toolkit should include the use of an anti-rootkit tool in order to stop this fake security program's associated rootkit.
Table of Contents
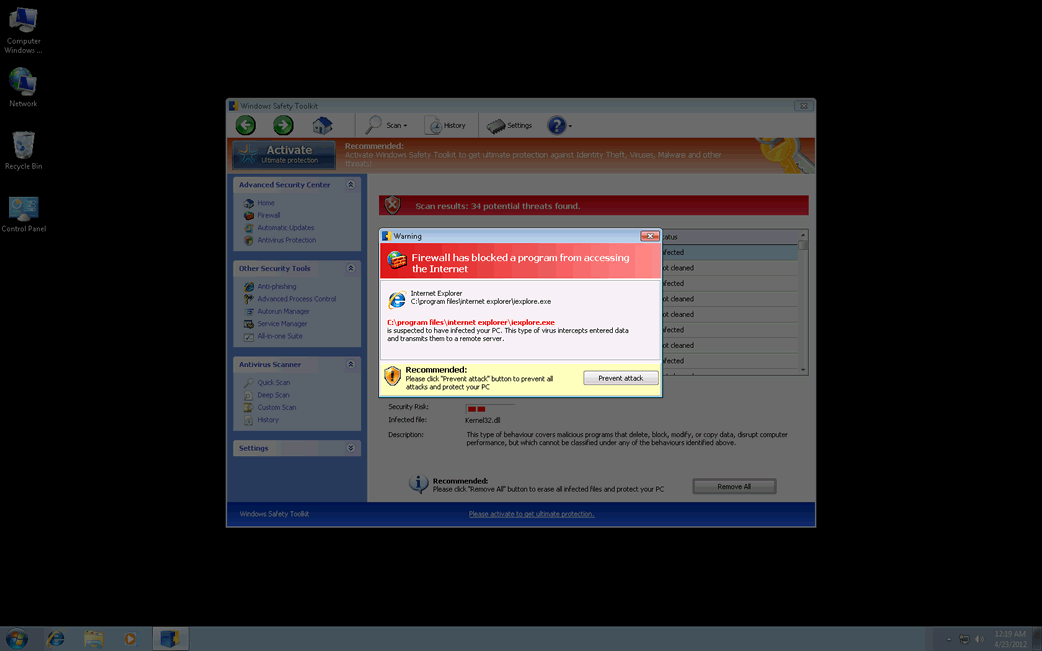
Dealing With the Windows Safety Toolkit Scam
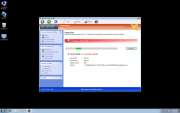
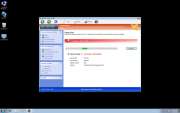
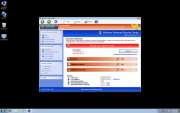
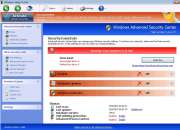
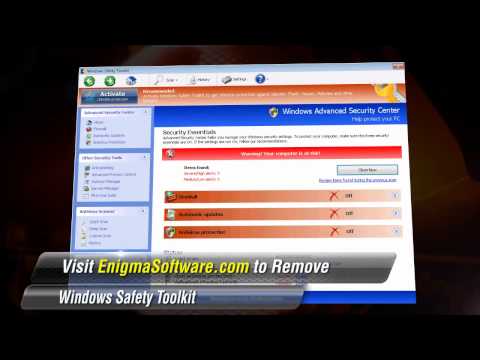
The Windows Safety Toolkit scam is not too sophisticated. Like most rogue anti-virus programs, Windows Safety Toolkit uses misleading error messages in order to make its victims believe that their computer system is under attack from a horde of viruses and Trojans. Then, Windows Safety Toolkit uses browser redirects and security notifications in order to recommend that the victim purchase a "full version" of Windows Safety Toolkit in order to fix these imaginary problems.
Windows Safety Toolkit will demand that the victim enter a registration code in order to supposedly "solve" these problems. However, this is impossible when one considers that Windows Safety Toolkit has no actual anti-virus capabilities. What this registration code will do is cause Windows Safety Toolkit to stop displaying misleading error messages. You should use the code 0W000-000B0-00T00-E0020, which can be used to stop some of Windows Safety Toolkit's most annoying characteristics. However, this code will not remove Windows Safety Toolkit from an infected computer system, and many of the problems Windows Safety Toolkit causes will remain until Windows Safety Toolkit is removed with a reliable anti-malware program.



Windows Safety Toolkit Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\Protector-[RANDOM 3 CHARACTERS].exe | |
| 2. | %AppData%\NPSWF32.dll | |
| 3. | %Desktop%\Windows Safety Toolkit.lnk | |
| 4. | %AppData%\W34r34mt5h21ef.dat | |
| 5. | %AppData%\result.db | |
| 6. | %CommonStartMenu%\Programs\Windows Safety Toolkit.lnk |

