Windows Defence Counsel
Windows Defence Counsel Image
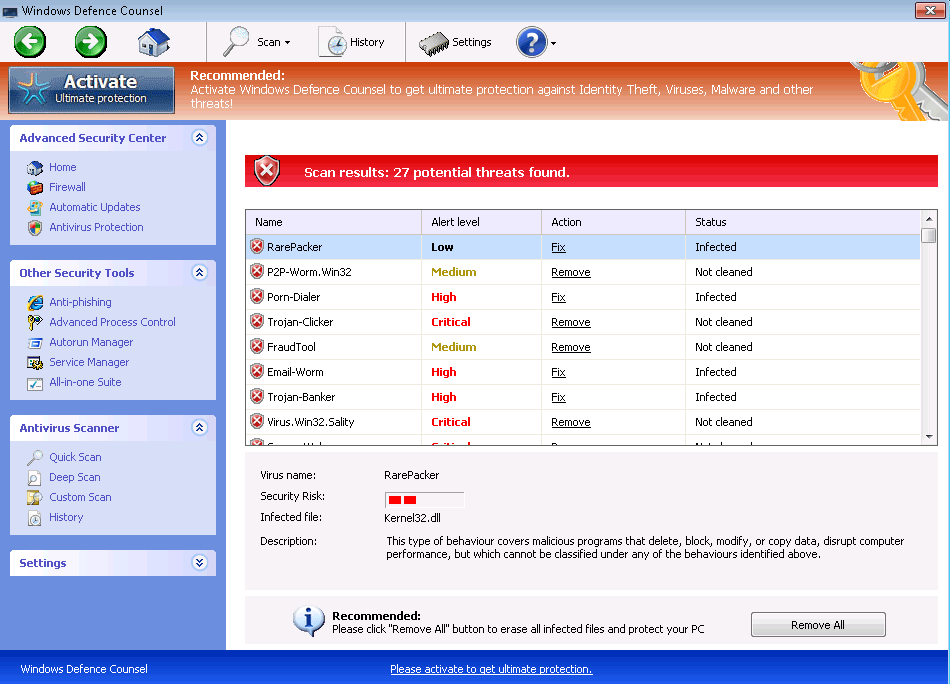
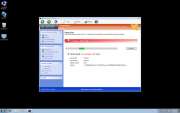
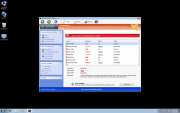
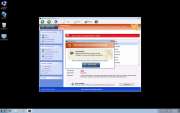
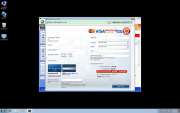
Windows Defence Counsel is one of the many fake security programs in the FakeVimes family of malware. Malware such as Windows Defence Counsel is referred to as rogue security software. Rogue security programs like Windows Defence Counsel try to carry out an online scam which consists in trying to convince the victims that it is necessary for them to purchase a useless 'full version' of its fake security program. To do this, Windows Defence Counsel will try to convince the victims that their computer is severely infected with malware. While this is technically true, what Windows Defence Counsel fails to tell you is that the severe malware infection is actually Windows Defence Counsel itself!
Table of Contents
Understanding a Scamware Like Windows Defence Counsel
The scam that Windows Defence Counsel carries out is among the most common kinds of online scams. There are thousands of programs similar to Windows Defence Counsel. The severity of the malware attack varies from one fake security program to another. While some of these fake security programs will simply pretend to be legitimate security programs and pester their victims with fake error messages, some of the more malicious kinds of rogue security programs will actually change your computer's settings and employ a variety of Trojan and rootkit components in order to completely take over the victim's computer. Unfortunately, Windows Defence Counsel belongs to the second kind; ESG team of PC security researchers has observed that Windows Defence Counsel may cause browser redirects, a computer to become slow or unstable, and make dangerous changes to the infected computer's settings and registry.
Windows Defence Counsel and the FakeVimes Family of Malware
The FakeVimes family of malware has been active since 2009. Windows Defence Counsel belongs to a variety of malware in the FakeVimes family that was first seen in late 2011 and that has been very active in 2012. Examples of these fake security programs include Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst.
The main danger that these variants of the FakeVimes family of malware pose is that they will often use the ZeroAccess rootkit in order to hide from detection. Because of this, ESG team of PC security analysts recommends using an anti-rootkit tool before trying to remove a Windows Defence Counsel infection. You cant trick Windows Defence Counsel into thinking that you have paid the registration fee with the code 0W000-000B0-00T00-E0020. This code will not remove Windows Defence Counsel, but will stop its most annoying symptoms while you seek a permanent solution.



Windows Defence Counsel Video
Tip: Turn your sound ON and watch the video in Full Screen mode.

File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\Protector-[RANDOM 4 CHARACTERS].exe | |
| 2. | %AppData%\Protector-[RANDOM 3 CHARACTERS].exe | |
| 3. | %AppData%\NPSWF32.dll | |
| 4. | %AppData%\result.db |

