Packrat
The Packrat hacking group is an Advanced Persistent Threat (APT) that has carried out several far-reaching operations concentrated in South America – Argentina, Brazil and Ecuador. The Packrat group’s activity reached its peak back in 2015. The Packrat threat actor tends to carry out phishing and data-theft operations, alongside reconnaissance campaigns. Cybersecurity researchers have chosen this name for this hacking group as their preferred tool is RATs (Remote Access Trojans). Most of the RATs utilized by the Packrat group appear to be what is often referred to as malware-as-a-commodity. This means that the hacking tools used by the Packrat group are purchased or rented mostly. The Packrat actor appears to specialize in social engineering rather than building malware from scratch.
The Packrat hacking group is likely to be very experienced in the field of cybercrime. Their campaigns are complex and well-executed. This threat actor is known to create fake identities and whole fraudulent companies and organizations to make their social engineering tricks as polished as possible. Some malware experts believe that the Packrat group may be government-sponsored. This is due to the fact that the targets of the Packrat threat actor are often high-ranking politicians, investigative journalists, media organizations and other large companies of interest. Furthermore, it would appear that the campaigns carried out by the Packrat hacking group are rather costly to maintain – likely in the hundreds of thousands of dollars.
The Packrat group would propagate their threats via phishing operations. These campaigns would involve the previously mentioned fake organizations and identities set up by the attackers. Some of the targets of the Packrat group would be phishing via text messages too. Among the most commonly used threats by the Packrat threatening actor are Alien Spy, Adzok, Cybergate and the Xtreme RAT. The phishing campaigns of the Packrat hacking group would target login credentials for popular websites and services such as Facebook, Twitter, Google, and various instant messaging utilities. To perfect their social engineering tactics, the Packrat threat actor also will create bogus Web pages whose sole purpose is disinformation that feeds into their elaborate cons.
Table of Contents
Timeline of Events
2008-2013
The tools and command and control infrastructure that the Packrat group uses suggests that they were actively operating as early as 2008. During the first five years of the group's operation, the threat actors used hosting services located in Brazil, with some of their malware samples being uploaded to online virus scanning services from Brazilian IP's. Many of the sample messages that the Packrat group used to bait victims in that period were filled with Brazilian social engineering content, suggesting that the hackers had targeted the largest South American country exclusively.
2014-2015
After a relatively uneventful period, Packrat entered deep waters when it targeted well-known Argentinian journalist and TV news host Jorge Lanata and Alberto Nisman, a high-profile Argentine lawyer and federal prosecutor. Nisman supposedly had incriminating evidence against high-ranking officials of the Argentinian government, including the then-current President of Argentine Cristina Elisabet Fernández de Kirchner.
The discovery of the malware used by the Packrat group was made when Nisman was found dead from a gunshot wound in his Buenos Aires apartment on January 18, 2015. The forensic lab at the Buenos Aires Metropolitan Police examined Nisman's Android phone and found a malicious file named ''estrictamente secreto y confidencial.pdf.jar'', which translates to ''strictly secret and confidential'' in English.
An identical file was later uploaded to an online virus database from Argentina, revealing it to be AlienSpy, a malware-as-a-service remote access toolkit that gives threat actors the ability to record their victim's activities, access their webcam, email, and more. The file was built for Windows, meaning the attackers might have been unsuccessful in their attempts to hack Nisman, who opened it on his Android phone.
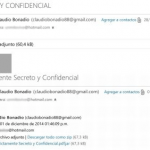
After the malware finding was made public, others came forward, saying that they had been targeted too. Máximo Kirchner, the son of then-current President of Argentina Cristina Elisabet Fernández de Kirchner and former Argentinian President Néstor Kirchner, claimed he was targeted by the same malware, providing screenshots of an email he received from someone impersonating Argentinian judge Claudio Bonadio with an address claudiobonadio88@gmail.com.
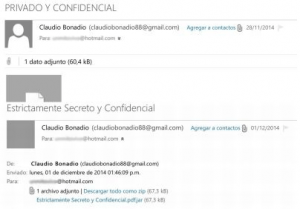
Email received by Máximo Kirchner. Source: ambito.com
An initial analysis by Morgan Marquis-Boire of Citizen Lab revealed that the malware used against Kircher, Lanata, and Nisman was linked to a command and control (C2) server named deyrep24.ddns.net. The same deyrep24.ddns.net C2 domain was found to be used by three other malware samples upon further inspection. One of the samples was a malicious document named ''3 MAR PROYECTO GRIPEN.docx.jar'' and supposedly contained communication between Ecuador's Ambassador to Sweden and Ecuadorian President Rafael Correa on the matter of fighter jet acquisition.
Researchers from Citizen Lab did further research after receiving numerous reports of phishing attacks against journalists and public figures in Ecuador in 2015. Many of the malicious emails and SMS that they examined were not politically-themed but were just credential harvesters for different email providers and social media. Further research revealed that campaign in Ecuador included explicitly political content, concerning a wide variety of political issues and figures in the country, as well as the creation of many fake profiles and organizations.
The researchers uncovered a vast web of interconnection between malware and phishing sites, used in the extensive Ecuadorian campaign. The malware they distributed was mostly Java RATs, like AlienSpy and Adzok. Many of the websites shared registration information, while the malware samples were typically communicating with daynews.sytes.net, a domain that is also linked to the Argentine cases. The investigation also revealed fake sites in Venezuela and infrastructure in Brazil.
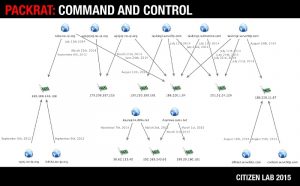
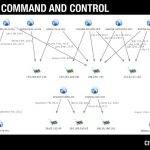
Packrat's C2 infrastructure. Source: citizenlab.ca
The Packrat hacking group has a well-developed infrastructure that has remained relatively secure for several years. The large-scale, costly, and well-polished campaigns carried out by the Packrat hacking group point to a state-sponsored actor that is well-funded and maintained.
Packrat Screenshots
URLs
Packrat may call the following URLs:
| conhost.servehttp.com |
| daynews.sytes.net |
| deyrep24.ddns.net |
| dllhost.servehttp.com |
| lolinha.no-ip.org |
| ruley.no-ip.org |
| taskmgr.redirectme.com |
| taskmgr.serveftp.com |
| taskmgr.servehttp.com |
| wjwj.no-ip.org |
| wjwjwj.no-ip.org |
| wjwjwjwj.no-ip.org |