Windows Custom Management
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 6,697 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 612 |
| First Seen: | June 26, 2012 |
| Last Seen: | September 16, 2023 |
| OS(es) Affected: | Windows |
Windows Custom Management Image
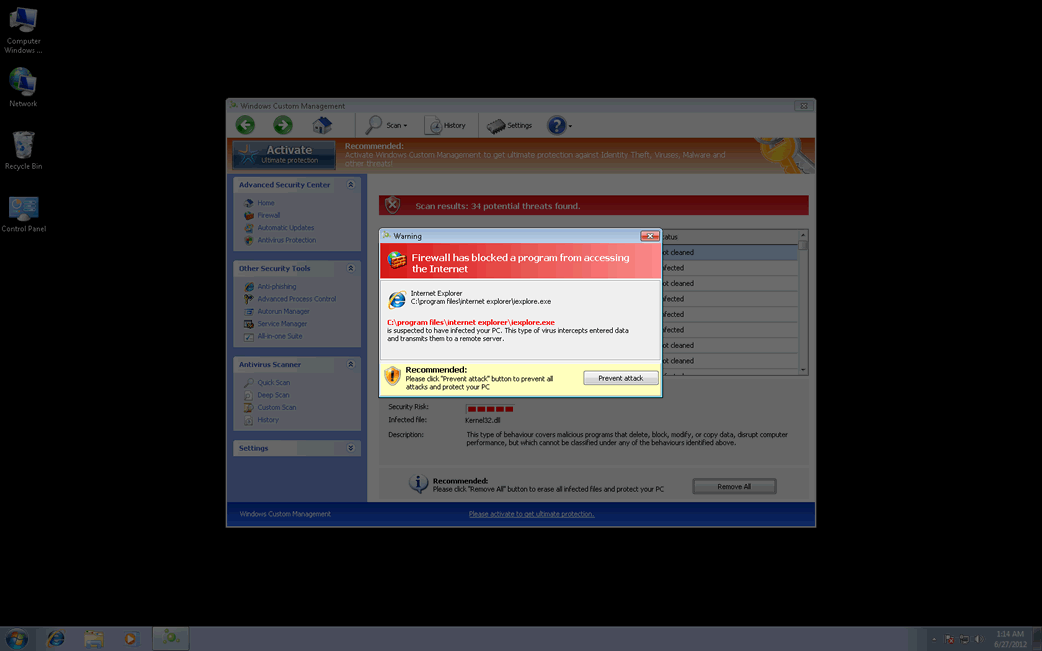
ESG security analysts have received numerous reports of an outbreak of fake security applications occurring worldwide since early 2012. The rogue security programs involved all belong to the well-known FakeVimes family of malware. However, these may be be bundled with a rootkit component, often belonging to the Sirefef (or ZeroAccess) family of rootkits. Windows Custom Management is another fake security program belonging to this batch of malware in the FakeVimes family. ESG malware researchers urge computer users to disregard all warnings from Windows Custom Management and to remove this fake security application with a reliable anti-malware tool.
Table of Contents
Windows Custom Management and the FakeVimes Family of Malware
Due to the fact that the FakeVimes family of malware has been around for several years (at least since summer of 2009), most security applications can deal easily with a FakeVimes-related infection. However, the rootkit component included in recent variants of the FakeVimes family makes them considerably more resilient than previous fake security programs in this family of rogue security software. To remove Windows Custom Management and other fake security programs released in 2012, it may be necessary to use a specialized anti-rootkit program. Examples of fake security applications in the FakeVimes family released in 2012 or previously involve Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst. All variants in the FakeVimes family of malware will pester you with annoying error messages in an attempt to persuade you that you have to purchase a 'full version' of these fake security programs.
Protecting Your Computer from Windows Custom Management and Its Clones
Most Windows Custom Management infections will begin with a social engineering attack. These kinds of attacks will usually try to trick you by trying to convince you that your PC is dangerously infected with malware. Following this, you will get messages urging you to download Windows Custom Management or one of its clones in order to remove these supposed infections for free. Of course, Windows Custom Management is actually a kind of malware program itself. To remove this invader from your computer system, ESG security researchers recommend using a reliable anti-malware program with the ability to deal with rootkit infections. You should disregard all of Windows Custom Management's warnings and never pay for its 'full version.' The registration code 0W000-000B0-00T00-E0020 can stop many of Windows Custom Management's most irritating symptoms. However, this registration code will do nothing to remove Windows Custom Management. To accomplish this, you need to use a reliable anti-malware program.
Windows Custom Management Video
Tip: Turn your sound ON and watch the video in Full Screen mode.

File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\Protector-[RANDOM CHARACTERS].exe |

