Globe Imposter 2.0 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 17,016 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 5,568 |
| First Seen: | August 8, 2017 |
| Last Seen: | July 2, 2023 |
| OS(es) Affected: | Windows |
Globe Imposter 2.0 Ransomware Image
The Globe Imposter 2.0 Ransomware is a successor of Globe Imposter, a fake version of the infamous Globe Ransomware Trojan that was released in the final months of 2016. The release of unsophisticated threats disguised as more threatening (and often well-known) threats is a common tactic among con artists, often used to increase the likelihood that the victims of the attack will pay the ransom that these threats demand. The most common way in which the Globe Imposter 2.0 Ransomware is being distributed is through the use of corrupted email attachments. The victims will receive a spam email message with an attached DOCX file, opened in Microsoft Word. This file will include a bad macro script that downloads and installs the Globe Imposter 2.0 Ransomware when the file is opened. Learning how to handle spam email and unsolicited email attachments is an essential aspect of dealing with the Globe Imposter 2.0 Ransomware and similar threats.
Table of Contents
How the Globe Imposter 2.0 Ransomware Attack Works
Like other encryption ransomware Trojans, the Globe Imposter 2.0 Ransomware will encrypt the victim's files using the AES 256 encryption. The Globe Imposter 2.0 Ransomware searches for files with certain file extensions and makes them inaccessible, with the intention of taking them hostage so that the victim will pay a ransom amount. After encrypting the victim's data, the Globe Imposter 2.0 Ransomware will display a ransom note on the victim's machine, demanding the payment of a ransom in exchange for the decryption key necessary to recover the affected files. The Globe Imposter 2.0 Ransomware targets 34 different file types, looking for files that are user-generated. Once the files have been encrypted, the Globe Imposter 2.0 Ransomware will add a new file extension to mark each affected file. Different variants of the Globe Imposter 2.0 Ransomware have been observed to add the following file extensions to the affected files:
.bad; .BAG; .FIX; .FIXI; .legally;n .keepcalm; .pizdec; .virginlock[byd@india.com]SON;
.[xalienx@india.com]; .725; .ocean; .rose; .GOTHAM; .HAPP; .write_me_[btc2017@india.com]; .726; .490; n.skunk.
The Globe Imposter 2.0 Ransomware demands a ransom payment that can range from 1 to 10 BitCoins (thousands of dollars!) Several contact email addresses have been associated with the Globe Imposter 2.0 Ransomware attack, including the following:
- keepcalmpls@india.com;
- happydaayz@aol.com;
- strongman@india.com;
- byd@india.com;
- xalienx@india.com;
- 511_made@cyber-wizard.com;
- btc.me@india.com.
The Globe Imposter 2.0 Ransomware Ransom Note
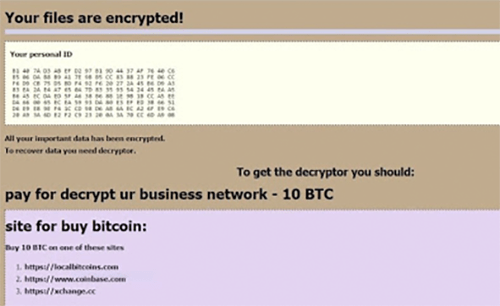
The Globe Imposter 2.0 Ransomware ransom note varies from one variant to the other. A general ransom note used by the Globe Imposter 2.0 Ransomware variants is an HTA file named 'HOW_OPEN_FILES.hta,' which will be placed on the infected computer's desktop. The following, for reference, is the text of the ransom note used by the previous version of the Globe Imposter 2.0 Ransomware:
'Your files are encrypted!
Your personal ID
***
All your important data has been encrypted. To recover data you need decryptor.
To get the decryptor you should:
pay for decrypt:
site for buy bitcoin:
Buy 1 BTC on one of these sites
1. https://localbitcoins.com
2. https://www.coinbase.com
3. https://xchange.cc
bitcoin adress for pay:
jlHqcdC83***:
Send 1 BTC for decrypt
After the payment:
Send screenshot of payment to alex_pup@list.ru . In the letter include your personal ID (look at the beginning of this document).
After you will receive a decryptor and instructions
Attention!
• No Payment = No decryption
• You realy get the decryptor after payment
• Do not attempt to remove the program or run the anti-virus tools
• Attempts to self-decrypting files will result in the loss of your data
• Decoders other users are not compatible with your data, because each user's unique encryption key'
Dealing with the Globe Imposter 2.0 Ransomware
The best protection against the Globe Imposter 2.0 Ransomware is file backups. Having the power to recover the affected files from a backup undoes the strategy of the Globe Imposter 2.0 Ransomware attackers completely, allowing computer users to restore their files easily. A reliable security program also should be used to protect your computer.
Update November 30th, 2018 — The 'bizarrio@pay4me.in' Ransomware
is a file cryptor Trojan that you may have the misfortune of encountering if you access corrupted documents on your computer. The 'bizarrio@pay4me.in' Ransomware is distributed via spam emails, and it is classified as a mid-tier crypto-threat. You should know that the 'bizarrio@pay4me.in' Ransomware is not a unique cyber-threat. The 'bizarrio@pay4me.in' Ransomware is a new version of the Globe Imposter 2.0 Ransomware, which emerged as a fake version of the Globe Ransomware back in December 2016. The Globe Imposter 2.0 family of malware expanded to include threats like the Kimchenyn Ransomware and the Uridzu Ransomware.
Now, it appears that the program creators have made an effort to produce an improved version that we refer to as the 'bizarrio@pay4me.in' Ransomware. The new version is known to target more than fifty file types and attach a marker to the encrypted objects. The first wave of incidents associated with the Trojan show that it appends the '.crypted_bizarrio@pay4me_in' suffix to filenames. For example, 'Black Library - Howl of the Banshee.epub' is renamed to 'Black Library - Howl of the Banshee.epub.crypted_bizarrio@pay4me_in' and a ransom note named 'how_to_back_files.html' is dropped to the desktop. The ransom notification is likely to be loaded in the system's default Web browser once the malware deletes its files from the Temp folder. The message presented by the 'bizarrio@pay4me.in' Ransomware reads:
'YOUR FILES ARE ENCRYPTED!
Your documents, photos, databases and all the rest files encrypted cryptographically strong algoritm. Without a secret key stored with us, the restoration of your files is impossible
To start the recovery process:
Send an email to: bizarrio@pay4me.in with your personal ID in the message body.
In response, we will send you further instructions on decrypting your files.
Your personal ID:
[random characters]
P.S.
It is in your interest to respond as soon as possible to ensure the recovery of your files, because we will not store your decryption keys on our server for a long time.
Be sure to add our email addresses to the trusted list, in your email client's settings. And also check the folder "Spam" when waiting for an email from us.
If we do not respond to your message for more than 24 hours, write to the back-up email:
bizarrio@venom.io'
We recommend avoiding contact with the ransomware operators via 'bizarrio@venom.io' and 'bizarrio@pay4me.in.' You should remove the 'bizarrio@pay4me.in' Ransomware using a credible anti-malware instrument and load data backups to recover your files. Complying with the ransom demands is not likely to lead to a favorable outcome for you. PC users should take the time to install a backup manager considering the spread of data wipers and ransomware in recent months.
SpyHunter Detects & Remove Globe Imposter 2.0 Ransomware
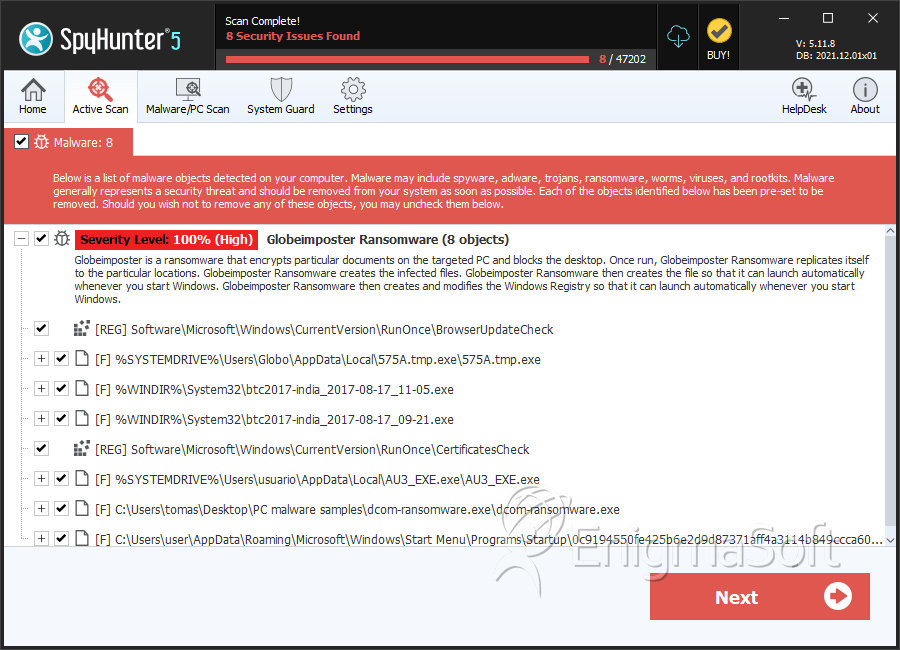
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 575A.tmp.exe | 86a8e2327f003d25a2abef413473218b | 594 |
| 2. | btc2017-india_2017-08-17_11-05.exe | b4ed40a147d3e280e85b4f40d64a93b4 | 97 |
| 3. | btc2017-india_2017-08-17_09-21.exe | 04d852a8b7f29ca797bbdb82eb0ae874 | 59 |
| 4. | AU3_EXE.exe | d78a1829b5c9db3ef2fe01d43cdd91b6 | 21 |
| 5. | dcom-ransomware.exe | afe5f38b22233a2f63b5527da807cf10 | 5 |
| 6. | 0c9194550fe425b6e2d9d87371aff4a3114b849ccca60b220fdd37e5d2b5be8d.exe | 70f5ed63c92fea27f8f8e5c2413bf323 | 2 |
| 7. | file.exe | 1905c6ac4e63e975690669fa183943bf | 1 |
| 8. | file.exe | 8552042bd59e3ff6b9fb97f5f7778ee1 | 1 |
| 9. | file.exe | bfc214a781108b92d143b896b56b202b | 0 |
| 10. | 7afd55f0c98f65d41f836613d825a895 | 7afd55f0c98f65d41f836613d825a895 | 0 |
| 11. | IGAMI.exe | b02dbce0663e5a22bdbe5241110a7a80 | 0 |

