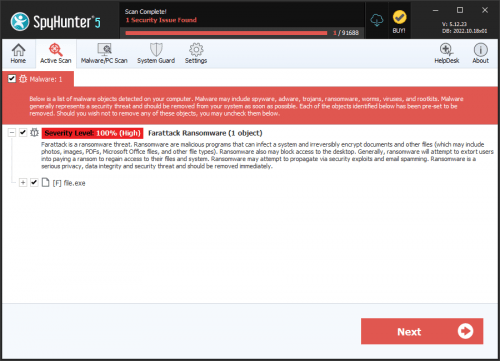
Attack Ransomware
The Attack Ransomware is a new malware threat that targets the data of its victims. According to cybersecurity researchers, the threat encrypts numerous different filetypes and demands payment for their decryption. When the Attack Ransomware locks a file, it appends that file's original name with a '.attack[number]' extension, with the number varying depending on the specific version of the malware. For instance, a file with the name "1.jpg" could be transformed into "1.jpg.attack5", among other possible variations. Another important fact is that Attack Ransomware belongs to the MedusaLocker Ransomware family.
Once the encryption process is completed, Attack creates a ransom-demanding message named 'how_to_back_files.html.' This message contains information that suggests that the ransomware targets companies rather than home users. It is worth noting that the Attack ransomware can cause serious damage to companies, as it can lock out their critical data and disrupt their operations until a ransom is paid.
The Attack Ransomware Renders Its Victims' Data Unusable
According to the ransom note left by the attackers, the victim's company networks have been compromised, and their files have been encrypted using RSA and AES cryptographic algorithms. The message warns against renaming or modifying the affected files and also advises against using third-party decryption tools since doing so will render the files undecryptable.
Furthermore, the ransom note informs the victims that their highly sensitive data has been exfiltrated. The attackers demand that the victims pay an unspecified ransom, and the amount will increase if contact is not established within 72 hours. Before meeting the ransom demands, the victims are given the option to test the decryption on three files. They can establish contact with the threat actors by messaging the 'ithelp01@decorous.cyou' email address.
However, the attackers threaten that if the victims refuse to pay the ransom, they will publicly disclose or sell the stolen data. It is generally impossible to decrypt the files without the cybercriminals' interference. The only exceptions are when the ransomware is severely flawed.
Even if the ransom demands are met, victims often do not receive the decryption keys or software. As a result, paying the ransom is not advisable since data recovery is not guaranteed, and it also supports illegal activities. Therefore, it is recommended that victims seek alternative means of data recovery and report the incident to the relevant authorities.
Users Should Protect Their Data from Potential Ransomware Infections
Ransomware attacks can have a devastating impact on individuals, businesses, and organizations. These attacks can cause data loss, disrupt operations, and even result in financial loss. Therefore, it is crucial for users to take appropriate measures to protect their data and devices from potential ransomware attacks.
One of the most efficacious ways to protect against ransomware attacks is by being proactive. Users should regularly update their software and operating systems to patch any known vulnerabilities that could be exploited by attackers. They should also regularly back up their data, storing it in a secure location that is not connected to the Internet. This way, if their data is encrypted by ransomware, they can restore it without having to pay the ransom.
It also is essential to be cautious when accessing email attachments or clicking on links from unknown or suspicious sources. Ransomware attacks are often spread through phishing emails or malicious links. Users should avoid opening attachments or clicking on links from unfamiliar sources, and they should be wary of emails that ask them to provide personal information or login credentials.
Another useful tip is to install and regularly update any anti-malware software. These tools can detect and remove known threats, helping to prevent ransomware attacks from infecting your device. Additionally, users should enable firewalls, which can help prevent unauthorized access to their devices and network.
The full text of Attack Ransomware's note is:
'YOUR PERSONAL ID:
/!\ YOUR COMPANY NETWORK HAS BEEN PENETRATED /!\
All your important files have been encrypted!Your files are safe! Only modified. (RSA+AES)
ANY ATTEMPT TO RESTORE YOUR FILES WITH THIRD-PARTY SOFTWARE
WILL PERMANENTLY CORRUPT IT.
DO NOT MODIFY ENCRYPTED FILES.
DO NOT RENAME ENCRYPTED FILES.No software available on internet can help you. We are the only ones able to
solve your problem.We gathered highly confidential/personal data. These data are currently stored on
a private server. This server will be immediately destroyed after your payment.
If you decide to not pay, we will release your data to public or re-seller.
So you can expect your data to be publicly available in the near future..We only seek money and our goal is not to damage your reputation or prevent
your business from running.You will can send us 2-3 non-important files and we will decrypt it for free
to prove we are able to give your files back.Contact us for price and get decryption software.
email:
ithelp01@decorous.cyou
ithelp01@decorous.cyouTo contact us, create a new free email account on the site: protonmail.com
IF YOU DON'T CONTACT US WITHIN 72 HOURS, PRICE WILL BE HIGHER'