Factfull Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 6 |
| First Seen: | January 26, 2022 |
| Last Seen: | January 27, 2022 |
| OS(es) Affected: | Windows |
The Factfull Ransomware can be used in attacks against users that will lock the data stored on their computers. The threat is designed to affect numerous file types specifically, while the encryption algorithm it uses ensures that the locked files will not be easily restored. The discovery of this particular ransomware is attributed to the infosec researcher who goes by GrujaRS on Twitter. Analysis has confirmed that the Factful Ransomware is a variant from the Makop malware family.
Apart from locking nearly all of the data found on the breached devices, the Factful Ransomware also will modify the names of the affected files. First, the threat will assign a string of characters to act as the ID of the specific victim. This character string will be followed by an email address (factfull0103@airmail.cc email) controlled by the attackers. Finally, '.factfull' will be appended as a new file extension.
Table of Contents
Factfull Ransomware’s Demands
The ransom message of the threat will be dropped on the victim's system as a text file named 'readme-warning.txt.' The ransom note is structured as an FAQ with multiple questions. The answers reveal that victims will have to pay a ransom to get assistance from the cybercriminals.
The ransom payment will have to be made using the Bitcoin cryptocurrency. Up to two files such as images and MS Word documents can be sent to the hackers to be decrypted for free. The files must not contain any important data and should not exceed 1MB in size. As for ways to reach the attackers, the note provides three different email addresses - 'factfull0103@airmail.cc,' 'pecunia0318@tutanota.com, and 'pecunia0318@goat.si.'
The full text of the ransom note is:
'Little FAQ:
.1.
Q: Whats Happen?
A: Your files have been encrypted and now have the "factfull" extension. The file structure was not damaged, we did everything possible so that this could not happen..2.
Q: How to recover files?
A: If you wish to decrypt your files you will need to pay in bitcoins..3.
Q: What about guarantees?
A: Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities - nobody will cooperate with us. Its not in our interests.
To check the ability of returning files, you can send to us any 2 files with SIMPLE extensions(jpg,xls,doc, etc… not databases!) and low sizes(max 1 mb), we will decrypt them and send back to you. That is our guarantee..4.
Q: How to contact with you?
A: You can write us to our mailbox: factfull0103@airmail.cc or pecunia0318@tutanota.com or pecunia0318@goat.si.5.
Q: How will the decryption process proceed after payment?
A: After payment we will send to you our scanner-decoder program and detailed instructions for use. With this program you will be able to decrypt all your encrypted files..6.
Q: If I don’t want to pay bad people like you?
A: If you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause only we have the private key. In practice - time is much more valuable than money.:::BEWARE:::
DON'T try to change encrypted files by yourself!
If you will try to use any third party software for restoring your data or antivirus solutions - please make a backup for all encrypted files!
Any changes in encrypted files may entail damage of the private key and, as result, the loss all data.'
SpyHunter Detects & Remove Factfull Ransomware
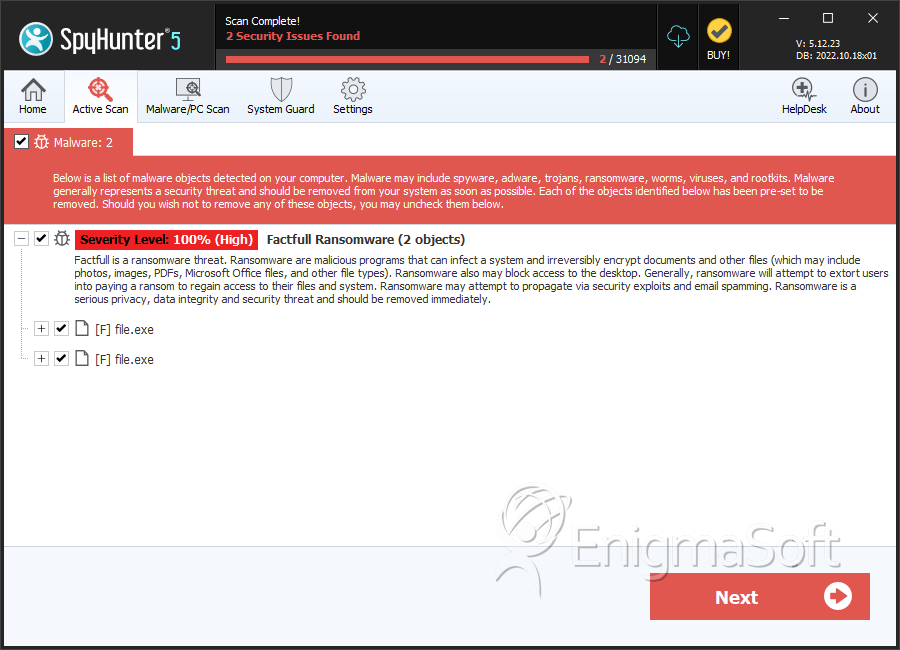
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 041b9a65f3d50134427374dcd8ae4a07 | 3 |
| 2. | file.exe | 1b89064576d13b8bd653af2ee917d954 | 0 |

