Cloud AV 2012
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 96 |
| First Seen: | November 23, 2011 |
| Last Seen: | August 17, 2022 |
| OS(es) Affected: | Windows |
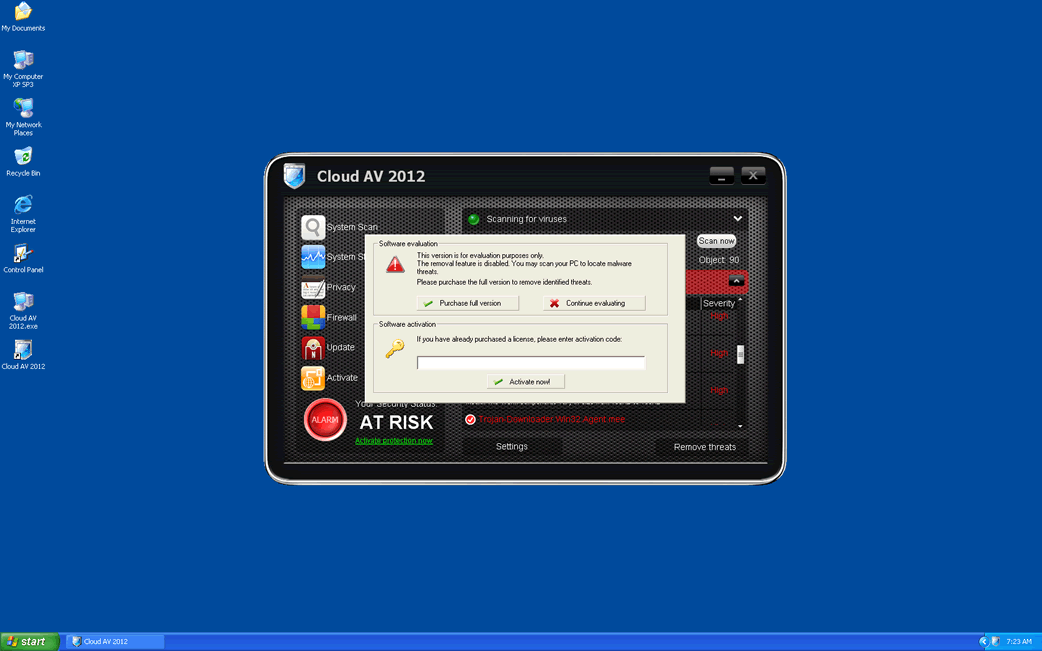
Cloud AV 2012 Image
Cloud AV 2012 is part of a very large family of malware, the FakeScanti family, comprised of a variety of fake anti-virus applications. There are dozens of versions of Cloud AV 2012, dating back to the year 2009. In fact, Cloud AV 2012 may date from before that since it is a direct successor of rogue security applications that were active in 2006. ESG PC security researchers warn against using the rogue anti-virus program Cloud AV 2012; this fake security program has absolutely no real capabilities. Beyond its flashy interface, there are little more than a collection malicious scripts and various Trojans. Cloud AV 2012 is part of a well-known online scam designed to prey on inexperienced computer users by selling them fake security applications. The main danger that lies in a Cloud AV 2012 infection is in this rogue's harmful associations. Most Cloud AV 2012 infections will be associated with a dangerous rootkit or bootkit infection. Depending on the associated rootkit, its removal may be quite difficult and require a specialized tool or the intervention of a computer security professional.
Among the many clones of Cloud AV 2012 are included such fake security programs as Security Guard, Sysinternals Antivirus, Wireshark Antivirus, Milestone Antivirus, BlueFlare Antivirus, WolfRam AntiVirus, OpenCloud Antivirus, OpenCloud Security, Data Restore, OpenCloud AV, Security Guard 2012, AV Guard Online, Guard Online, Cloud Protection, AV Protection Online, System Protection 2012, AV Security 2012, Sphere Security 2012, AV Protection 2011, Super AV 2013.
Table of Contents
How Cloud AV 2012 Affects Its Victims’ Computer System
Like most rogue security applications, Cloud AV 2012 is designed to cause the victim to panic by giving the illusion that a severe malware infection is present on the infected computer system. While this is technically true, the malware infection in question is Cloud AV 2012 itself. Cloud AV 2012 will try to convince its victims to purchase a useless "license" through the use of a credit card at Cloud AV 2012's website. To do this, Cloud AV 2012 will display a constant torrent of alarming error messages and fake security alerts. Cloud AV 2012 will also have a number of detrimental effects on an infected computer system, such as making the infected computer run slowly, crash frequently, or have its settings changed. Cloud AV 2012 may use Trojans to block access to the Internet, disable known security applications, and change your files settings so that they will be hidden from view. An inexperienced computer user, who's faced with all of these problems at once, may be predisposed to believing Cloud AV 2012's lies. Do not become a victim! Remove Cloud AV 2012 at once.
SpyHunter Detects & Remove Cloud AV 2012
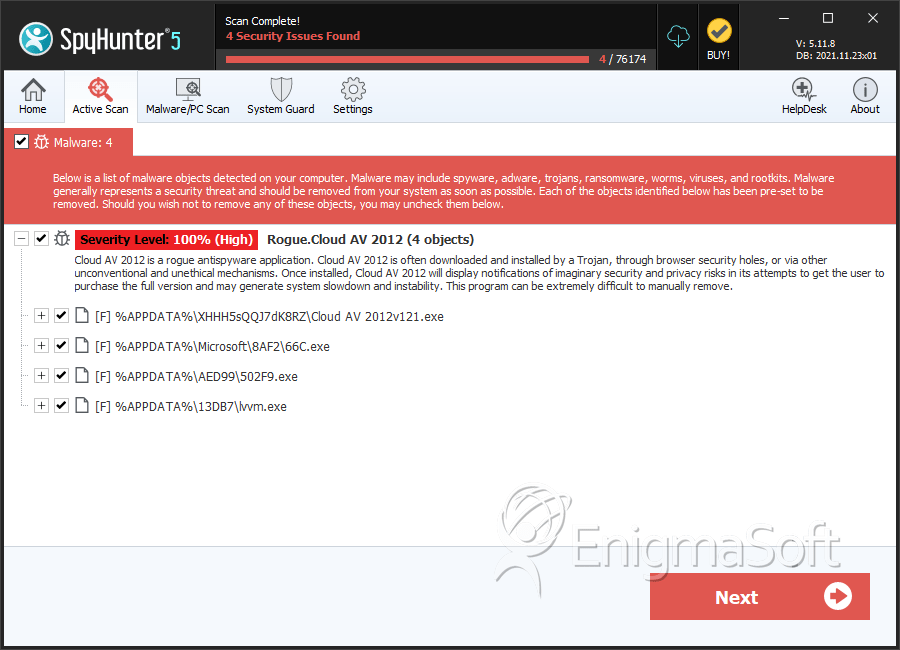
Cloud AV 2012 Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Cloud AV 2012v121.exe | 420b6e9c65701b4b6720f25762f6186d | 43 |
| 2. | 66C.exe | 535b08b0737a0524b133be6401338383 | 12 |
| 3. | Cloud AV 2012v121.exe | b199c92af7b4a1f1427f7ebff90e0615 | 5 |
| 4. | 502F9.exe | a206e763d2bbed0eee677180c0ebe359 | 2 |
| 5. | lvvm.exe | 430ab1341e367ee43e2c57e9accd7be2 | 2 |
| 6. | %Local_AppData%\dwme.exe | ||
| 7. | %Windows%\system32\[RANDOM CHARACTERS].exe | ||
| 8. | %TempDir%\dwme.exe | ||
| 9. | %SystemDir%\Cloud AV 2012v121.exe | ||
| 10. | %SYSTEM%\Cloud AV 2012v121.exe | ||
| 11. | %PROGAM_FILES%\24245\lvvm.exe | ||
| 12. | %AppData%\FCE03\0FD4B.exe | ||
| 13. | %ProgramFiles%\03F0D\lvvm.exe | ||
| 14. | %AppData%\dwme.exe | ||
| 15. | %PROGAM_FILES%\LP\BAD6\C29.exe | ||
| 16. | %Documents and Settings%\[USERNAME]\Application Data\svhostu.exe | ||
| 17. | %ProgramFiles%\LP\4B7F\027.exe | ||
| 18. | %AppData%\ldr.ini | ||
| 19. | %Documents and Settings%\[USERNAME]\Application Data\[RANDOM CHARACTERS]\ | ||
| 20. | %AppData%\FCE03\3F0D.CE0 | ||
| 21. | %ProgramFiles%\LP\4B7F\2.tmp | ||
| 22. | %Programs%\Cloud AV 2012\Cloud AV 2012.lnk | ||
| 23. | %DesktopDir%\Cloud AV 2012.lnk | ||
| 24. | %Documents and Settings%\[USERNAME]\Local Settings\Temp\[random].tmp | ||
| 25. | %Documents and Settings%\[USERNAME]\Desktop\Cloud AV 2012.lnk | ||
| 26. | %TempDir%\1.tmp | ||
| 27. | %ProgramFiles%\LP\4B7F\4.tmp | ||
| 28. | %Temp%\8.tmp | ||
| 29. | %AppData%\[RANDOM CHARACTERS]\Cloud AV 2012.ico | ||
| 30. | %Documents and Settings%\[USERNAME]\Start Menu\Programs\Cloud AV 2012\ | ||
| 31. | %AppData%\LUUJ1wscH0aTNzF\Cloud AV 2012.ico | ||
| 32. | %ProgramFiles%\LP\4B7F\3.tmp | ||
| 33. | %Desktop%\Cloud AV 2012.lnk |

