Cloud Protection
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 43 |
| First Seen: | October 10, 2011 |
| Last Seen: | August 17, 2022 |
| OS(es) Affected: | Windows |

Cloud Protection Image
Cloud Protection is a fake anti-virus program that belongs to the Guard Online family of rogue anti-virus programs. Do not be fooled by Cloud Protection's sleek black interface with big colorful buttons and red lettering. Despite Cloud Protection's stylish design, Cloud Protection is nothing more than a fake anti-virus application designed to scam inexperienced computer users. Cloud Protection will always detect a virus infection, usually with big alarming red letters and a fake system scan. This virus infection is, of course, completely imaginary. Cloud Protection is part of a well-known scam that has been around in some variation or another for a very long time. ESG security researchers recommend handling a Cloud Protection infection with a real and reliable anti-virus application. Failure to remove Cloud Protection from your computer system can result in the loss of your personal data, your credit card information being stolen, and at risk of further malware infections.
Table of Contents
How the Cloud Protection Scam Works
Rogue security programs like Cloud Protection are part of a scam that is aimed at inexperienced computer users. The Cloud Protection scam basically boils down to convincing the victim to pay for this fake anti-virus program, by claiming that the computer system is severely infected with a variety of viruses and Trojans. Cloud Protection achieves this in a number of different ways:
- Cloud Protection directly attacks Cloud Protection's victim with a barrage of fake error messages, security alerts, system alerts and pop-up notifications from the task bar. Cloud Protection also displays a number of alarming messages in Cloud Protection's interface, using big red letters. To add to the illusion that the victim's computer is severely infected, Cloud Protection also runs a fake system scan upon start-up, forcing the victim to wait while a progress bar slowly fills up. This is all just for show, since, regardless of the actual virus problems on the infected computer, the results will always be the same.
- Cloud Protection consumes system resources, and often comes into conflict with other installed programs, services and applications. This means that the victim's computer will often become slow, inefficient, and unstable.
- Cloud Protection uses a variety of different malicious scripts, Trojans, and may even use a rootkit, in order to hide itself, prevent legitimate security applications from removing and detecting Cloud Protection, block access to the Internet and hide the user's files. These kinds of activities reinforce the illusion that there is something seriously wrong with the victim's computer system.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Sophos | Mal/FakeAV-OZ |
| NOD32 | a variant of Win32/Kryptik.AAJZ |
| Panda | Adware/WindowsRecovery |
| BitDefender | Gen:Variant.Kazy.40147 |
| NOD32 | a variant of Win32/Kryptik.TWI |
| Ikarus | Trojan.Win32.Jorik |
| McAfee-GW-Edition | Artemis!1B426E933853 |
| Kaspersky | Trojan.Win32.Jorik.Fraud.fla |
| NOD32 | a variant of Win32/Kryptik.UES |
| McAfee | Generic FakeAlert.bz |
| GData | Win32:FakeAlert-BHX |
| AntiVir | TR/Fakealert.TZ |
| DrWeb | Trojan.Packed.189 |
| Kaspersky | Trojan.Win32.Jorik.Fraud.fmf |
| Avast | Win32:FakeAlert-BHX [Trj] |
SpyHunter Detects & Remove Cloud Protection
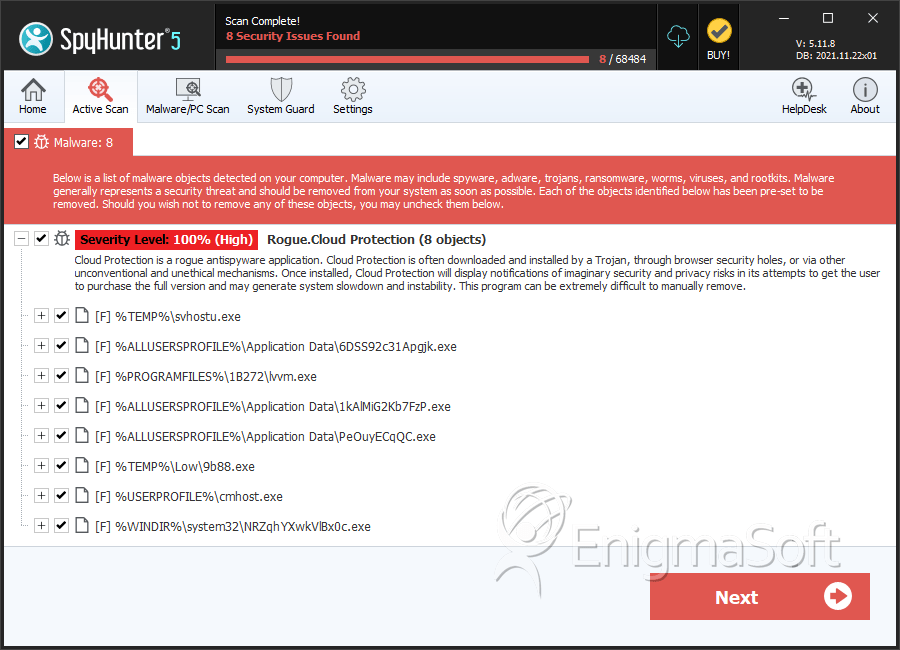
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | svhostu.exe | 55e3ebfc4a5b7a14a46b9051c10a08ec | 14 |
| 2. | 6DSS92c31Apgjk.exe | 15d961278fc23d262a41b43c91b79849 | 6 |
| 3. | lvvm.exe | 30b417d498af215d9d4c04f9182813f7 | 5 |
| 4. | 1kAlMiG2Kb7FzP.exe | 19db38e4385b31dd3460bffd8be2ee7f | 3 |
| 5. | PeOuyECqQC.exe | 1b426e933853d2bcb271183c696a3084 | 3 |
| 6. | NRZqhYXwkVlBx0c.exe | 9ca34506acf87aa24c3bbd1ea2218609 | 2 |
| 7. | svhostu.exe | 07c237f3ee4e19dbf8058166e766333c | 2 |
| 8. | 9b88.exe | a537b08413c63a31533833bed1002b13 | 1 |
| 9. | cmhost.exe | 999ab3d32d2aa4c05962142ebbca8f41 | 1 |
| 10. | eDQmkk06sEUM5g.exe | b8d9e640f6eb41142455c213a1e01b97 | 1 |
| 11. | %Programs%\Startupcrss.exe | ||
| 12. | %TempDir\svhostu.exe | ||
| 13. | %SystemDir%\D88olEDV7kS7kSu.exe | ||
| 14. | %AppData%\E77ikC6uQA5hAym | ||
| 15. | %AppData%\g44tgnOLrfI2dJw\Cloud Protection.ico | ||
| 16. | %ProgramFiles\Internet Explorer\1.tmp | ||
| 17. | %TempDir\2.tmp | ||
| 18. | %AppData%\g44tgnOLrfI2dJw | ||
| 19. | %Programs%\Cloud ProtectionCloud Protection.lnk | ||
| 20. | %Desktop%\Cloud Protection.lnk | ||
| 21. | %AppData%\GxxTGN9pzF | ||
| 22. | %AppData%\ldr.ini |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.