Globe Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 17,204 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 49,628 |
| First Seen: | August 24, 2016 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The Globe Ransomware has the potential to inflict quite a lot of damage. The Globe Ransomware is a typical ransomware Trojan, designed to encrypt the victim's files, taking them hostage essentially. The Globe Ransomware then demands the payment of a ransom in exchange for the key needed to decrypt the affected files. Ransomware Trojans like the Globe Ransomware have become quite popular in recent times, making it necessary for computer users to learn how to protect themselves and their files from infections like the Globe Ransomware. Unfortunately, it may be nearly impossible to decrypt the files that have been encrypted by the Globe Ransomware or other ransomware Trojans that use advanced encryption algorithms and an encryption method that makes it impossible to extract a decryption key from the affected computer. The best protection against threats like the Globe Ransomware is to have appropriate backups for all files on a computer.
Table of Contents
The Main Targets of the Globe Ransomware are Small Business
Currently, the Globe Ransomware is not very widespread. The main targets of the Globe Ransomware are located in Central Asia. The amount demanded by the Globe Ransomware changes, and is somewhere between 1 and 3 BitCoins (which is currently between $600 and $1800 USD at the current exchange rates). One particularly worrying aspect of the Globe Ransomware is that it seems to target small businesses mainly, making the potential for damage from the Globe Ransomware larger than with other ransomware threats.
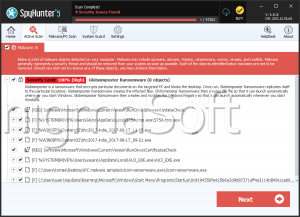
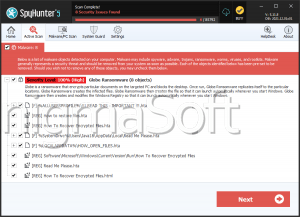
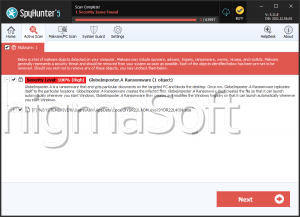
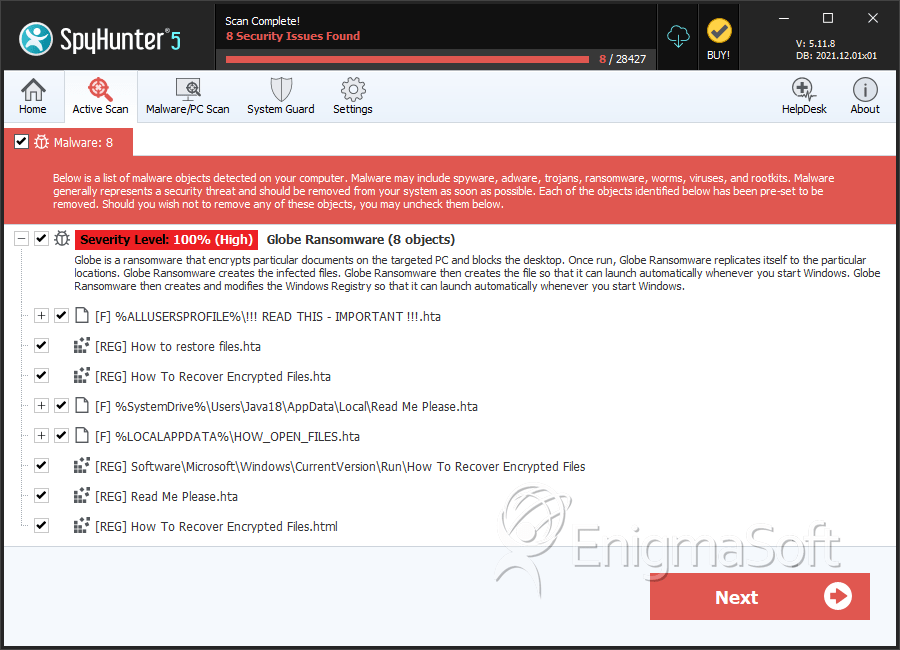
After encrypting a victim's files, the Globe Ransomware drops a ransom note contained in a file named 'How to restore your files.hta,' which contains instructions on how to pay the Globe Ransomware ransom and recover the encrypted files. The victims are instructed to contact the con artists at an email address on the domain @tutanota.com. The Globe Ransomware attack is fairly straightforward. The Globe Ransomware may be delivered through a corrupted email attachment. This email attachment drops an executable file on the victim's computer, which carries out the encryption. In most cases, the Globe Ransomware will avoid files that are essential for Windows to function, instead targeting documents and media files that the computer users would have a hard time recovering without a backup. The Globe Ransomware is designed to run automatically whenever Windows starts up, and recovery from this threat will require the use of an updated and resourceful anti-malware program to ensure that the Globe Ransomware infection is completely removed.
How Threats Like the Globe Ransomware may be Delivered
The most common delivery method for threats like the Globe Ransomware is the use of corrupted email attachments that may use social engineering techniques like fake tax returns or receipts to convince computer users to open corrupted email attachments. Because of this, educating computer users on handling email and using reliable anti-spam filters properly are among the best measures that can be taken to prevent the Globe Ransomware attacks and infections with similar threats. There are other ways in which the Globe Ransomware can be delivered, including corrupted online advertisements, exploit kits, and the direct hacking of the victim's computer. General online security measures, strong anti-malware software, and keeping all programs fully up-to-date will help computer users to avoid Globe Ransomware infections, as well as problems with other threats.
Dealing with a Globe Ransomware Infection
Unfortunately, removing the Globe Ransomware infection will not decrypt the victim's files. Because of this, it will be necessary to not only remove the Globe Ransomware itself but also restore the affected files from a backup location. Malware analysts strongly advise against paying the Globe Ransomware's ransom. Paying these enormous amounts to recover files only allows con artists to continue creating threats. Remember that, when dealing with con artists such as these, there is no guarantee that they will keep their word and restore the affected files after the computer user pays the Globe Ransomware ransom.
SpyHunter Detects & Remove Globe Ransomware
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | !!! READ THIS - IMPORTANT !!!.hta | 2b7bd31fd3447cd1b0e0bdfd690b0740 | 442 |
| 2. | HOW_OPEN_FILES.hta | e3b9bb7ca0576dfe90e94aac1d333630 | 75 |
| 3. | Read Me Please.hta | 58f8086cdb674cc03cced8e65d495c44 | 25 |
| 4. | trust.exe | 668c83c1f7f13259ab5d1699ea24d17f | 2 |
| 5. | How to restore files.hta | 503478dce7398eac1ce8cc7db0fea7b9 | 1 |
| 6. | file.exe | a464f7bc0431292d74ad66403efbf691 | 0 |