Windows Risk Minimizer
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | March 13, 2012 |
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
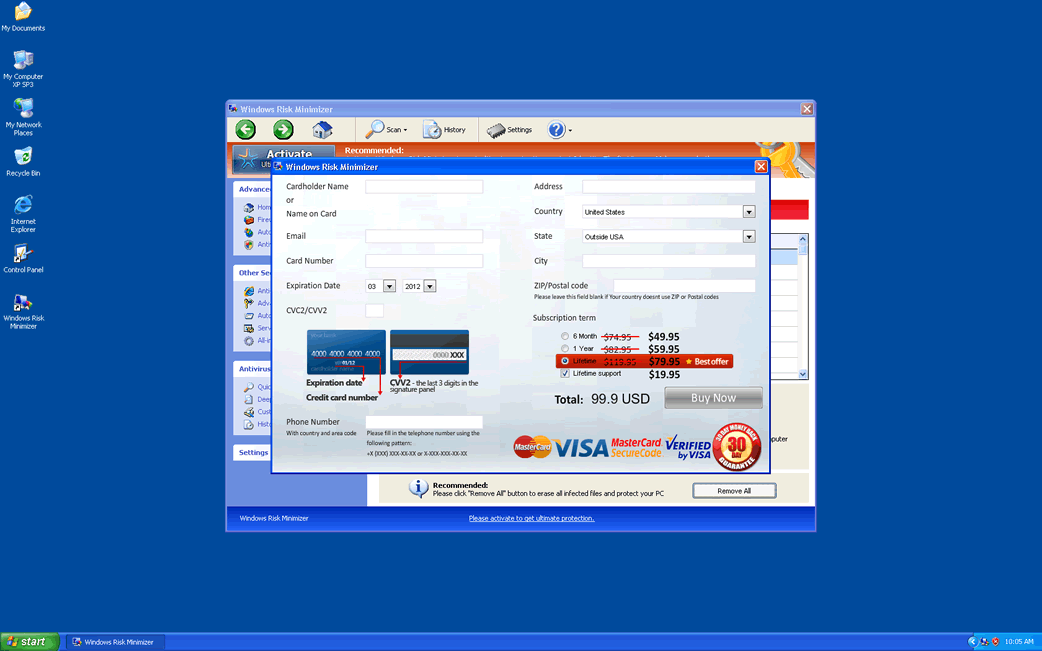
Windows Risk Minimizer Image
Windows Risk Minimizer belongs to the FakeVimes family of rogue security programs. Windows Risk Minimizer belongs to a recent batch of clones of the FakeVimes family, a family of rogue security programs that started its activities back to 2009. Windows Risk Minimizer and its clones attempt to scam computer users by inducing them to believe that their PCs are infected with malware and then convincing them to purchase bogus security programs.
Some members of the FakeVimes family of rogue security programs include Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst.
However, the batch that includes Windows Risk Minimizer is particularly malicious because Windows Risk Minimizer tends to be accompanied by a ZeroAccess rootkit infection, a malware infection designed to prevent removal and detection of Windows Risk Minimizer that is quite difficult to remove. In fact, Windows Risk Minimizer will usually require a specialized rootkit removal tool in order to be cleaned out effectively. Windows Risk Minimizer itself, however, is not particularly difficult to remove. Since PC security researchers have been keeping tabs on the FakeVimes family and its clones for several years, dealing with this malware threat should be within the reach of any competent security application. Members of the FakeVimes family of malware tend to use executable files with names composed of three random letters. This recent batch of clones tends to use executable files named 'protector-xxx', where xxx are three random letters, with an EXE extension.
Table of Contents
Despite Its Age, the Windows Risk Minimizer Scam is Essentially the Same
Although there are slight differences in the interface and names between Windows Risk Minimizer and its many clones, the way Windows Risk Minimizer carries its attack is basically unchanged from versions of this malware threat dating back to 2009. The attack is simple: first, Windows Risk Minimizer makes the necessary changes to the Windows Registry and system settings that allow Windows Risk Minimizer to display error messages that appear authentic as well as starting up automatically whenever the victim starts up Windows. Then, Windows Risk Minimizer will display intrusive bogus error messages and a fake system scan and report claiming the presence of numerous malware threats. Finally, Windows Risk Minimizer will claim that the only way to remove these nonexistent threats is by paying for a license to use Windows Risk Minimizer in its fake 'full version.' Since Windows Risk Minimizer is malware itself, Windows Risk Minimizer should instead be removed with a reliable anti-malware program.



SpyHunter Detects & Remove Windows Risk Minimizer
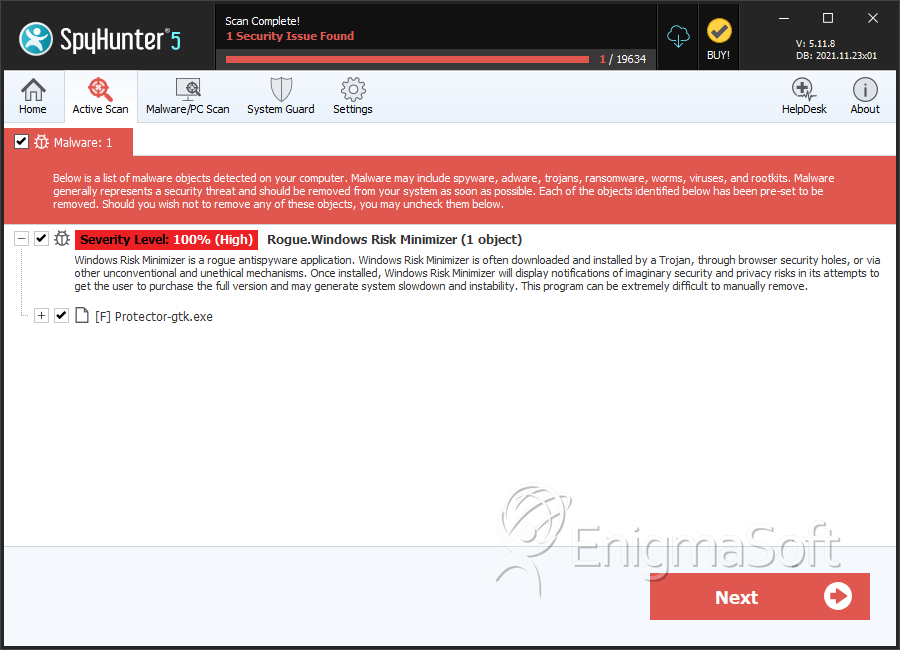
Windows Risk Minimizer Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Protector-gtk.exe | 1a30a36401f4374a5a464ff58bca3ef0 | 1 |
| 2. | %AppData%\Inspector-[RANDOM CHARACTERS].exe | ||
| 3. | %AppData%\npswf32.dll | ||
| 4. | %CommonPrograms%\Windows Risk Minimizer.lnk | ||
| 5. | %DesktopDir%\Windows Risk Minimizer.lnk |

