Windows High-End Protection
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 3,182 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 4,336 |
| First Seen: | April 30, 2012 |
| Last Seen: | September 19, 2023 |
| OS(es) Affected: | Windows |
Windows High-End Protection Image
Table of Contents
Windows High-End Protection Does Not Offer Any Protection for Your Computer System
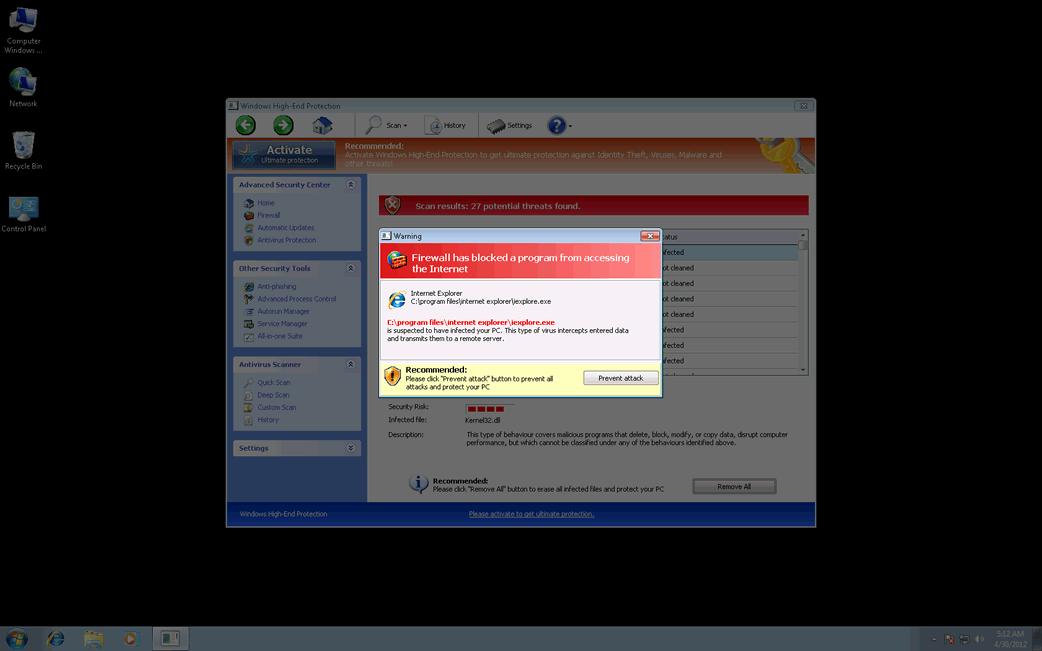
Windows High-End Protection is a bogus anti-virus program that is part of a recognized online scam. Basically, Windows High-End Protection pretends to be a legitimate security application despite not having any anti-virus or anti-malware capabilities. The main goal of the Windows High-End Protection scam is to convince computer users to purchase useless, fake security programs. These kinds of malware infections as known as rogue anti-virus or rogue anti-malware programs. Windows High-End Protection belongs to a common family of rogue security programs known as FakeVimes.
FakeVimes bogus security programs have been active for several years. ESG malware analysts have been tracking the activities of fake security software in the FakeVimes family since 2009. Because of this, dealing with a Windows High-End Protection infection is not particularly difficult for most security programs. However, Windows High-End Protection belongs to a group of FakeVimes anti-viruses released in 2012 that often include an associated rootkit that is installed along with the rogue security program. The presence of this rootkit component, often some version of the ZeroAccess rootkit, greatly complicates removal of Windows High-End Protection and its clones.
There are numerous malicious programs like Windows High-End Protection, including such rogue anti-virus applications as Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst.
Do Not Become a Victim of the Windows High-End Protection Scam!
Malware like Windows High-End Protection is often known as scareware because of its main tactic: scaring its victims. Windows High-End Protection is designed to display numerous error messages and bogus security warnings in order to make its victims panic, scaring them into believing that their computer system has been attacked by several viruses and Trojans. Then, Windows High-End Protection will offer to fix these nonexistent problems provided that the victim is willing to spend money on a "full version" of Windows High-End Protection. Of course, since Windows High-End Protection has no real anti-virus capabilities, paying for its "full version" is not a good idea.
You can trick Windows High-End Protection into thinking that you have paid for its "full version" by entering the registration code the 0W000-000B0-00T00-E0020. ESG malware analysts have identified this registration code as an effective way to stop Windows High-End Protection from displaying its alarming error messages. However, this registration code will not remove Windows High-End Protection from your computer system. To remove Windows High-End Protection completely, it is recommended to use a reliable, fully up to date anti-malware application.
Windows High-End Protection Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\NPSWF32.dll | |
| 2. | %AppData%\Protector-[RANDOM CHARACTERS].exe | |
| 3. | %AppData%\result.db |

