Egregor Ransomware
Egregor Ransomware Image
The Egregor Ransomware is a new ransomware threat that, according to cybersecurity, researchers could be the beginning of a whole new family of threats. On its own, however, Egregor Ransomware's code appears to be based on the Sekhmet Ransomware with several similarities being uncovered. Both threats employ similar API calls, functions, obfuscation techniques and strings such as %Greetings2target%. Some strings have undergone minor changes - for example, %sekhmet_data% has become %egregor_data%. The new threat's name has occult connotations and means a distinct non-physical entity that arises from a collective group of people. The hackers might be considering their group to be such an entity.
Victims are Threatened with 'Mass-Media' Data Leaks
While, for the most part, Egregor operates as a typical ransomware threat, it also includes a considerable spin on the formula. Quite a few modern ransomware threats have started, including data exfiltration into their activities. The collected data is used as an additional extortion mechanism with the various criminals threatening to release it on their various websites crafted for that purpose. The Egregor Ransomware, however, takes the next step and tells its victims that the collected data will be leaked through mass-media resulting in the clients, competitors, and partners of the affected company will know about the security breach.
This Week In Malware Episode 28 Part 3: Egregor Ransomware Gang Expose Data From Ubisoft & Crytek Gaming Companies
So far no such leaks have been carried out by the hackers behind the Egregor Ransomware, but they do have a deep web site that tracks their victims in a virtual 'hall of shame.' For the moment, thirteen companies are listed there. Among the victims is GEFCO, a global logistics company that recently suffered a ransomware attack against its networks. The Egregor Ransomware appears to be targeting entities from all over the world, with affected organizations being found in Japan, Mexico, Saudi Arabia, Germany, Italy and the US.

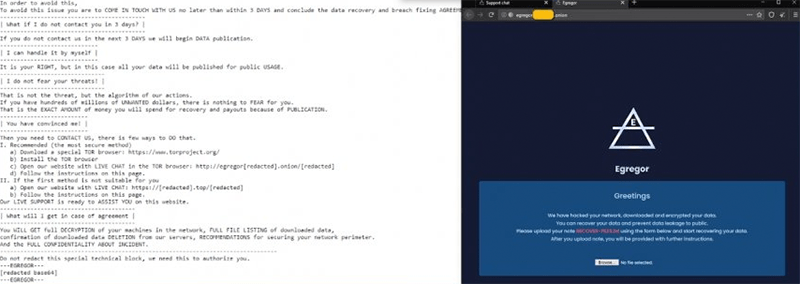
Screenshot of Egregor Ransomware threat message
The instructions left by the EgregorRansomware are dropped as a text file named 'RECOVER-FILES.txt.' No specific sum is mentioned but the hackers do promise that upon payment, they also will include security recommendations for their victims. The text of the ransom note reads:
'| What happened? |
------------------
Your network was ATTACKED, your computers and servers were LOCKED,
Your private data was DOWNLOADED.
---------------------
| What does it mean? |
----------------------
It means that soon mass media, your partners and clients WILL KNOW about your PROBLEM.
-------------------------
| How it can be avoided? |
--------------------------
In order to avoid this,
To avoid this issue you are to COME IN TOUCH WITH US no later than within 3 DAYS and conclude the data recovery and breach fixing AGREEMENT.
-------------------------------------------
| What if I do not contact you in 3 days? |
------------------------------------------
If you do not contact us in the next 3 DAYS we will begin DATA publication.
-----------------------------
| I can handle it by myself |
-----------------------------
It is your RIGHT, but in this case all your data will be published for public USAGE.
-------------------------------
| I do not fear your threats! |
-------------------------------
That is not the threat, but the algorithm of our actions.
If you have hundreds of millions of UNWANTED dollars, there is nothing to FEAR for you.
That is the EXACT AMOUNT of money you will spend for recovery and payouts because of PUBLICATION.
--------------------------
| You have convinced me! |
--------------------------
Then you need to CONTACT US, there is few ways to DO that.
I. Recommended (the most secure method)
a) Download a special TOR browser: https://www.torproject.org/
b) Install the TOR browser
c) Open our website with LIVE CHAT in the TOR browser: http://egregor[redacted].onion/[redacted]
d) Follow the instructions on this page.
II. If the first method is not suitable for you
a) Open our website with LIVE CHAT: https://[redacted].top/[redacted]
b) Follow the instructions on this page.
Our LIVE SUPPORT is ready to ASSIST YOU on this website.
----------------------------------------
| What will I get in case of agreement |
----------------------------------------
You WILL GET full DECRYPTION of your machines in the network, FULL FILE LISTING of downloaded data,
confirmation of downloaded data DELETION from our servers, RECOMMENDATIONS for securing your network perimeter.
And the FULL CONFIDENTIALITY ABOUT INCIDENT.
----------------------------------------------------------------------------------
Do not redact this special technical block, we need this to authorize you.
---EGREGOR---'

