Windows Safety Module
Windows Safety Module Image
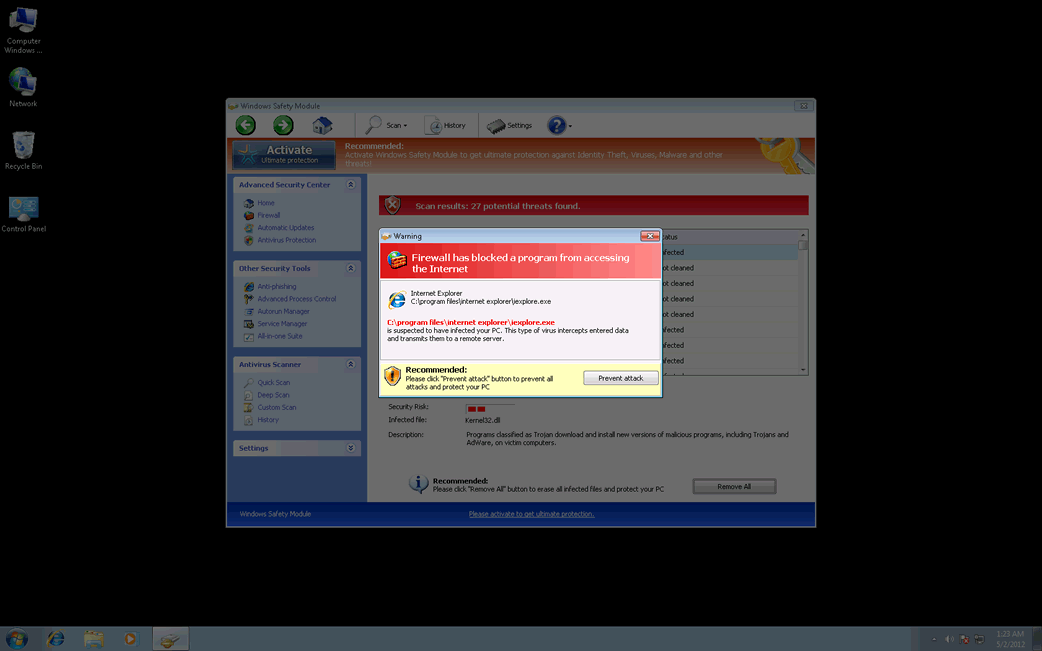
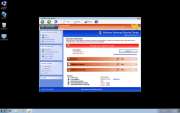
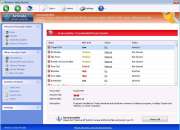
Although Windows Safety Module claims that Windows Safety Module can keep a computer system free from malware, this is hard to believe, considering that Windows Safety Module is part of a multi-component malware attack itself. Windows Safety Module in particular is installed by a Trojan infection, uses a variety of Trojans in order to attack a computer system, and is often accompanied by a rootkit infection that can be quite difficult to remove. Windows Safety Module belongs to a category of malware known as fake antispyware programs, a kind of scareware designed to make computer users purchase useless security software. Windows Safety Module is one of the dozens of members of the FakeVimes family of rogue anti-virus programs.
ESG security researchers are well acquainted with the FakeVimes family of malware; FakeVimes rograms have been infecting computer systems since 2009. Because of this, most cases of infection with malware in this family are not too difficult to remove. However, ESG malware analysts have observed that FakeVimes programs released in 2012 tend to include an integrated ZeroAccess (also known as Sirefef) rootkit component. This rootkit makes removal of its components quite difficult since it creates a hidden file system that can hide the presence of malware on the victim's computer system. It also gives Windows Safety Module the capacity to disable known security software.
Table of Contents
Preventing a Windows Safety Module Attack
There are many clones of Windows Safety Module, that is, various versions of the same malware infection with different names. These are used to throw PC security researchers off, making it necessary for malware analysts to have to keep up with new releases in order to dispense new cures for infected computer system. Examples of clones of Windows Safety Module include programs with names like Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst.
Despite their different names, all of these programs carry out the same scam. Basically, they scare computer users into paying for a fake "upgrade" for Windows Safety Module by displaying misleading error messages and false positives for severe malware infections on the victim's computer system. ESG malware analysts strongly advise against paying for Windows Safety Module. Instead, a reliable anti-malware program with anti-rootkit technology should be used to scan the infected computer system. You can enter the registration code 0W000-000B0-00T00-E0020 as a way to make many of Windows Safety Module's irritating error messages stop (keep in mind that this will not remove Windows Safety Module, but only stop its most annoying symptoms; removal with a reliable anti-malware program is still strongly recommended).



Windows Safety Module Video
Tip: Turn your sound ON and watch the video in Full Screen mode.

File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\NPSWF32.dll | |
| 2. | %AppData%\Protector-[RANDOM CHARACTERS].exe | |
| 3. | %AppData%\result.db |

