Windows Pro Safety
Windows Pro Safety Image
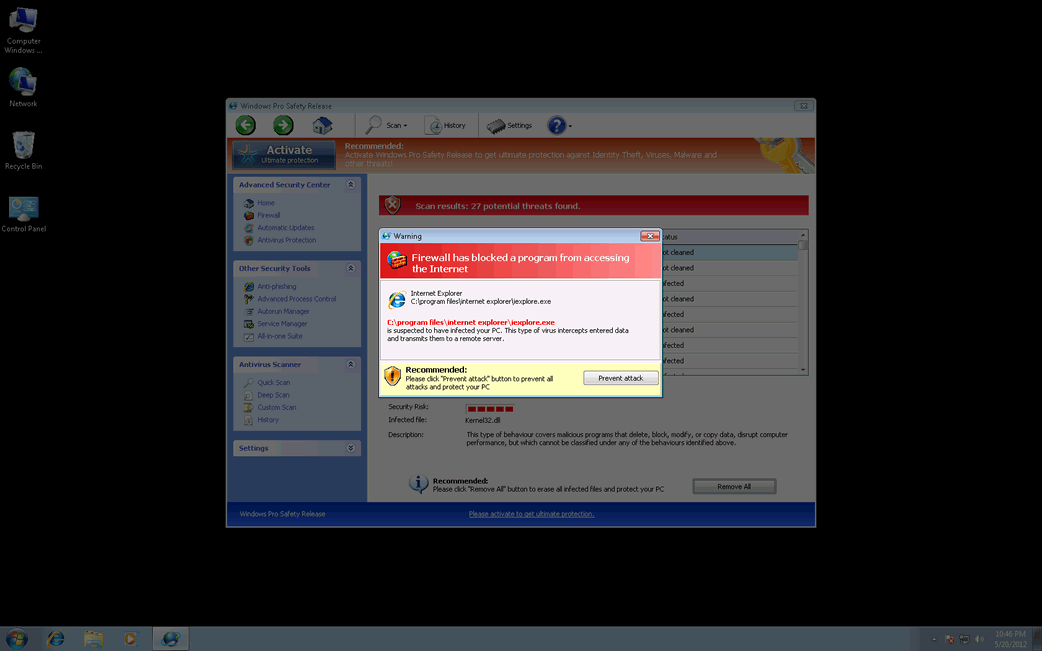
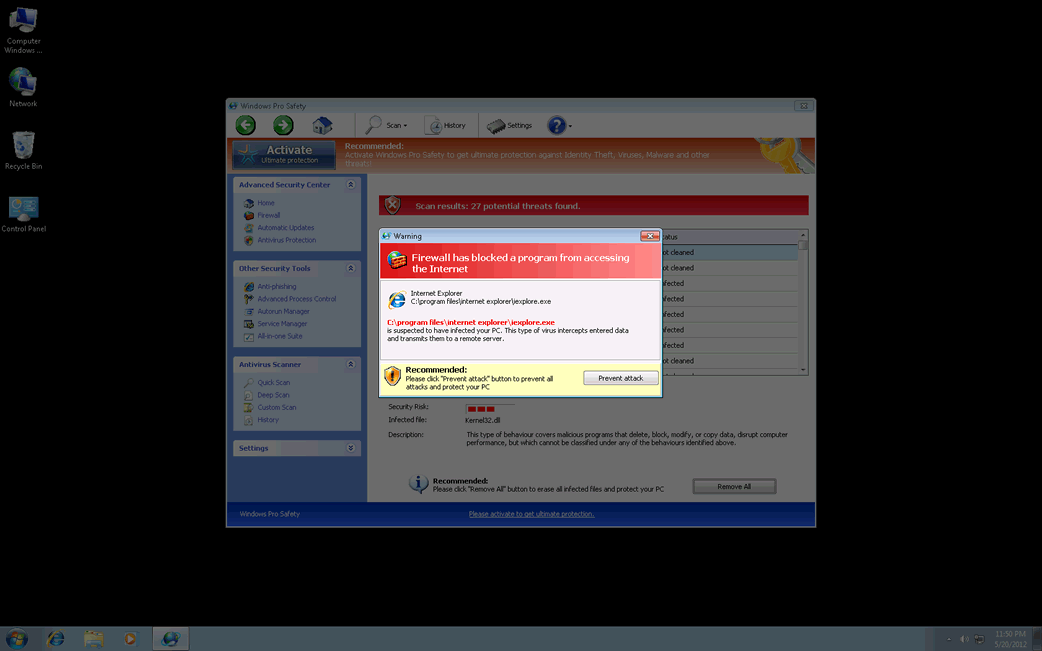
Windows Pro Safety belongs to a category of malware programs known as rogue security applications. Rogue security programs like Windows Pro Safety pretend to be legitimate anti-malware programs but have no actual anti-malware capabilities. These kinds of fake security applications are used as part of a pervasive online scam that preys on inexperienced computer users. Basically, criminals make the victims believe that their computer system is severely infested with all kinds of malware. However, trying to use Windows Pro Safety to fix these simply results in a message claiming that the victim needs to 'upgrade' to an also useless 'full version' of Windows Pro Safety. This supposed upgrade is not cheap, usually close to one hundred dollars. ESG security analysts strongly advise against purchasing Windows Pro Safety. Instead, this fake security application should be dealt with using a reliable anti-spyware program.
Table of Contents
Windows Pro Safety, Rootkits and the FakeVimes Family of Malware
Windows Pro Safety belongs to a particularly large group of fake security software known as the FakeVimes family of malware. Because these bogus security applications have been active since 2009, most legitimate anti-malware programs are well equipped to deal with them. However, malware in the FakeVimes family released in 2012 will often include an accompanying rootkit infection (often a version of the Sirefef rootkit) that makes them much more difficult to remove than previous versions of FakeVimes malware applications. Some examples of clones of Windows Pro Safety released in 2012 and before include Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst. The presence of the rootkit component makes these newer versions of FakeVimes clones much more difficult to remove than their predecessors and will often require the help of a specialized anti-rootkit tool or a strong anti-malware program with anti-rootkit technology.
How You Can Protect Your Computer System from the Windows Pro Safety Scam
The culprit behind most rogue security software infections is usually a Trojan. Trojans associated with Windows Pro Safety will often enter a computer system disguised as a fake video codec, a harmless email attachment, or as a result of an exploit on an attack website. The most common causes for Trojan infections associated with Windows Pro Safety are online advertisements claiming to scan your computer system for malware. They will always claim that your computer is infected and urge you to install Windows Pro Safety. Almost all of these kinds of malicious advertisements will also attempt to exploit known vulnerabilities in order to install Windows Pro Safety in the background while the fake scan is distracting the computer user.
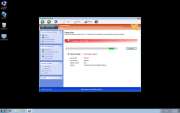
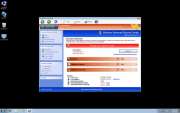



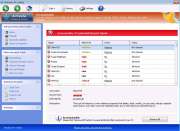
Windows Pro Safety Video
Tip: Turn your sound ON and watch the video in Full Screen mode.

File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\Protector-[RANDOM 4 CHARACTERS].exe | |
| 2. | %AppData%\Protector-[RANDOM 3 CHARACTERS].exe | |
| 3. | %AppData%\NPSWF32.dll | |
| 4. | %CommonStartMenu%\Programs\Windows Pro Safety.lnk | |
| 5. | %Desktop%\Windows Pro Safety.lnk | |
| 6. | %AppData%\result.db |