Paradise Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 763 |
| First Seen: | September 13, 2017 |
| Last Seen: | December 7, 2021 |
| OS(es) Affected: | Windows |
The Paradise Ransomware is an encryption ransomware Trojan first observed in the second week of September 2017. The Paradise Ransomware is part of a Ransomware as a Service (RaaS) platform that includes threats such as the TeslaWare. These services allow the con artists to lease a third-party to create and manage ransomware Trojans, which they can customize and distribute depending on the targets they want to attack. The people responsible for the RaaS receive a percentage of the profits while taking care of managing payments and maintaining them up-to-date. The person hiring the services of the RaaS can choose the way they will distribute the Paradise Ransomware. Some common ways of distributing these threats include corrupted spam email attachments and various compromised online websites and content.
Table of Contents
The Paradise Ransomware and Its Use of RaaS
There are not many details about the RaaS platform since it runs anonymously and all communications are carried out on the Dark Web. The initial Paradise Ransomware attacks were targeted to Western Europe and the United States. The first variants of the Paradise Ransomware run as 'DP_Main.exe' on the infected computer and target computers running the Windows operating system. Like most encryption ransomware Trojans, the Paradise Ransomware is designed to encrypt the victim's data, then requesting that the victim pays a ransom in exchange for the decryption key. Otherwise, the victim's data will be lost forever. The Paradise Ransomware targets the user-generated files, including video, music, spreadsheets, configuration files, archives, and a wide variety of other commonly used file types. The files encrypted by the Paradise Ransomware are marked with the file extension '.paradise' and a unique identifier is added to this extension, which supposedly corresponds to an ID issued by the RaaS to the people hiring their services.
How the Paradise Ransomware Demands Its Ransom Payments
The files renamed by the Paradise Ransomware follow this pattern:
[file name].id-[affiliate_id].[affiliate_email].paradise
There have been several email addresses associated with the people using the Paradise Ransomware. The Paradise Ransomware delivers its ransom note in the form of a text file named '#DECRYPT MY FILES#.txt' dropped on the victim's desktop. The Paradise Ransomware's ransom note contains the following text:
'[WHAT HAPPENED]
Your important files produced on this computer have been encrypted due a security problem
If you want to restore them, write us to the e-mail: info@decrypt.ws
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
[FREE DECRYPTION AS GUARANTEE]
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information and their total size must be less than 1Mb
[HOW TO OBTAIN BITCOINS]
The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the seller by payment method and price
hxxps://localbitcoins.com/buy_bitcoins
[ATTENTION]
Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
If you not write on e-mail in 36 hours - your key has been deleted and you cant decrypt your files'
Dealing with a Paradise Ransomware Attack
The best way to protect your data from threats like the Paradise Ransomware is to have a reliable backup system in place. If you have file backups, then you can recover from the attack by restoring the files from the backup copy. This will undo the con artists' strategy to extort you and demand money. Apart from using a reliable backup method, PC security researchers also recommend that computer users have a security program that is fully up-to-date, which can be used to intercept and remove threats like the Paradise Ransomware from a targeted computer (although they will not restore the files already encrypted).
Update December 24th, 2018 — '.VACv2 File Extension' Ransomware
The '.VACv2 File Extension' Ransomware is categorized as a variant of the Paradise Ransomware that was released on December 24th, 2018. The new variant is named after the file marker placed on the encrypted content that is found in a custom suffix placed on filenames. The '.VACv2 File Extension' Ransomware uses a renaming scheme similar to the one used by the GandCrab Ransomware. Also, some users reported the '.VACv2' extension being listed with the name GandCrab 5.0.4 Ransomware that was identified in October 2018. We have no definitive proof that the '.VACv2 File Extension' Ransomware is based on GandCrab, but threat actors may use snippets of code associated with the GandCrab Ransomware and simply use other names to mislead security researchers. The '.VACv2 File Extension' Ransomware is observed to encode text, images, audio, video, databases, PDFs and eBooks by using a custom AES cipher. The filenames receive a new suffix that looks like this: _
'Your files are encrypted!
Paradise Ransomware Team!
Your personal ID
[16 random characters]
WHAT HAPPENED!
Your important files produced on this computer have been encrypted due to a security problem.
If you want to restore them, write to us by email.
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment, we will send you the decryption tool that will decrypt all your files.
Contact!
email: pittt@prt-decrypt.xyz'
The threat actors may offer victims to decrypt one file under 3 MB of size as proof that there is a decryptor. PC users who forgot to make a backup recently may consider paying money to the '.VACv2 File Extension' Ransomware creators. However, you should not trust the people behind the Paradise Ransomware. It is safer to use available data backups, check your email account for recently exchanged files and use older versions of your data from file hosting services. PC security experts remind users that the ransomware business may be in decline, but there are successful RaaS platforms that are still working, and you need to install a useful backup tool on your system.
Update January 4th, 2019 — 'alexbanan@tuta.io' Ransomware
The 'alexbanan@tuta.io' Ransomware is a generic encryption Trojan that appeared shortly after the '.VACv2 File Extension' Ransomware. The 'alexbanan@tuta.io' Ransomware is a member of the Paradise Ransomware family that behaves the same way as the original cyber threat. The threat authors use email accounts to spread the Trojan, but their tactics remain the same — an attached macro-enabled document is received via email claiming to offer important updates to social media and business propositions. PC users may be intrigued to find out more and load a corrupted macro script that installs the 'alexbanan@tuta.io' Ransomware on their devices in the background. The program at hand is reported to use the AES and RSA ciphers to lock content on the compromised devices. Also, the Trojan runs a command in the Command Line tool so that the System Restore points and the Shadow Volume snapshots are erased. The 'alexbanan@tuta.io' Ransomware encodes your typical file formats associated with photos, music, smartphone videos, office documents and some databases. The 'alexbanan@tuta.io' Ransomware marks files by adding the '._
'Your files are encrypted!
Paradise Ransomware Team!
Your personal ID
[16 random characters]
WHAT HAPPENED!
Your important files produced on this computer have been encrypted due to a security problem.
If you want to restore them, write to us by email.
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment, we will send you the decryption tool that will decrypt all your files.
Contact!
email: alexbanan@tuta.io'
There is no free decryption tool for the users affected by the 'alexbanan@tuta.io' Ransomware at the time of writing this. PC users need to be proactive in defending against threats like the Paradise Ransomware and other variants. You can use backup managers to produce protected archives with your data and make sure you have more than two data backups. That way you would not have to worry if the 'alexbanan@tuta.io' Ransomware managed to lock your content entirely. PC users are advised to disable macros entirely or enable macros from approved sources only.
November 2019 Update
Thanks to the efforts of the cybersecurity community and dedicated researchers, there is now a free decryption tool that can recover files scrambled by the Paradise ransomware.
The decryption tool can recover files with a number of different extensions used in various Paradise ransomware campaigns, including ".paradise", ".2ksys19", ".FC" and ".p3rf0rm4". The tool is a completely free download and comes with a detailed instruction manual with step-by-step instructions. However, Paradise Ransomware must still be removed from the infected system utilizing an antimalware resource. Otherwise, the threat may remain on the infected computer and later cause serious issues or encrypt additional files.
SpyHunter Detects & Remove Paradise Ransomware
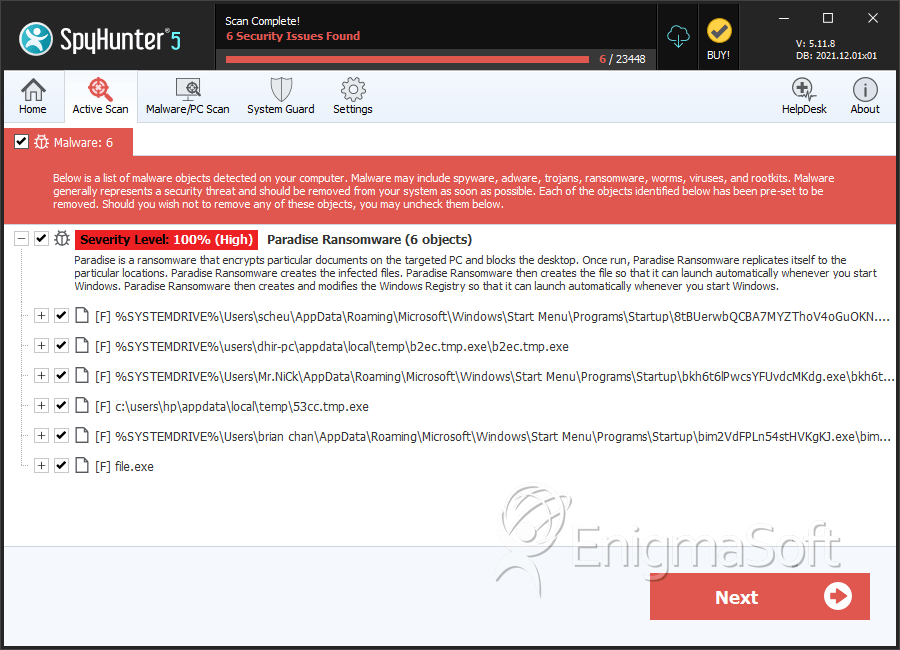
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 8tBUerwbQCBA7MYZThoV4oGuOKN.exe | a25cad303bd117999ef90678b14969be | 300 |
| 2. | b2ec.tmp.exe | 7902fbf7c2c7d09290dc042a6c3e4ccc | 263 |
| 3. | bkh6t6lPwcsYFUvdcMKdg.exe | a3c88bfcd317f5e57c84b32f9d545aab | 37 |
| 4. | 53cc.tmp.exe | 0f7e6c13bd84333001688893dc6c242e | 17 |
| 5. | bim2VdFPLn54stHVKgKJ.exe | f26b38954b3558da7e9bb6566d396e81 | 8 |
| 6. | file.exe | 8aa00ee509a649619794fc1390319293 | 2 |

